Zero transfer scam involves sending small amounts of USDT to your wallet, often so insignificant that they go unnoticed. These attacks utilize intricate methods and crypto address manipulation, making them a challenge to detect even for seasoned crypto users. Therefore, understanding how USDT scams operate and implementing effective protective measures is crucial. To illustrate the complexities and potential dangers, we will investigate a specific case study of this scam, also called the crypto dust attack.
What is a Zero Transfer Scam?
Zero transfer scams involve employing bots, scripts, and automation to exploit human vulnerabilities, leading to confusion, manipulation, and ultimately, financial loss. Our research team delves into a case study of a crypto zero transfer scam that occurred on the Tron Network in September 2023. The scam originated with a seemingly legitimate transfer on the blockchain, triggering a chain of events that resulted in the theft of 34,300 USDT.
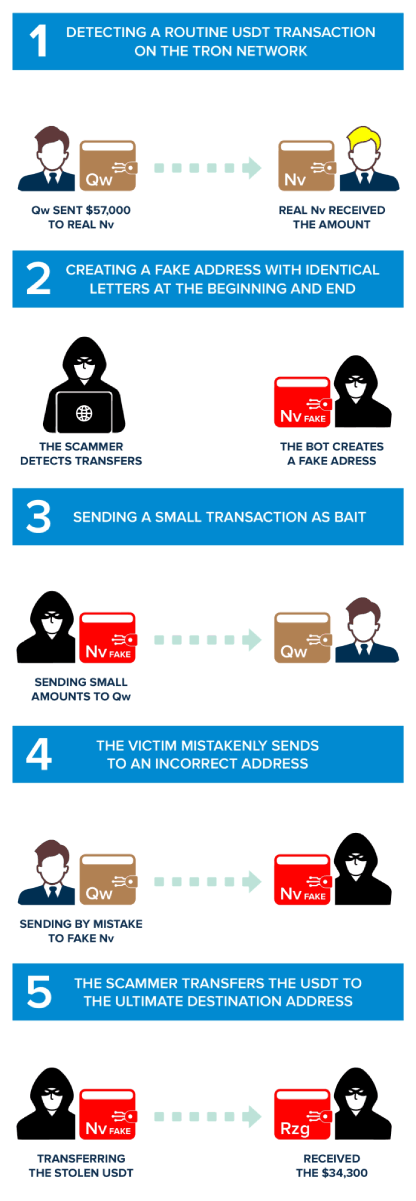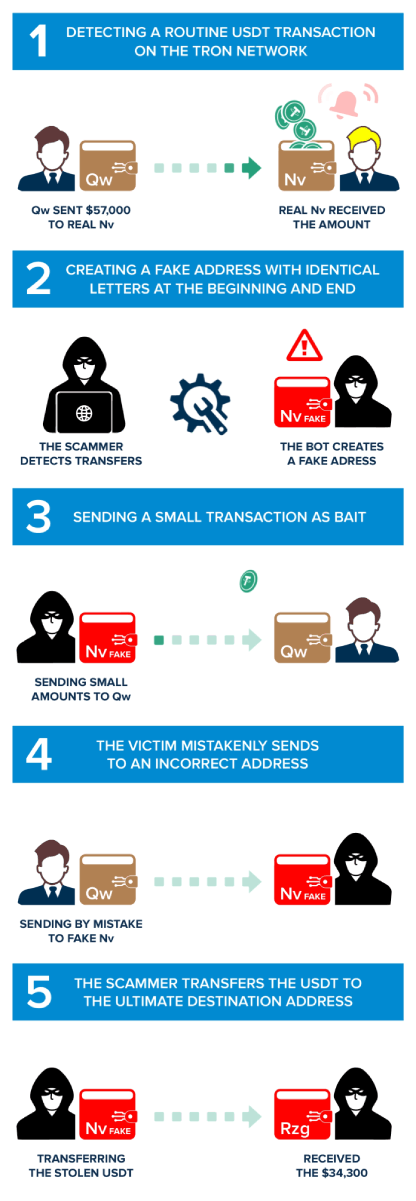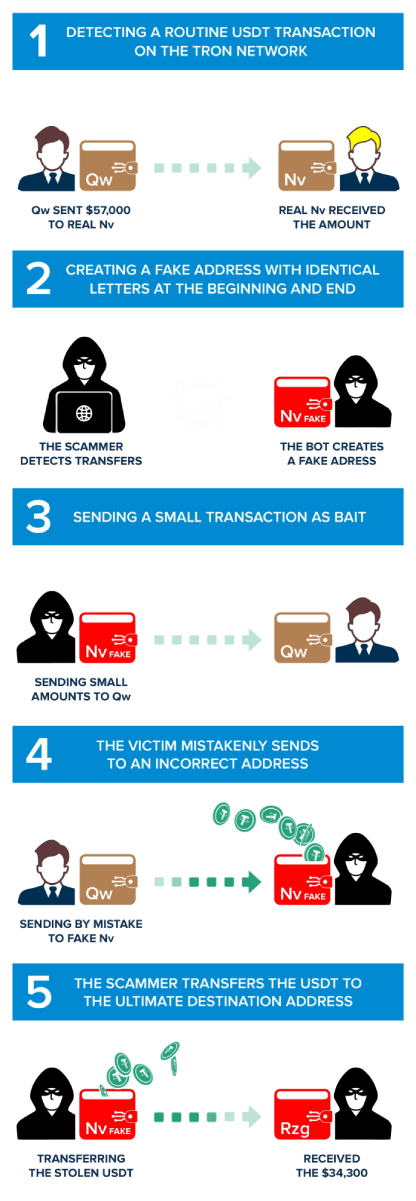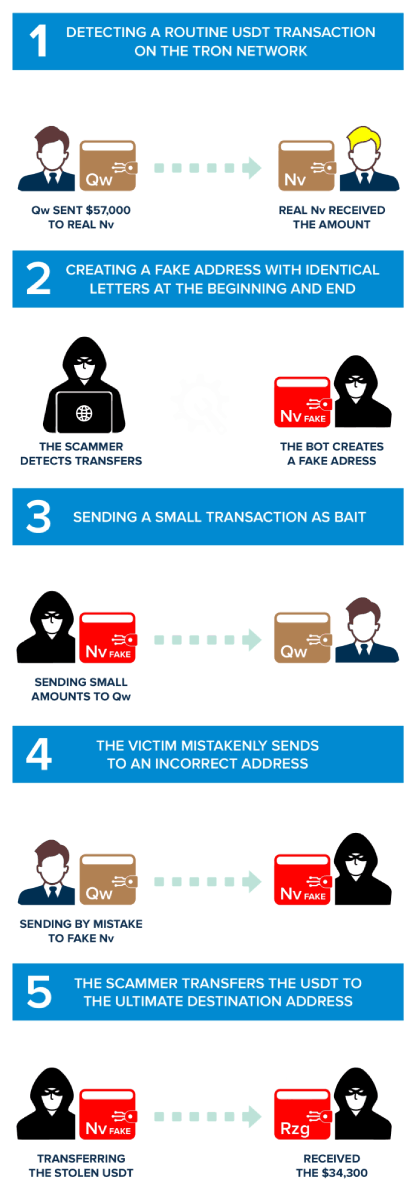
Step 1: Tracking a Seemingly Innocent Transaction
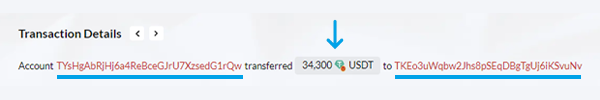
In this particular case study, the victim is TYsHgAbRjHj6a4ReBceGJrU7XzsedG1rQw (referred to as 'Qw' for simplicity, based on the last characters of its wallet address). The scam started on 2023-09-20 at 14:55:03 (UTC).
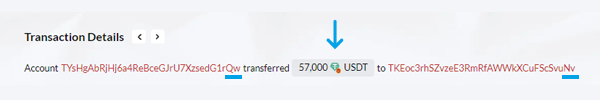
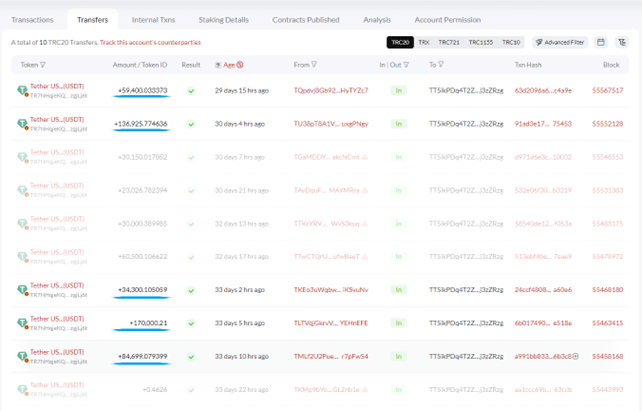
“Qw“executed an honest transaction of 57,000 USDT on the TRC20 network to TKEoc3rhSZvzeE3RmRfAWWkXCuFScSvuNv (referred to as "Real Nv", based on the last two characters of its address).
This transaction appeared innocent, similar to the countless USDT transfers that occur daily on the Tron blockchain. However, this seemingly ordinary transaction laid the foundation for an elaborate and meticulously planned crypto dusting attack. The scammers developed a script that systematically scans the entire Tron blockchain for transactions. After identifying the legitimate transaction between the two parties, the script triggers the next phase of the attack.
Step 2: Creating a Fake Address
Based on the assumption that the owner of the "Qw" address might repeat the USDT transfer to the "real Nv" address, scammers devise a plan to exploit. They craft a newly generated address that closely resembles the legitimate "real Nv" address. This deceptive address, the "fake Nv" address, is designed to trick unsuspecting users into sending funds to the wrong destination. The scammers' plan lies in their ability to create addresses that mimic the real ones with remarkable precision, often differing only by subtle, easily overlooked variations.
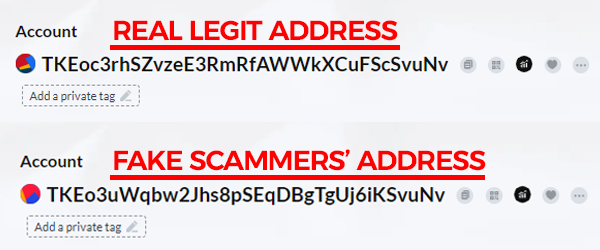
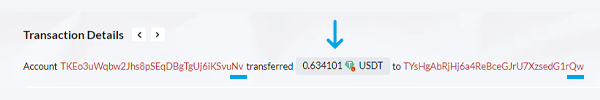
The success of this deception lies in the scammer's ability to create an address, TKEo3uWqbw2Jhs8pSEqDBgTgUj6iKSvuNv, that closely resembles the authentic "real Nv" address. The subtle differences between the two addresses make this stage particularly dangerous. By creating confusion, the scammers aim to manipulate the victim, "Qw" in this instance, into accidentally selecting the fake address instead of the legitimate one during USDT transactions. This misdirection allows the zero transfer scam to proceed, leading the unsuspecting victim to send cryptocurrency to the scammers' created address, known as "fake Nv." Comprehending this process is essential for recognizing the tactics employed in these zero transfer attacks on Tron Network, also called USDT scams.
Step 3: Setting the Crypto Dust for the Zero Transfer Attack
In a calculated move, the scammers execute a strategic maneuver. They initiate a small transaction of USDT, amounting to 0.634101 USDT, from the newly created "fake Nv" address to the victim's "Qw" address. The insignificant sum involved is often deliberately chosen to go unnoticed by the unsuspecting victim. This seemingly harmless transaction subtly manipulates the order of transactions displayed in the victim's wallet, strategically positioning the malicious "fake Nv" address at the top of the transaction history.
By strategically placing the "fake Nv" address at the top of the transaction history, the scammers increase the probability that the victim, "Qw," will accidentally copy and paste the incorrect "fake Nv" address, leading to a crucial error in their subsequent transfer. This deliberate manipulation sets the stage for the victim to fall prey to the scammers' carefully orchestrated deception.
Step 4: Sending Funds to the Fake Address
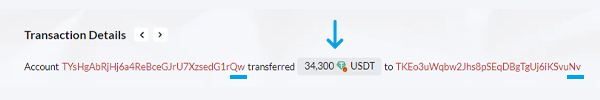
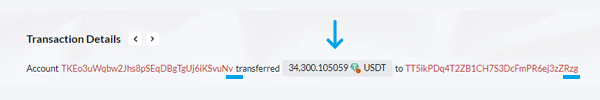
In a crucial moment of misjudgment, the unsuspecting victim, "Qw," falls prey to the scammers' deceptive scheme. Overlooking the crucial middle characters of the receiving address, "Qw" mistakenly identifies the address ending with "Nv" as the genuine "Nv" address. This fatal error leads to the accidental copying of the fake "Nv" address, which is subsequently used for the intended transfer. Tragically, in this instance, "Qw" sent 34,300 USDT to the fake "Nv" address!
The scammers' evil plan is completed with the "Qw's" unintentional transfer of funds to the fake "Nv" address, marking the successful execution of this zero transfer scam. The consequences of this seemingly minor oversight are profound. The USDT intended for the legitimate recipient is sent to the scammers, resulting in a devastating loss of 34,300 USDT. This fact marks the peak of the USDT scam, leaving the victim robbed of their cryptocurrency.
Step 5: An Automation Sends Stolen Funds to the Master Wallet
Upon the successful transfer of USDT from the victim's wallet to the scammers' fake address, the final stage of the address poisoning attack unfolds. The scammers swiftly employ a bot to move the stolen USDT directly to its ultimate destination, the "Master Scammers Wallet" (TT5ikPDq4T2ZB1CH7S3DcFmPR6ej3zZRzg).
A final transfer from the "fake Nv" address sends the 140,00.21 USDT to the "Master Wallet".
This rapid scheme serves as an attempt to launder the illicitly obtained USDT, obscuring its origins and rendering it virtually untraceable and unrecoverable. By transferring the stolen funds to their genuine wallet or an external account, the scammers seek to sever any connection between the misappropriated cryptocurrency and the victim's wallet. In essence, they strive to erase any evidence of their involvement, making it exceedingly difficult for the victim to track the trail of the stolen funds.
In conclusion, 629,888 USDT was stolen in a few days!
Comprehending this final stage is crucial for fully grasping the malicious intent behind crypto dust attacks and the daunting challenges victims face in seeking retribution. Once the USDT is transferred beyond the victim's grasp, the chances of recovering the stolen funds dwindle to zero. Sadly, "Qw" is not the sole victim of this unscrupulous group of scammers. As evident in the transaction history of the "Master Wallet" (zg), five distinct USDT holders have fallen prey to this deceptive scheme, each incurring varying losses, but all misled by the same cunning tactics.
Our PlasBit research team has uncovered the far-reaching implications of this address poisoning attack, which has left crypto users reeling from the devastating consequences. These ruthless scammers have amassed a staggering 629,888 USDT in a matter of days.
Protecting Yourself From The Zero Transfer Scam
In the wake of the detailed exploration of the zero transfer scam, which resulted in the loss of 34,300 USDT, it becomes imperative to delve into comprehensive guidelines to empower cryptocurrency users to shield themselves from falling prey to such deceptive schemes. The sophistication of these attacks necessitates a heightened level of awareness and prudence from users. Below are in-depth strategies to fortify your defenses against the Zero Transfer Scam:
Understanding the Dynamics of Transactions: Cryptocurrency users should cultivate a habit of meticulous transaction scrutiny. Even seemingly insignificant transfers merit careful attention, as attackers exploit the concealment of their activities behind small-scale cryptocurrency movements.
Address Verification as a Crucial Step: Before executing any transaction, engaging in a thorough verification process of cryptocurrency addresses is paramount. Cross-referencing each character of the address with the intended recipient mitigates the risk of falling victim to fraudulent schemes.
Manual Entry Over Copy-Paste Automation: Relying solely on the copy-paste function for cryptocurrency addresses poses a risk. Users are encouraged to manually type addresses or leverage wallet solutions with address verification features, reducing vulnerability to automated manipulations.
Adopting Secure Wallet Solutions: The selection of a secure and reputable digital wallet is pivotal. Opting for wallets with advanced security features, such as real-time alerts for suspicious transactions, provides an additional defense against fraudulent activities.
Leveraging Anti-Scam Tools: Integrating anti-scam services and filters within digital wallets or trading platforms enhances the ability to identify potential scams or dubious addresses. Proactively using these tools strengthens the user's defense against evolving attack strategies.
Continuous Education as a Defensive Strategy: Maintaining a high level of awareness regarding emerging tactics employed by attackers is crucial. Ongoing education empowers users to recognize and respond effectively to the ever-evolving landscape of cryptocurrency scams.
Immediate Reporting of Suspected Scams: Swift action in reporting suspected scam incidents to relevant authorities and involved cryptocurrency platforms is critical. Timely reporting enhances the likelihood of tracing and recovering lost funds.
Prioritizing Anonymity and Privacy: Mindful selection of services and platforms prioritizing user anonymity and privacy is a preventive measure. Limiting the disclosure of personal information minimizes the risk of targeted attacks.
Regular Security Updates: The practice of keeping devices, software, and digital wallets up-to-date is fundamental. Updates often include security enhancements that fortify defenses against the latest attack vectors.
Exploring Multi-Signature Wallets: Consideration of multi-signature wallets, requiring multiple private keys to authorize a transaction, adds a layer of security. This strategic approach ensures that compromising a single key is insufficient for unauthorized access.
Enabling Two-Factor Authentication for Transactions: The activation of two-factor authentication for transactions adds an extra layer of security. This ensures that even if an attacker gains access to a wallet, an additional authentication factor is required to complete a transaction.
Community Engagement for Collective Defense: Active participation in the cryptocurrency community fosters collective awareness. Sharing experiences and insights about emerging scams contributes to a shared defense mechanism against evolving threats.
Users can substantially mitigate the risk of succumbing to scams like the address poisoning attack by assimilating these comprehensive strategies into their cryptocurrency practices. The pillars of awareness, education, and strategic implementation serve as a robust defense in the dynamic landscape of cryptocurrency security.
Lessons Learned and Future Vigilance
Having delved into the intricacies of the zero transfer scam and explored comprehensive strategies to fortify defenses, it is essential to reflect on the lessons learned from this case study and emphasize the ongoing vigilance required in dynamic cryptocurrency security. The case study illuminates the deceptive tactics employed by scammers in executing crypto dusting attacks. The seemingly innocuous transactions are a smokescreen for a meticulously planned attack, exploiting human vulnerabilities and relying on intricate crypto address manipulation. Users must remain aware of the potential dangers behind even the smallest cryptocurrency transfers.
Address Verification as a Cornerstone
The importance of thorough address verification cannot be overstated. The scammers' success, in this case, hinged on their ability to create a fake address closely resembling a legitimate one. Users must adopt a cautious approach, cross-referencing each character of an address before proceeding with transactions. Manual entry and verification provide an additional layer of security against automated manipulations. Additionally, the ecosystem of cryptocurrency scams is ever-evolving, demanding users' commitment to continuous education and adaptability. Staying informed about emerging tactics, sharing experiences within the community, and actively engaging in ongoing education efforts are pivotal components of maintaining a robust defense against evolving threats.
Users must leverage technological safeguards like secure wallets with advanced security features and anti-scam tools. Multi-signature wallets, two-factor authentication, and regular security updates are instrumental in fortifying defenses against a spectrum of attacks, including those as sophisticated as the crypto dusting attack. Finally, this case underscores the irreversible nature of cryptocurrency transactions. Once funds are transferred beyond the victim's control, the chances of recovery diminish significantly. This reality emphasizes the need for proactive measures and cautious behavior to prevent falling victim to scams in the first place.
Conclusion: A Call to Ongoing Vigilance
In conclusion, the zero transfer scam case is a stark reminder of the ever-present risks in the cryptocurrency landscape. Users are urged to internalize lessons, implement proactive protective measures, and remain vigilant in the face of evolving threats. The community's collective efforts and individual commitment to security will contribute to a safer and more resilient cryptocurrency ecosystem. As technology advances and threat vectors evolve, adapting and staying informed becomes paramount. The PlasBit research team urges community members to employ the most effective protective measures to safeguard themselves against address-poisoning attacks. Remain informed, vigilant, and engaged in exploring the crypto world's exciting possibilities while safeguarding your financial well-being. In our research section, we provide additional resources for further exploration and learning about cryptocurrency security. Stay educated and well-prepared to achieve financial freedom.