Crypto users are obvious targets of all sorts of attacks, from social engineering and to fake wallet apps, due to the fact that the hacker knows they simply hold crypto. Let's explore one common case, what is crypto dust attack? It refers to a scenario in which a hacker locates an active address on the blockchain and then sends small amounts of USDT from an address that has the same beginning and ending as one of the user past transactions, that transaction appears on the victim's wallet transactions history, causing the victim to mistakenly copy the hacker address as it looks familiar and send the usdt to the hacker address instead of the correct address. Crypto dusting attacks involve intricate procedures and wallet address manipulations that can bewilder even experienced users. Therefore, you must understand how these frauds work and how to protect yourself. We will examine a specific crypto dust attack case study to shed light on the intricacies and risks.
What Is Dust In Crypto?
The name of this type of scam may sound funny at first, but it comes from a real term in the crypto world. So what is dust in crypto? It refers to extremely small amount of crypto left in your wallet after trades or transactions, usually too small to trade or exchange. Since this scheme uses small amounts of crypto to fool victims, the term "dust" has stuck to it.
The Crypto Dust Attack Unveiled
This type of attack involves a series of steps that the scammer carries out in an automatic and organized manner, using bots, scripts, and automation, exploiting people's cognitive biases, confusing them, manipulating them, and deceiving them. Plasbit's research case study analyzes a scam perpetuated in October 2023 using USDT on the Tron network.
It all started with a legitimate transfer that our researchers encountered on the Tron network that led to a series of events that resulted in a scammer stealing 629,002 USDT in 4 days! By understanding the authenticity of the first transaction, the scammer can weave a deceptive web that entraps the victim in a sequence of events, leading to the loss of their USDT.
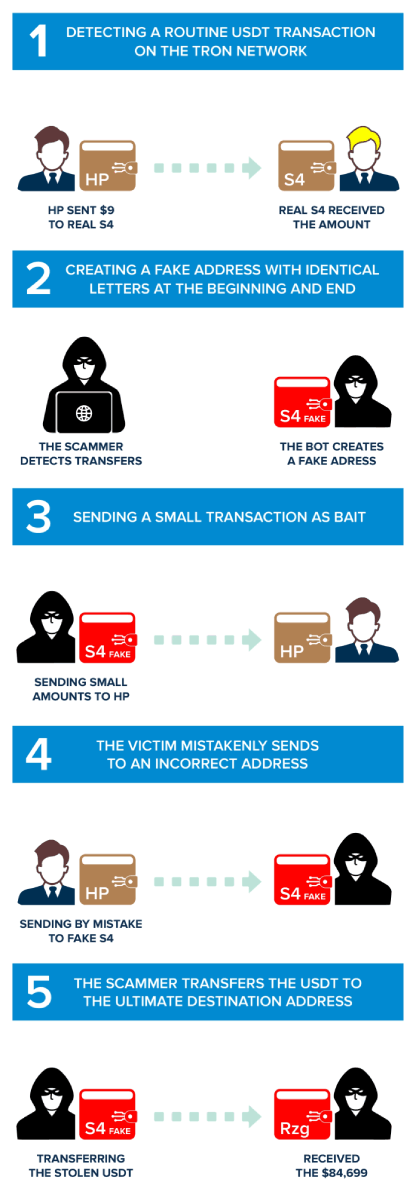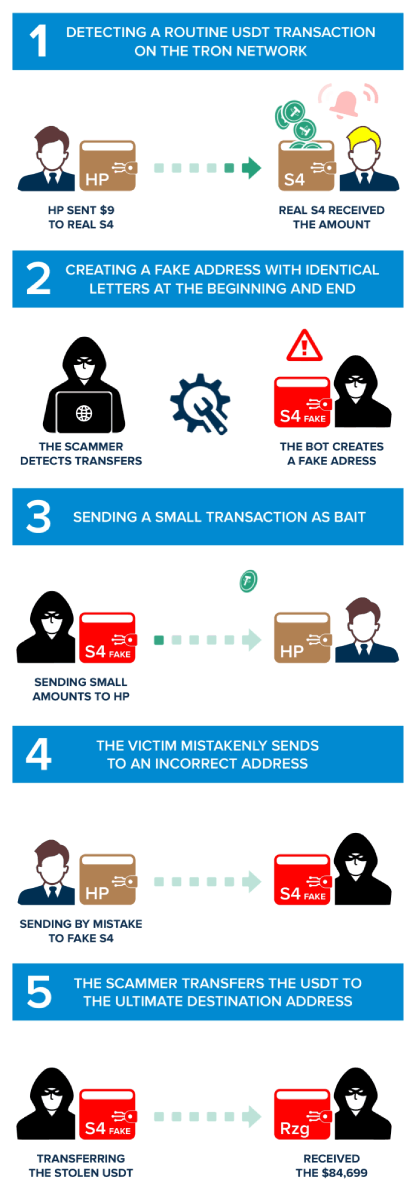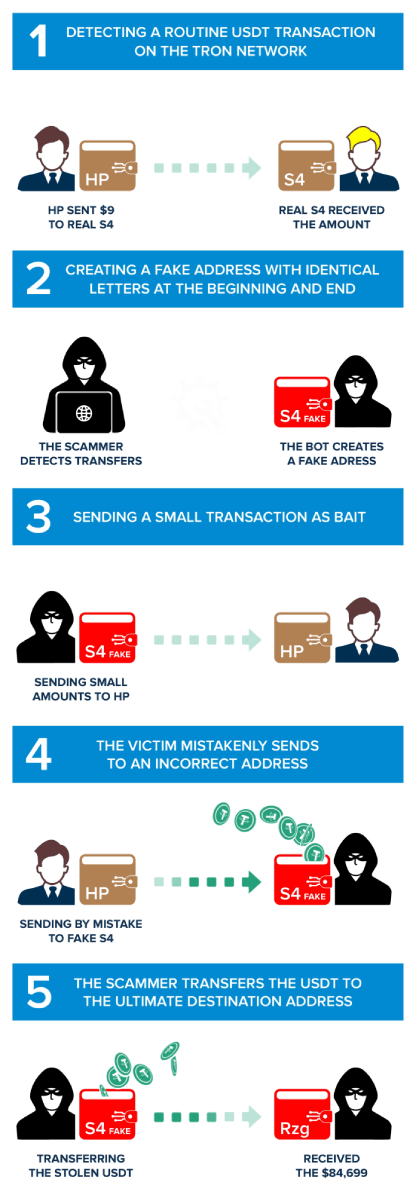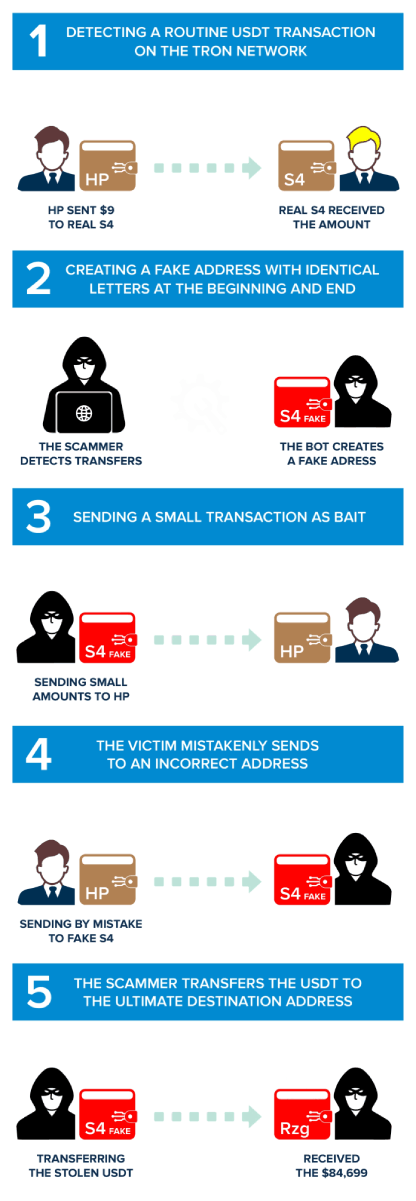
First Phase: Identifying a Legitimate and Routine Transfer on the Tron network
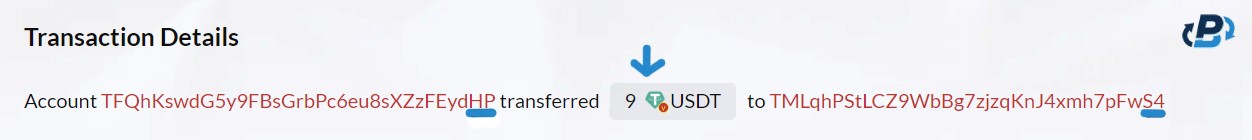
It all starts on 2023-10-08 at 13:05:15 (UTC) with the address TFQhKswdG5y9FBsGrbPc6eu8sXZzFEydHP. (We will refer to this address as “HP,” given the last two characters of the address) The owner of the address “HP” performs a legitimate transfer of 9 USDT on the TRC20 network to address TMLqhPStLCZ9WbBg7zjzqKnJ4xmh7pFwS4. (We will refer to this address as “Real S4”, a name derived from its last two characters and the fact that it is the real address to where the funds are meant to be transferred).
This transaction is genuine, as the user merely engages in standard USDT movement, sending funds for various reasons, such as a purchase, investment, or transfer between personal wallets. At this point, it might seem like an ordinary crypto transaction that occurs millions of times on the Tron network. However, this innocuous transfer sets the stage for the elaborate and cunning scam that follows. The scammer writes a script that automatically scans the entire Tron network for transactions, as in our example. Once it recognizes the transfer between two parties, it initiates the second phase of the attack, creating a misleading fake address.
Second Phase: Creation of a Similar Fake Address
The assumption is that if the owner of the “HP” address sent USDT to the “real S4” address, he will do it again. That is where the scammer cleverly creates a new address designed to mimic the legitimate "S4" address. The resemblance between the “fake” address and the real one is uncanny, often differing by only minor, inconspicuous variations that can easily escape the notice of an unsuspecting user. The scammer's automated scripts create a new address that poses the same first three and the last six characters!
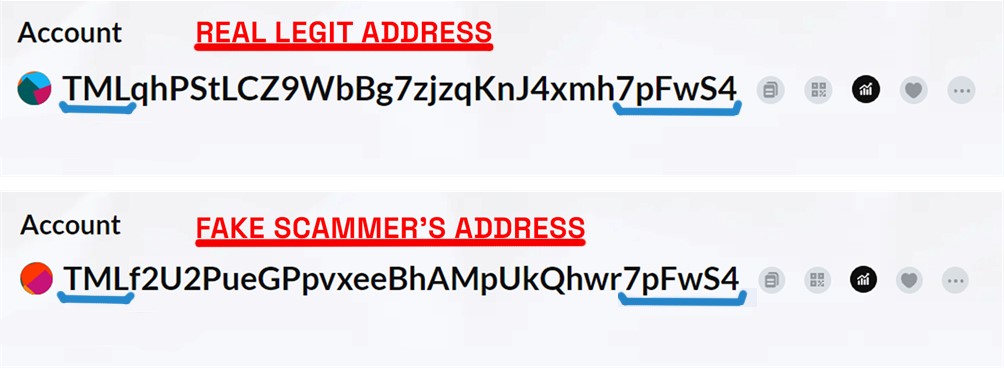
This phase is crucial for the success of the deception. Now, the scammer holds a similar address in this example, TMLf2U2PueGPpvxeeBhAMpUkQhwr7pFwS4, which looks identical to the real "S4" address. It's these subtle differences that make this step particularly dangerous. The scammer's goal is to create enough confusion that the victim, in this case, HP, might inadvertently select the fake address instead of the authentic one in subsequent transactions. This confusion paves the way for the scam to progress, leading to the unsuspecting victim sending USDT to the wrong address: The scammer's fake "S4" address. Understanding this phase is crucial for recognizing the tactics employed in crypto dusting attacks. By being aware of how scammers manipulate wallet addresses and create deceptive imitations, you can take proactive measures to protect your digital assets.
Third Phase: Setting the Bait
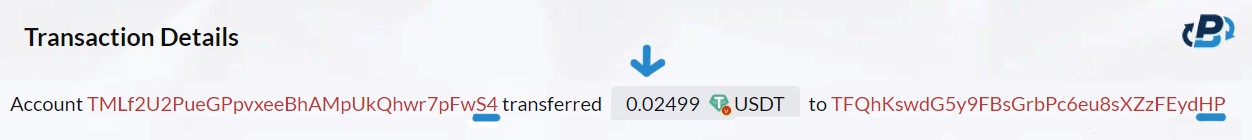
At this phase, the scammer has already noted a legitimate significant transaction from "HP" to the real "S4" address and created a fake address resembling the genuine S4 address. Now, the scammer takes a strategic move. It initiates a small transaction of USDT (0.02499 USDT in this case), basically sending from the new “fake S4" address to the victim “hp” address. The sum involved is negligible, often so tiny that it might appear insignificant to the victim. This small transfer serves a twofold purpose: First, it subtly manipulates the victim's perception of wallet activity, making it seem like the real "S4" address has been sent USDT. Second, it influences the order in which transactions appear on the wallet, prioritizing the new transaction.
By placing the “fake S4" address first on the transaction list, the scammer increases the likelihood that the owner of the address "HP" will wrongly copy and paste the “fake S4” resulting in confusion and sending the USDT to the fake address. Setting the stage for the victim to make a costly mistake in their next transaction. Understanding this step is crucial for recognizing the strategic nature of crypto dust attacks and the lengths scammers go to deceive their victims.
Fourth Phase: The Unintentional Transaction to the Fake Address
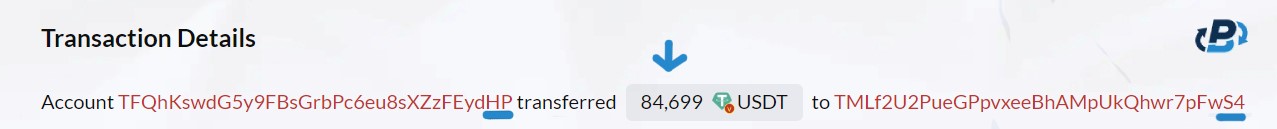
Having set the stage with the small USDT transfer from the "fake S4" address, the scammer awaits the crucial moment for their deception to materialize fully. In this phase, “HP”, the unsuspecting victim, overlooks the middle characters of the receiving address and assumes that the address with the characters “S4” in the end is the real S4 address. Then, he copies the address and pastes it as the recipient address, meaning pasting the “fake S4” address as the actual address. In our case, “HP” transferred 84,699 USDT to the “fake S4" address!
All caused by the cleverly orchestrated confusion initiated by the scammer, making “HP” unwittingly copy the “fake S4" address. This seemingly minor mistake has far-reaching consequences. The USDT intended for the legitimate recipient is sent to the scammer's address, resulting in a loss of 84,699 USDT. Unintentionally sending the USDT to the scammer. This is when the scam comes to fruition, and the scammer successfully acquires the victim's USDT.
Fifth and last Phase: The Scammer's Disappearing Act
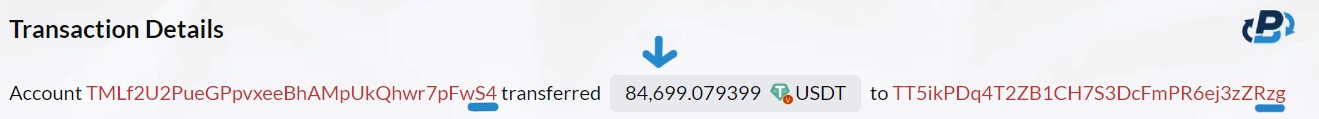
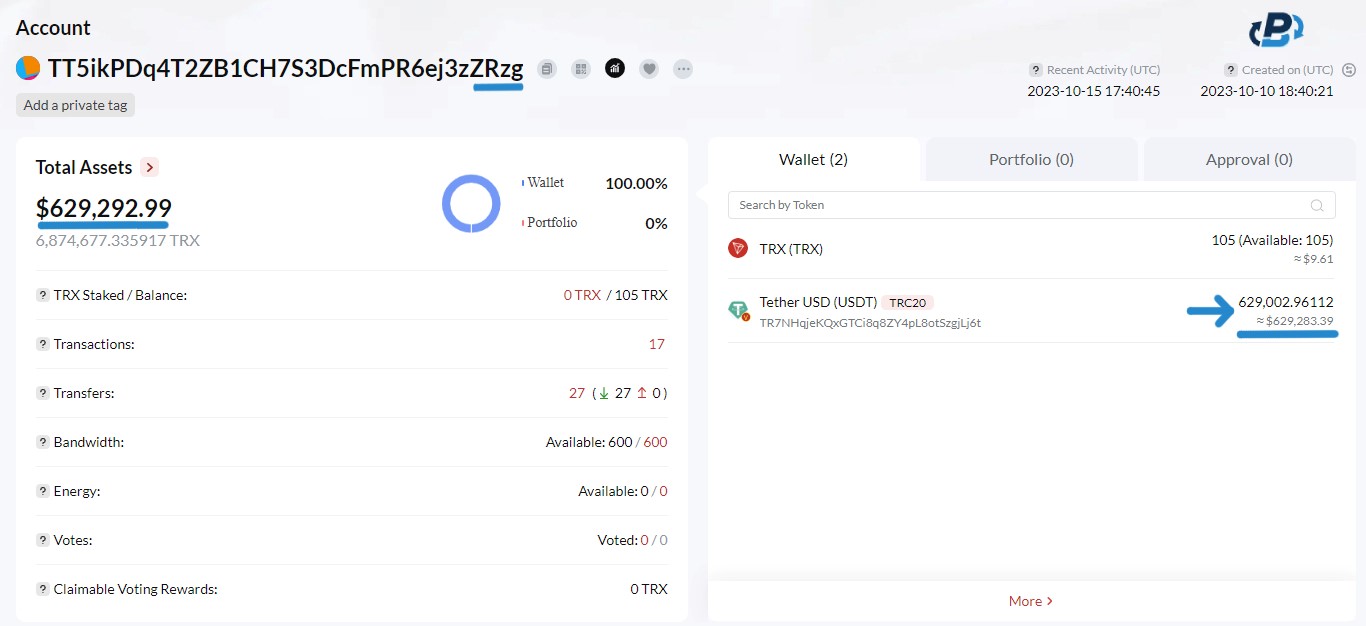
With the successful transfer of USDT from the victim's wallet to the scammer's fake address, the final step of the crypto dust attack unfolds. The scammer uses a bot to quickly act to transfer the USDT directly to the final destination, the “Master Wallet”, (TT5ikPDq4T2ZB1CH7S3DcFmPR6ej3zZRzg). A final transaction from the “fake S4" address sends the 84699 USDT to the “Master Wallet”.
This swift maneuver attempts to launder the stolen cryptocurrency, obscuring its origin and making it challenging to trace or recover. By sending the funds to their real wallet or an external account, the scammer aims to distance the stolen funds from the victim's wallet. Essentially, they seek to erase any evidence of their involvement, making it difficult for the victim to follow the money trail.
In conclusion, 629,002 USDT was stolen in 4 days!
Understanding this last step is critical for recognizing the finality of crypto dust attacks and the challenge they pose for victims seeking redress. Once the cryptocurrency has been transferred out of the victim's reach, it becomes impossible to recover the USDT. Unfortunately, “HP” is not the only victim of this scammer. As you can see in the transaction history image attached, five different USDT owners have fallen for this scam, each losing varying amounts but all deceived in the same manner.
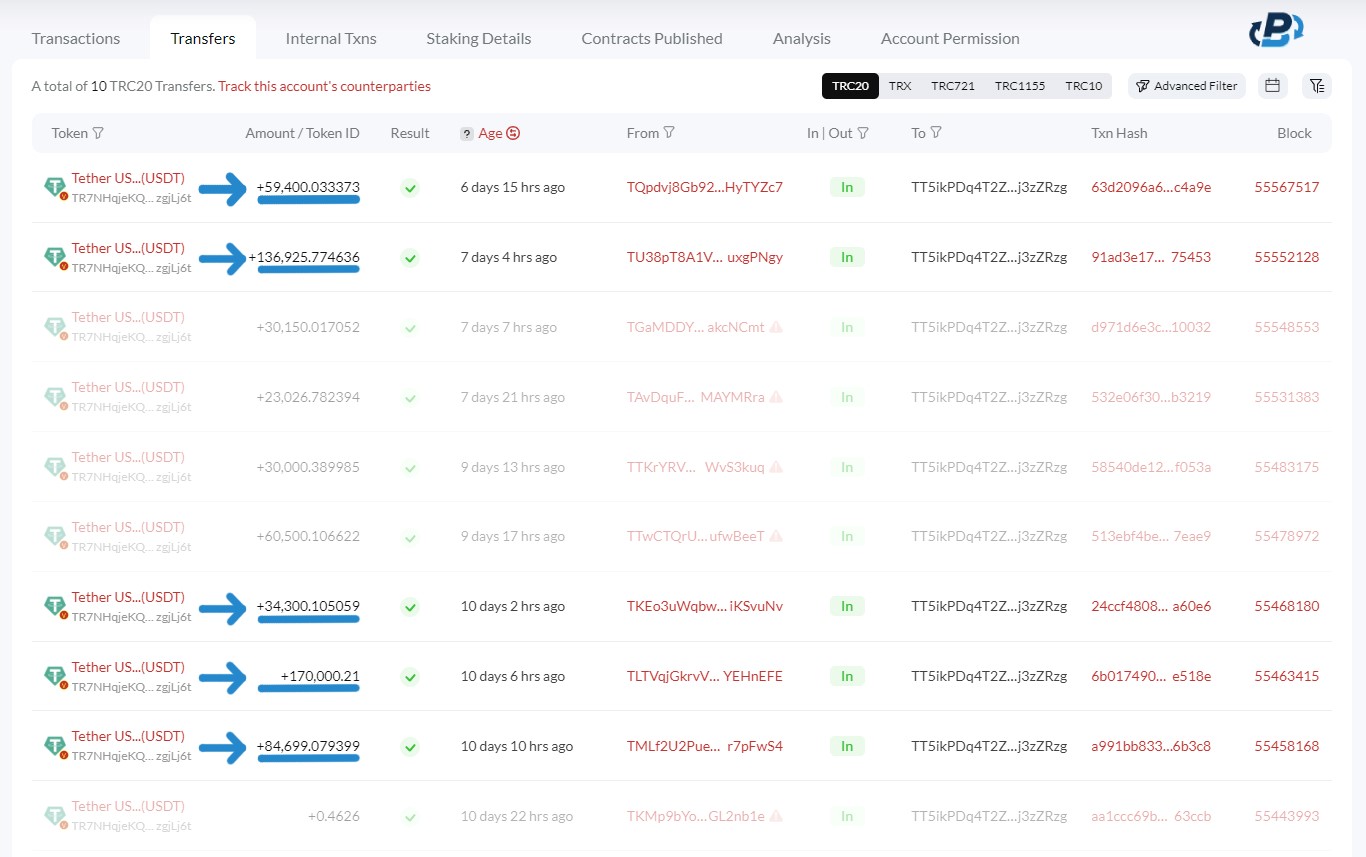
Our PlasBit researchers have discovered that this scam has significant effects, resulting in devastating consequences for crypto owners. As evident in the attached image, this single scammer has managed to steal an astonishing amount of 629,002 USDT in just four days.
How do You Protect Yourself From a Crypto Dust Attack?
Crypto dust attacks are dangerous, but acting proactively can help you prevent the loss of your crypto. You need to know the scammers' favorite targets, how to increase your privacy, endure the boredom of these attempts, and learn all the best practices for safe transactions.
1. Who are the target victims
These attacks primarily target individuals or entities with significant cryptocurrency holdings. These high-value targets are commonly called "whales" in the cryptocurrency world. You may be at a slightly elevated risk if you find yourself in this category, residing in an area with high levels of personal safety and security concerns or political instability. These attacks could be a preliminary step to more nefarious activities, such as phishing, fraud, extortion, or even physical threats.
2. Improving Your Privacy
The cryptocurrency ecosystem has seen significant enhancements in privacy measures over the years. Many modern wallets and exchanges have implemented advanced features to mitigate the risks associated with dusting attacks. These include using HD wallets, identifying dust UTXOs, and integrating with anonymity networks like the Tor Network or VPNs. PlasBit, for example, provides privacy-enhancing wallets and tools that significantly reduce the common concerns related to these scams.
3. Enduring the Annoyance Factor
It's crucial to remember that having crypto dust in your wallet doesn't grant anyone control over your funds. These trace amounts of cryptocurrency are not sufficient to compromise your financial security. Privacy measures and security features integrated into new wallets and exchanges have significantly reduced the risks associated with these attacks.
4. Enhancing Safe Transactions
The first line of defense against crypto dust attacks is awareness. Understanding the warning signs can significantly reduce your vulnerability to such scams. Some common red flags on Tron network to watch out for include:
Unsolicited Transactions: Be cautious of receiving small, unexpected transfers or transactions with negligible amounts of cryptocurrency. These could be the initial stages of a crypto dusting attack.
Fake Addresses: Double-check the recipient's address before initiating any transactions. Scammers often create addresses that closely resemble legitimate ones, with slight variations that can be easy to miss. Moreover, only the first and last alphanumeric characters are visible on the Tron network. Be sure to visit the transaction page and check that the address is correct, not just the first and last characters.
Unusual Activity: Something might be amiss if you notice strange or unfamiliar activity in your wallet or see multiple small transactions. Investigate further.
5. Tips for Safeguarding Your USDT
To enhance your security in the cryptocurrency space, consider these practical tips:
Use Reputable Wallets: Opt for well-established cryptocurrency wallets with robust security features. Research and read reviews before selecting a wallet.
Use two wallets: Using at least two types of wallets is recommended, one secondary for smaller daily transactions and one primary for a store of value. Use the primary wallet store of value only to make transactions to and from your secondary wallet.
Double-Check Addresses: Always verify the recipient's wallet address. Even a single character difference can lead to catastrophic consequences. Check that the entire address is correct.
Regularly Review Wallet Activity: Review your cryptocurrency wallets' transaction history and balances. If you notice any suspicious activity, address it promptly.
Educate Yourself: Stay informed about the latest scams and security threats in the cryptocurrency space. Knowledge is your best defense.
Taking these precautions can significantly reduce the risk of falling victim to a crypto dusting attack.
Is Dust Attack a Phishing Attack?
Since this attack is focused on confusing the victim into entering wrong information for their next transfers, some sharp readers may ask, is dust attack a phishing attack? No, it is not, a dust attack is an attempt to fool the victim into sending transactions to a wrong address that is being controlled by the scammer, while a phishing attack is focused on fooling the victim into revealing sensitive information, like passwords or emails, that would allow the scammers to take control over the victim's assets, and transfer them to the criminals' own accounts.
Crypto Dust Attack: Summing It Up
As we conclude our journey through crypto dust attacks, we must recap the key takeaways and the significance of staying vigilant in cryptocurrencies. Crypto dusting attacks are deceptive schemes that exploit small, seemingly insignificant amounts of cryptocurrency in users' wallets. These attacks involve carefully orchestrated steps, often leading to substantial financial losses for unsuspecting victims. Understanding how these attacks operate and recognizing the red flags is crucial to safeguarding your digital assets. Through the case study, we've seen firsthand how a dust attack can impact an individual. By learning from real-world examples, you can better appreciate the importance of due diligence and cautiousness in your cryptocurrency transactions.
PlasBit research department advises users in the community on the best security practices to protect themselves from falling victim to crypto dusting attacks. By following these measures and staying informed about potential threats, you can minimize the risks associated with cryptocurrency transactions and maintain the security of your assets. Remember that in the ever-evolving ecosystem of cryptocurrencies, awareness, and education are your most potent tools for self-defense. By arming yourself with knowledge and adhering to best practices, you can enjoy the benefits of digital currencies while mitigating the risks. We hope this article has equipped you with the information and tools needed to navigate the world of cryptocurrencies safely and securely. Stay informed, stay cautious, and continue exploring the exciting possibilities of the crypto space while guarding your financial interests. PlasBit provides additional resources for further reading and understanding cryptocurrency security, and our research articles can help you stay well-prepared in your digital financial endeavors.