In the dynamic world of cryptocurrencies, where digital assets flow freely across blockchain networks, a new and insidious threat has emerged: Address poisoning attack. It's a scam in which the scammer targets crypto wallet holders through the blockchain, creates a new address that closely resembles an address the crypto holder has sent crypto before by matching the address's final few characters, tricking them into sending crypto his newly created address as it appears familiar. This article is your key to understanding this covert attack strategy, which recently led to the staggering theft of 136,920 USDT in just one transaction! Address poisoning is a meticulously orchestrated scheme; you need to grasp its intricacies to protect your investments.
The Address Poisoning Attack
The cryptocurrency world is rife with innovation, offering investors and enthusiasts new opportunities daily. However, this space is also a breeding ground for cybercriminals constantly devising sophisticated ways to protect individuals from their valuable digital assets. One such method, address poisoning, has gained notoriety for its effectiveness in siphoning cryptocurrencies, leaving victims puzzled and powerless. We will delve deep into the mechanics of the address poisoning attack, a devious and increasingly prevalent method employed by cybercriminals to exploit unsuspecting cryptocurrency holders. PlasBit research team performed an investigation to study the scam that happened in October 2023, where scammers succeeded in stealing USDT on the Tron network.
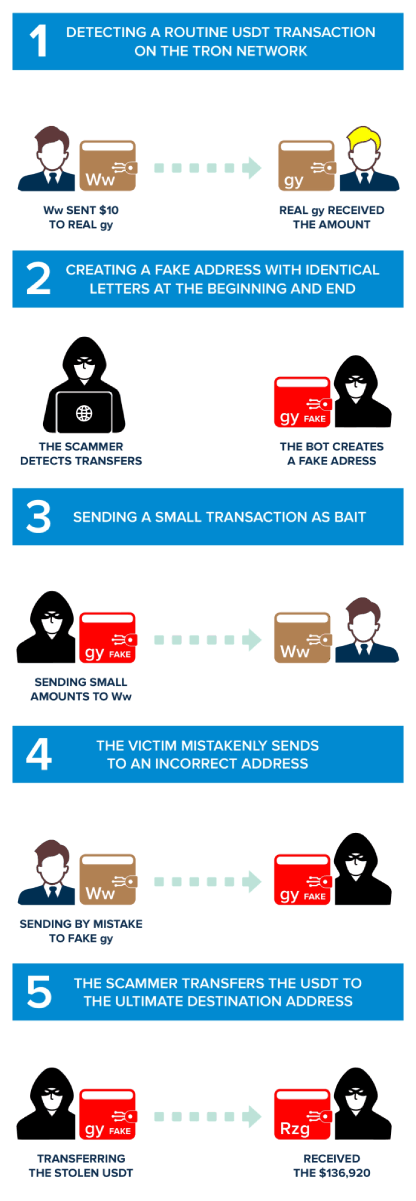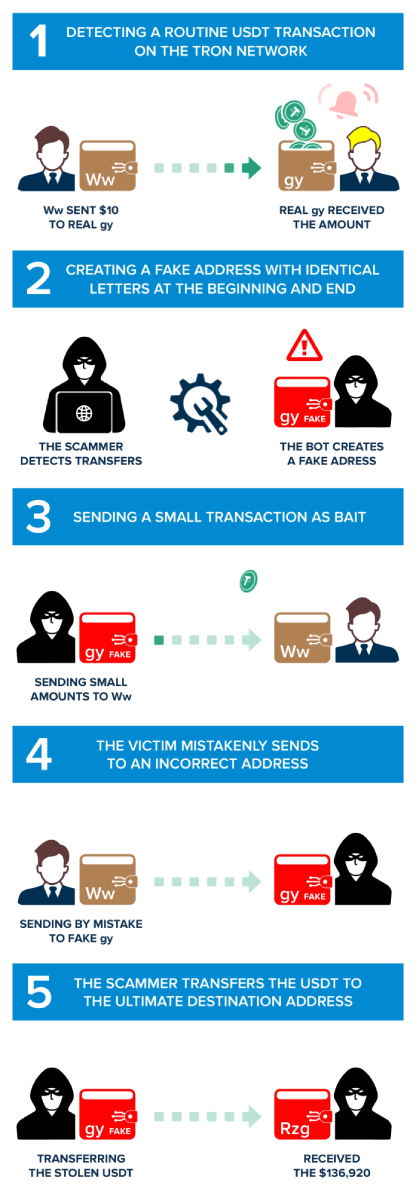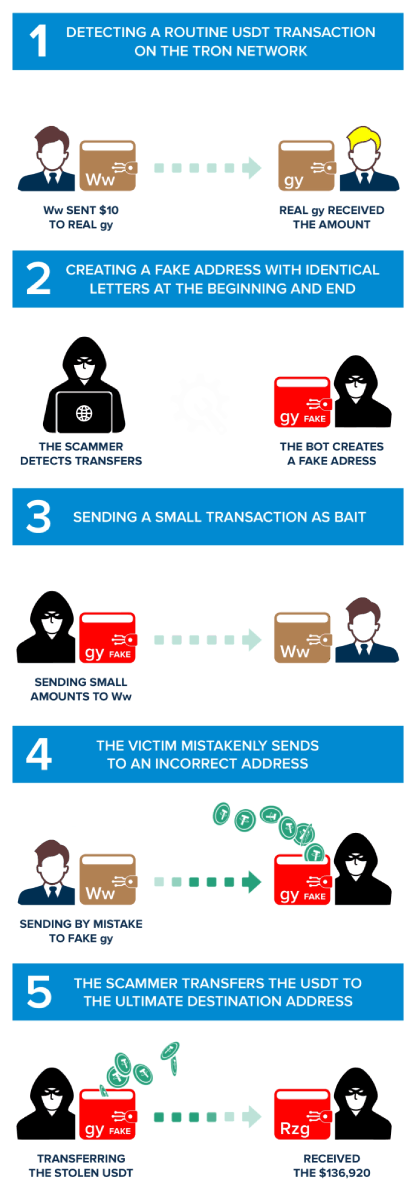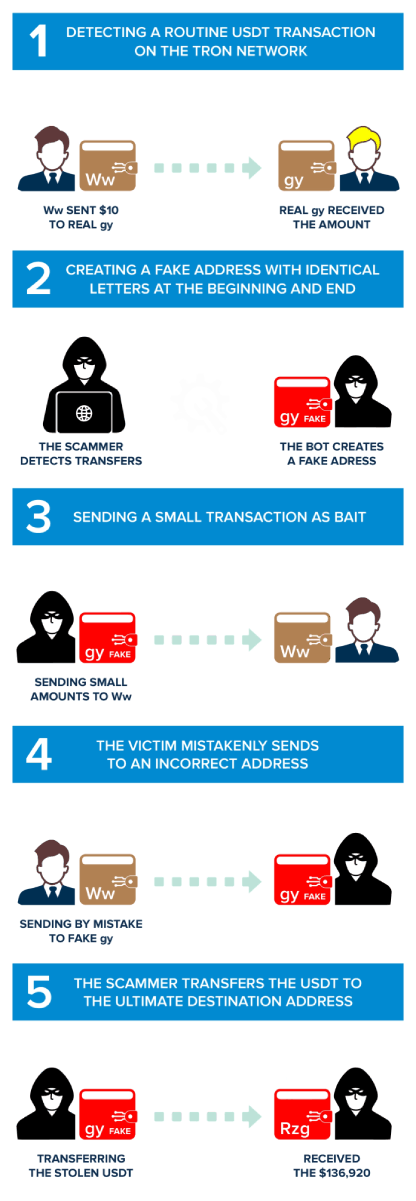
Phase 1: Finding a Regular USDT Transfer on the Tron Network
The journey of an address poisoning attack typically commences with the first phase, Identifying a wallet's high net worth. Attackers seek out wallets with significant transaction activity, indicating a large cryptocurrency holding.
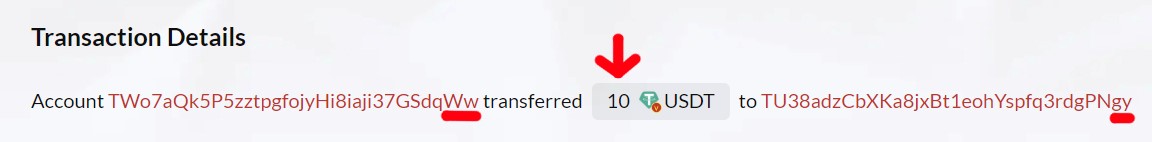
In our example, the victim wallet is TWo7aQk5P5zztpgfojyHi8iaji37GSdqWw (We will refer to this address as "Ww," given the last two characters). "Ww" wallet holds a substantial amount of USDT and has become a prime target for address poisoning due to the potentially notable loot they promise. The scam began on 2023-10-08 at 13:05:15 (UTC) as the address "Ww" owner performed a legitimate transfer of 10 USDT on the TRC20 network to the address TU38adzCbXKa8jxBt1eohYspfq3rdgPNgy. (We will refer to this address a s "Real gy").
Phase 2: The Scammer Creates a Fake Similar Address
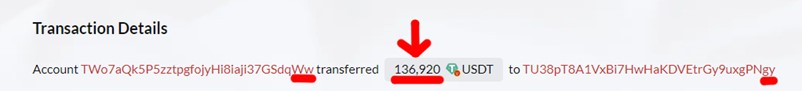
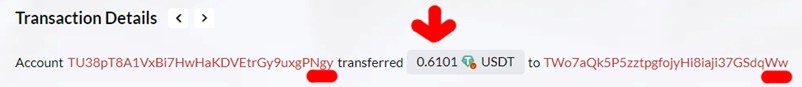
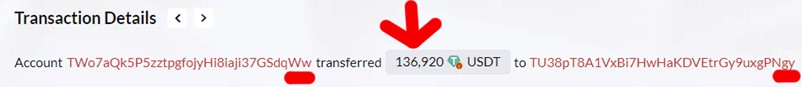
In the second phase of the address poisoning attack, the scammers set their devious plan into motion by creating a mimic wallet's address. These fake wallets are a crucial component of the attack, as they are designed to closely resemble the target's wallet, trying to confuse the victim. It is essential for crypto users to carefully verify the entire wallet address before sending money. Simply copying the address from the previous transaction without double-checking it is not a recommended practice. The scammer has noticed that the target wallet 'Ww' has carried out legitimate transactions with the address "Real gy" TU38adzCbXKa8jxBt1eohYspfq3rdgPNgy, so he creates a similar wallet in this case: TU38pT8A1VxBi7HwHaKDVEtrGy9uxgPNgy, from now called "Fake gy".
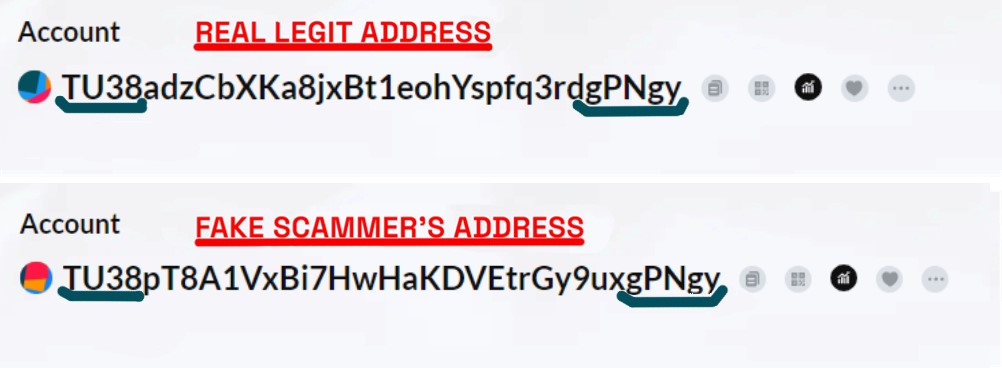
This meant to appear in the victim's transaction history and pretend to be the legitimate address he usually interacts with.
Phase 3: Active Attack Phase - Sending Small Trap Transactions
This is where the attackers initiate small transactions to bait the victim by causing the transactions to appear on top in the wallet transaction history list. The attacker "fake gy" is strategic in its approach. It sends relatively small amounts of cryptocurrency to the victim's wallet, often in a manner that appears innocuous.
In our case, this is the transaction, "fake gy" sent 0,6101 USDT to "Ww".
The scammer creates the ideal situation for the unsuspecting victim to make a mistake: He makes his “fake gy” address appear at the top of the recent transactions list in the victim's wallet, this way, the victim is likely to copy the address from the last received transaction in order to make another transfer.
Phase 4: The Target Wallet's Mistaken Transaction
This is the phase in which a pivotal moment exists in the attacker's scheme. At this stage, the attacker engineers a scenario in which the target wallet mistakenly sends cryptocurrency to one of the attacker's mimic wallets.
This mistake sets the stage for the attacker to stealthe victim's digital assets. The attacker worked to manipulate the victim's perception of the blockchain, creating a web of deceit that led to this critical point. Having interacted with the fake wallet through the bait transactions, the victim is more likely to overlook discrepancies or mistakes, believing they are engaging with their authentic wallet. As a result of the orchestrated confusion and manipulation, the victim inadvertently initiates a transaction to the mimic wallet, believing it to be a routine or legitimate transaction with their own wallet. This action plays directly into the hands of the attackers.
Our study shows that "Ww" copied the "fake gy" address from its transaction history without double-checking the whole address. In fact, in this transaction, "Ww" lost 136,920 USDT, sending them to the "fake gy" wallet on the Tron network.
Phase 5: Transferring Stolen Cryptocurrency to the Main Account
In the fifth phase of the address poisoning attack, the cybercriminals have successfully lured the victim into sending cryptocurrency to one of their mimic wallets. With the victim's cryptocurrency now residing in the mimic wallet, the attackers seize the moment and act swiftly to make the transfer.
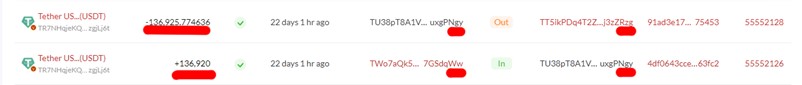
An automated bot has access to the mimic wallet and initiates the transfer of the stolen funds to their primary cryptocurrency account in a few seconds. In our case, a script made a transaction and sent the funds instantaneity from the "fake gy" to the main wallet of the scammer TT5ikPDq4T2ZB1CH7S3DcFmPR6ej3zZRzg, introducing a new layer of deception as the attackers work to create a convoluted and intricate web of transactions to cover their tracks.
Their aim is to render any attempts at tracking the stolen cryptocurrency futile, making it nearly impossible for investigators or the victim to discern the path of the stolen funds. We can also see that the scammer's main wallet has already stolen funds in excess of 629,000 USDT!
Erasing All Traces of the Attack
This phase of the address poisoning attack represents the final and most critical step in the attacker's quest to cover their tracks and eliminate any evidence of malicious activity. The attackers deploy sophisticated techniques to hide their actions, making it exceedingly challenging for the victim to trace the stolen funds or seek redress.
As the stolen cryptocurrency sits safely in the attacker's primary account, the need to erase all attack traces becomes paramount. To achieve this, the attackers employ the following techniques:
Tumbling Services: Attackers may use cryptocurrency tumbling or mixing services, which jumble the stolen funds with those of other users. This process obfuscates the transaction trail, making it virtually impossible to trace the funds back to the source.
Shapeshifting: Shapeshifting services allow attackers to convert the stolen cryptocurrency into other digital assets, often across multiple blockchains. This conversion further complicates tracking efforts as the funds take on new forms.
Splitting Funds: The attackers might split the stolen funds into smaller amounts and send them through an intricate network of wallets and accounts, further obscuring their origin.
Crossing International Borders: The attackers create jurisdictional challenges that hinder legal pursuit by transferring the stolen funds across international borders and between different exchanges and wallets.
Layered Anonymity: Attackers may also use anonymity-focused cryptocurrencies or privacy coins in their transactions, adding another layer of complexity to the tracking process.
The ultimate goal of the scammer is to achieve a level of anonymity that effectively shields the attackers from detection. By combining the above techniques, they ensure that their identity and the location of the stolen funds remain concealed. As this phase concludes, the address poisoning attack effectively vanishes into the shadows, leaving the victim with little recourse for tracing or recovering the stolen cryptocurrency. The attackers have executed a comprehensive plan, leveraging psychological manipulation, mimicry, and advanced blockchain techniques to divert and secure their ill-gotten gains. For the victim, the aftermath of an address poisoning attack is marked by frustration and powerlessness. Tracking the stolen funds, given the layers of obfuscation employed by the attackers, is arduous and often fruitless. Can you trace the owner of an address? This represents one of the biggest challenges in cryptocurrency security: the difficulty in recovering stolen assets and bringing cybercriminals to justice.
Common Characteristics of Wallet Poisoning Attacks
Address poisoning attackers utilize various tools and methods to scour the blockchain for wallets with high transaction volumes. These can include publicly available information on block explorers, data analytics, and tracing techniques. Once a target is identified, the attacker's work begins in earnest.
Target Profile: The targets of these attacks are often individuals or entities known to possess a significant amount of USDT. Typical targets are high-profile cryptocurrency investors, businesses, or wallets linked to exchanges. Attackers prefer wallets with extensive transaction histories as they provide more opportunities for manipulation.
Why Target Big Wallets: Address poisoning attackers go after substantial wallets because of the significant financial rewards they offer. The more substantial the wallet, the higher the potential for a lucrative heist. As the saying goes, "follow the money," and cybercriminals know that big wallets hold the most treasure. By targeting this kind of users, they can steal millions in cryptocurrencies, and a few people went to jail for crypto.
Case in Point: Consider a hypothetical scenario where an attacker identifies a wallet holding vast reserves of various digital assets. The allure of such a wallet lies in the potential to execute an address poisoning attack and redirect a substantial amount of cryptocurrency away from the victim.
Attacker Techniques
To be successful in the scam, attackers use various techniques:
Wallet Characters: Attackers carefully create a wallet with the same alpha-numeric characters at the beginning and end to replicate the target wallet's user address. This design imitation is intended to fool the victim into believing they interact with their legitimate wallet. The scammer created an automated script to create a new address with the same first three and the last six characters of the wallets in the wallet target's transactions.
Transaction History: The mimic wallet's transaction history could be manipulated to match the target wallet as closely as possible. This could also include replicating previous transactions and balances to create a convincing fake address.
Creating a Mirage: This mimic wallet construction aims to create a mirage that obscures the attacker's true intentions. By creating a similar address, the attackers intend to divert the victim's attention and make it challenging for them to distinguish the genuine wallet from the fake.
The Psychological Impact: The mimic address's effectiveness hinges on its psychological impact on the victim. When the victim believes they are sending money to their usual wallet, they are less likely to scrutinize transactions and activities as closely as they would with a suspicious wallet. This psychological manipulation is a fundamental aspect of the attack.
Function and Purpose of Bait Transactions
These bait transactions serve several crucial purposes:
Gaining Access: The small bait transactions allow attackers to insert themselves into the victim's transaction history, connecting the mimic and target wallets.
Earning Trust: By initially sending relatively small amounts, the attackers aim to build trust. The victim may see these transactions as harmless and not initially suspect malicious intent, probably thinking of them as a reward or cashback.
Psychological Manipulation: Bait transactions are a vital component of psychological manipulation. They lull the victim into a sense of security, making them less likely to scrutinize future transactions, mainly if they originate from a familiar source.
Confusing the Trail: The purpose of these bait transactions is to complicate the transaction history and introduce confusion. By mingling the mimic wallet's transactions with those of the target wallet, it becomes more challenging for the victim to distinguish between the two. This convolution plays a pivotal role in the success of the address poisoning attack.
Timing and Frequency: The attackers carefully time and space out these bait transactions. They may execute them at intervals, minimizing suspicion, or right after a legit transaction of the target wallet. The attackers exploit the victim's sense of familiarity and trust by creating a consistent interaction pattern between the mimic and target wallets.
The active attack phase is a pivotal step in the address poisoning process. It bridges the mimic and target wallets, connecting the two in the victim's transaction history. As this phase unfolds, the attackers are one step closer to their ultimate goal: diverting the victim's cryptocurrency without detection.
How to Protect Yourself From Address Poisoning Attacks
In the wake of our in-depth exploration of the address poisoning attack, it becomes evident that safeguarding your cryptocurrency holdings is paramount. To protect yourself from such malicious tactics, you must understand the measures and best practices to help you defend against address poisoning and similar threats. We provide a comprehensive guide on bolstering defenses and securing digital assets.
Know Your Adversaries: Understanding the potential attackers is crucial. Be aware of who might be interested in your assets and the tactics they employ. This awareness will enable you to defend against their strategies proactively.
Choose Reputable Wallets: Avoid using unverified or obscure wallet providers. Research and opt for well-established, reputable cryptocurrency wallets known for their security features: use wallets like PlasBit to prioritize security, privacy, and interoperability.
Maintain Discretion: Limit the exposure of your cryptocurrency holdings and financial information. The less information you share about your assets, the lower the likelihood of being targeted.
Use Anonymity Features: Consider using privacy-focused cryptocurrencies with advanced anonymity features to protect your financial identity.
Multisignature Wallets: Utilize multisignature wallets that require multiple private keys to authorize transactions. This adds an extra layer of security against unauthorized transfers.
Vigilance: Stay vigilant and trust your instincts. If a transaction appears suspicious or unfamiliar, it's better to err on the side of caution and not engage with it.
Double-check addresses: Always verify the details of a transaction before confirming it. Double-check the recipient's address to ensure it matches the intended recipient.
Keep Software Updated: Regularly update your wallet software to benefit from security enhancements and bug fixes.
Two-Factor Authentication (2FA): Enable 2FA for your online accounts, especially those associated with cryptocurrency exchanges and wallets.
Educate Yourself: Continuously educate yourself about emerging threats and security best practices in cryptocurrency.
Seek Legal Recourse: In case of an attack, consult legal experts and law enforcement to explore potential avenues for recovering stolen assets or pursuing the perpetrators.
Report Incidents: If you suspect you are a victim of an address poisoning attack or any cryptocurrency-related crime, promptly report it to the relevant authorities or platforms.
Cooperate with Investigations: Cooperate with law enforcement and investigative agencies to increase the chances of identifying and apprehending the attackers.
Other Common Scams in the Crypto Space
We will mention some other common crypto scams, shedding light on the tactics used and providing guidance on how to protect yourself from falling victim to these fraudulent schemes.
Phishing Scams: Phishing scams are one of the oldest tricks in the book, but they continue to be effective. Scammers create fake websites, emails, or social media profiles that closely mimic legitimate cryptocurrency platforms or services. They then lure users into sharing sensitive information, such as private keys or login credentials, which the scammers use to access and steal their digital assets.
Ponzi Schemes: Ponzi schemes promise high, guaranteed returns on investments in cryptocurrency. These scams pay out early investors using the funds of new investors, creating the illusion of profitability. However, when the scheme eventually collapses, many participants lose their entire investment.
Fake ICOs (Initial Coin Offerings): Scammers often create fake ICOs, complete with a whitepaper and a compelling narrative, to entice investors to buy non-existent tokens. Once they've collected a substantial amount of cryptocurrency, the scammers disappear.
Pump and Dump Schemes: In pump and dump schemes, manipulators artificially inflate the price of a low-value cryptocurrency by spreading false or exaggerated information. Unsuspecting investors rush in to buy, hoping to profit, only to have the manipulators "dump" their assets at inflated prices, causing the value to plummet.
Exchange Hacks: Cryptocurrency exchanges can be prime targets for hackers. When an exchange is breached, users' funds can be stolen. To mitigate this risk, use reputable exchanges with a strong security track record, enable two-factor authentication (2FA), and store your assets in secure wallets rather than leaving them on the exchange.
Social Engineering: Scammers often employ social engineering tactics to manipulate individuals into revealing sensitive information. They may impersonate a friend, family member, or support representative and request access to your cryptocurrency holdings.
The crypto world is filled with opportunities and risks. While the potential for financial gain is substantial, so is the risk of falling victim to scams. Understanding the common crypto scams and taking proactive measures to protect your assets is crucial. Always exercise caution, verify the authenticity of the entities you deal with, and stay informed about the latest scam tactics.
We hope that in this analysis of PlasBit's research section, you have understood what an address poisoning attack is. You must act and inform yourself proactively to know how to behave effectively when attacked. This guide empowers you with the knowledge and strategies to protect your cryptocurrency assets and guard against address poisoning attack and similar threats. By implementing these measures and staying informed about the evolving landscape of cryptocurrency security, you can significantly reduce your vulnerability to such malicious tactics. Your digital assets deserve the utmost protection, and this chapter provides the tools to achieve just that.