Crypto dusting attack refers to small amounts of cryptocurrency sent to your wallet, often so tiny that they appear unimportant. This attack involves complex techniques and the manipulation of crypto addresses, which can confuse even experienced users. Therefore, you must comprehend how these USDT scams work and how to protect yourself. We will examine a specific crypto dust attack case study to emphasize the complexities and threats.
Crypto Dusting Attack: USDT Scams on Tron Network
This kind of USDT scam involves a series of steps that the scammers carry out in a computerized and systematic way, using bots, scripts, and automation, exploiting people's mental predispositions, disorienting, manipulating, and tricking them. Our team research case study analyzes a crypto dusting attack on Tron Network, perpetuated in September 2023. It all began with an honest transfer on the Tron network, leading to a series of events that resulted in scammers stealing 170,000 USDT! By understanding the authenticity of the first transaction, the scammers can weave a dishonest plan that entraps the victim in a series of circumstances, leading to the loss of their USDT.
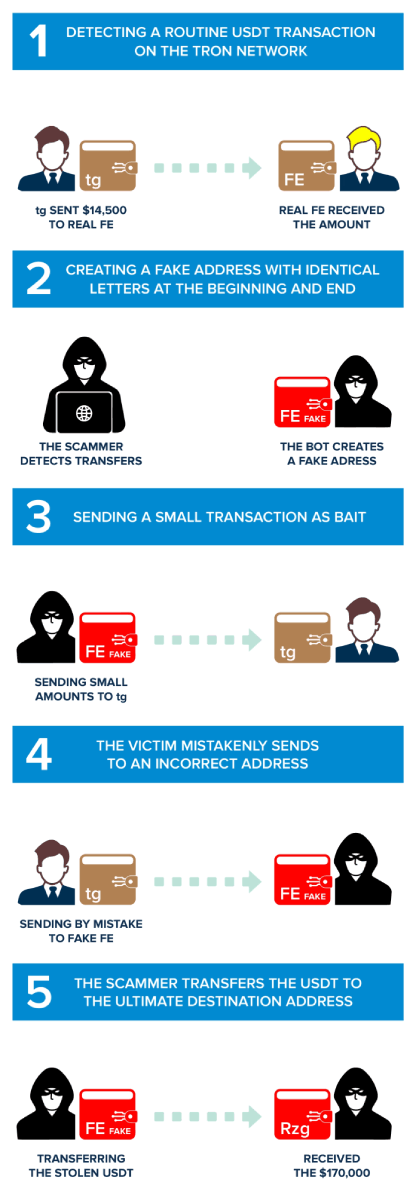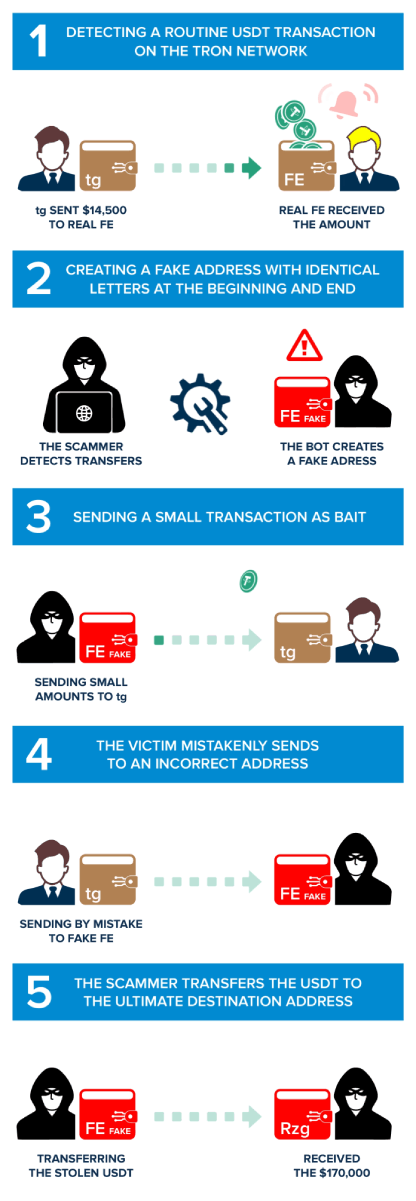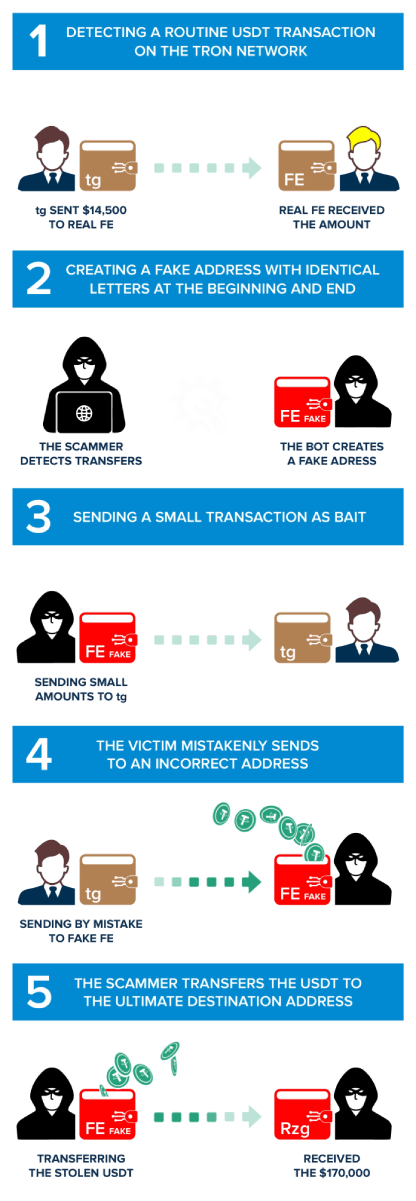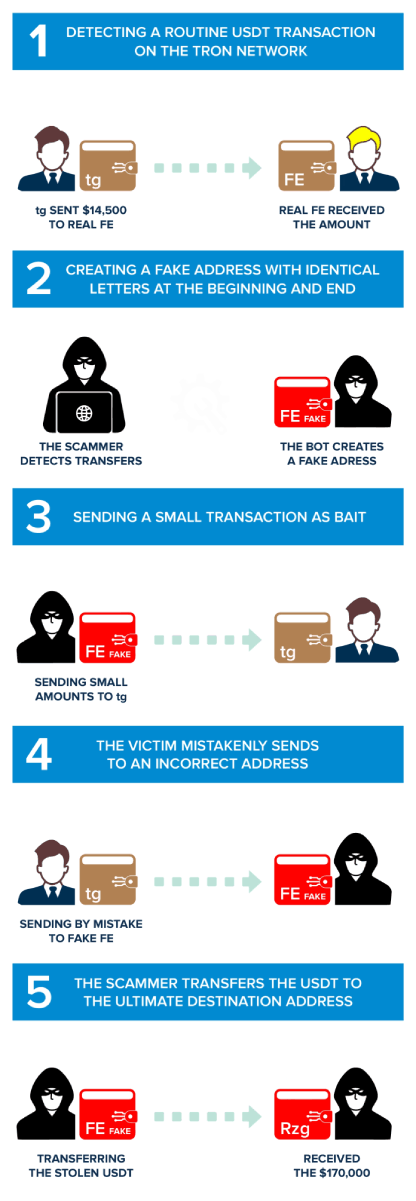
First Step: Tracking a Legitimate Transfer on the Tron network
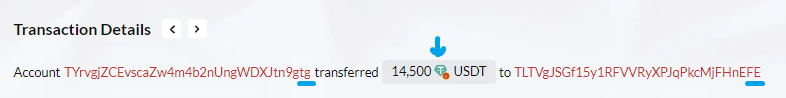
It all starts on 2023-09-28 at 07:00:12 (UTC), and the victim is TYrvgjZCEvscaZw4m4b2nUngWDXJtn9gtg (We will refer to this address as "tg" given the last two characters of the address).
The owner of the address "tg" performs a legitimate transfer of 14,500 USDT on the TRC20 network to address TLTVgJSGf15y1RFVVRyXPJqPkcMjFHnEFE (We will refer to this address as "Real FE," a name derived from its last two characters and the fact that this is the real address to which 'tg' wanted to send the funds).
This transaction is honest, as the user merely engages in a standard USDT transfer, sending funds for various reasons, such as a purchase, investment, or transfer between personal wallets. At this point, it might seem like an everyday crypto transaction that occurs millions of times on the Tron blockchain. However, this benign transaction sets the premise for the elaborate and cunning crypto dust attack that follows. The scammers write a script that automatically scans the whole Tron blockchain for transactions, as in our example. Once it identifies the transfer between two parties, It initiates the second phase of the attack, creating misleading a fake address.
Second Step: Creation of a Similar Counterfeit Address
The hypothesis is that if the owner of the "tg" address sent USDT to the "real FE" address, he will do it again. At this point, scammers create a newly generated address designed to imitate the legitimate “real FE" address. The similarity between the "fake FE" address and the real one is impressive, often differing by only minor, hidden variations that can easily fool an inexperienced user. The scammers' bot creates a new address with the same first three and the last six characters!
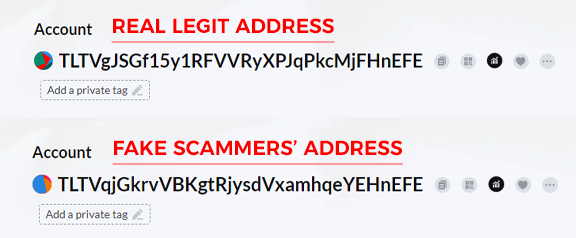
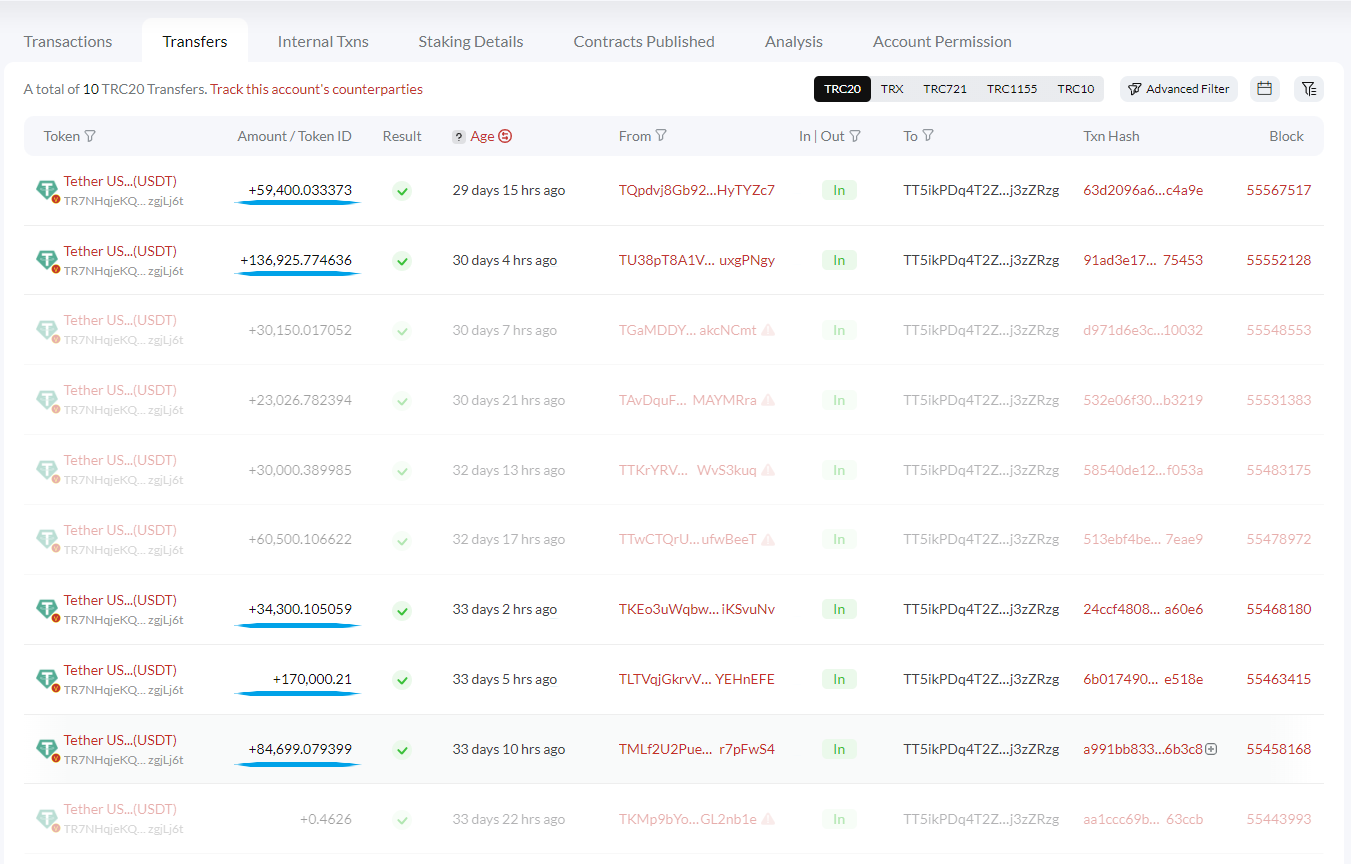
This phase is crucial for the success of the deception. The scammer holds a similar address, TLTVqjGkrvVBKgtRjysdVxamhqeYEHnEFE, which looks identical to the "real FE" address. It's these subtle dissimilarities that make this step particularly risky. Scammers try to make things confusing so that the victim, "Real FE" in this case, might accidentally choose the wrong (fake) address instead of the real one during USDT transfers. This confusion allows the crypto dusting attack to continue, making the unsuspecting victim send crypto to the fake address created by the scammers, known as "fake FE." Understanding this process is crucial to recognize the tactics used in USDT scams on the Tron Network. Knowing how scammers use address poisoning attacks to manipulate wallets and create deceptive scams helps you protect your crypto assets proactively.
Third Step: Setting the Crypto Dust
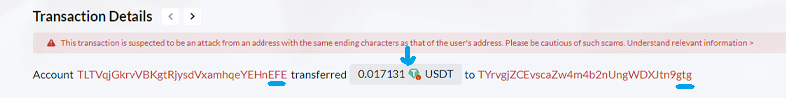
Now, the scammers take a strategic action. They sent a small transaction of USDT (0.017131 USDT in this case), basically sending from the new "fake FE" address to the victim "tg" address. The sum involved is insignificant, often so small that it might appear insignificant to the victim. This little transaction affects the order in which transactions appear on the wallet, showing the malicious one at the top of the transaction history.
By placing the "fake FE" address first on the transaction history, the scammers increase the possibility that the owner of the address "tg" will inaccurately copy and paste the "fake FE" resulting in confusion and sending the USDT to the fake address, setting the stage for the victim to make a costly error in their next transfer. Understanding this phase is essential for identifying the strategic nature of this crypto dusting attack and the lengths scammers go to deceive their victims.
Fourth Step: The Unintended Transfer to the Fake Address
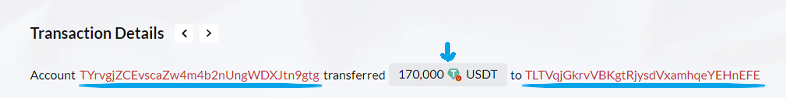
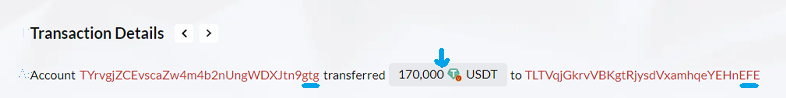
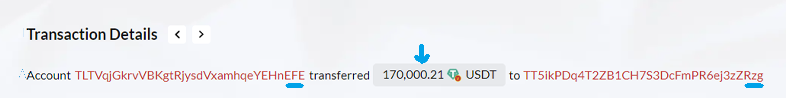
During this stage, the unsuspecting victim, "tg," makes a mistake. They forget to inspect the middle characters of the receiving address and mistakenly think that the address ending with the character "FE" is the real "FE" address. As a result, they copy the address of the fake "FE" and use it as the address for the legitimate recipient. In our example, "tg" sent 170,000 USDT to the fake "FE" address!
The scammers made a tricky plan that caused "tg" to accidentally copy the address of the fake "FE," leading to this crypto dusting attack. This little mistake has far-reaching effects. The USDT planned for the honest recipient is sent to the scammers' address, resulting in a loss of 140,0009 USDT. Unintentionally sending the funds to the scammers. This is when the USDT scams come to realization, and the scammers successfully obtain the victim's USDT.
Fifth and last Step: A Bot Starts to Hide the USDT Stolen
With the successful transfer of USDT from the victim's wallet to the scammers' fake address, the last step of the address poisoning attack evolves. The scammers use a bot to fast act to move the stolen USDT directly to the final destination, the "Master Scammers Wallet", (TT5ikPDq4T2ZB1CH7S3DcFmPR6ej3zZRzg). A last transfer from the "fake FE" address sends the 140,00.21 USDT to the "Master Wallet".
This swift scheme tries to launder the stolen USDT, covering its source and making it difficult to trace or recover. By sending the money to their real wallet or an external account, the scammers aim to alienate the misappropriated crypto and the victim's wallet. Basically, they aspire to erase any proof of their involvement, making it challenging for the victim to track the money course.
In conclusion, 629,888 USDT was stolen in a few days!
Understanding this last step is essential for realizing the purpose of a crypto dust attack and the challenge it poses for victims aiming for redress. Once the USDT has been transferred out of the victim's reach, it becomes impossible to recuperate the stolen funds. Unfortunately, "tg" is not the only victim of this group of scammers. As you can see in the transaction history of the “Master Wallet”, “zg”, five different USDT owners have fallen for this scam, each losing differing amounts, but all misled in the same way.
Our PlasBit research team has discovered that this address poisoning attack has substantial outcomes, resulting in devastating consequences for crypto users. These scammers have robbed a shocking quantity of 629,888 USDT in just a few days.
Protect Yourself From The Crypto Dusting Attack
An address poisoning attack is dangerous, but being proactive can help prevent your funds' loss. You must understand the scammers' favorite targets, how to improve your privacy, endure the boredom of these attacks, and know all the best techniques for safe crypto transfers.
- Who are the target wallets
These scammers primarily target individuals or entities with substantial crypto holdings. These high-value targets are typically called "whales" in the Web3 ecosystem. You may be at a slightly elevated risk if you find yourself in this category, living in an area with high levels of personal protection and security situations or political instability. These attacks could be a preparatory step to more nefarious activities, such as phishing, fraud, extortion, or even physical threats.
- Enhancing Your Privacy
The crypto world has seen considerable enhancements in privacy measures over the years. Many modern wallets and exchanges have implemented advanced components to mitigate the risks associated with USDT scams. These include using HD wallets, identifying dust UTXOs, and combining them with anonymity networks like the Tor Network or VPNs. PlasBit, for example, provides privacy-focused wallets and features that significantly decrease the typical problems related to these crypto dust attacks.
- Tolerating the Bother Factor
It's important to recognize that having crypto dust in your wallet doesn't grant anyone control over your funds. These trace amounts of cryptocurrency are not sufficient to compromise your wallet security. Privacy measures and security tools integrated into new wallets and exchanges have remarkably reduced the risks associated with these attacks.
- Improving Secure Transfers
The first line of protection against crypto dust attacks is awareness. Comprehending the alert signs can greatly decrease your exposure to such USDT scams. Some typical red flags on Tron network to watch out for include:
Unrequested Transactions: Be careful of receiving little, random transfers or transactions with insignificant quantities of cryptocurrency. These could be the initial steps of a crypto dusting attack.
Fake Addresses: Double-check the recipient's address before starting any transfers. Scammers often create addresses that closely resemble legitimate ones, with small divergences that can be easily ignored. Moreover, only the first and last alphanumeric characters are visible on the Tron network. Be sure to visit the transaction page and check that the whole address is correct, not just the first and last characters.
Strange Wallet Activity: Something might be amiss if you notice irregular or unknown activity in your wallet or see multiple small transactions. Examine further.
- Tips for Safeguarding Your USDT
To improve your safety in the Web3 space, consider these helpful tips:
Use Respected Wallets: Opt for well-established wallets with strong protection components. Study and read reviews before choosing a wallet.
Use Two Wallets: Using at least two types of wallets is suggested, one secondary for smaller daily transfers and one primary for storing most of the value. Use the primary wallet only to transact with and from your secondary wallet.
Double-Check Addresses: Always verify the recipient's wallet address. Even a single character disparity can lead to disastrous effects. Check that the full address is correct.
Regularly Inspect Wallet Activity: Check your cryptocurrency wallets' transaction history and balances. If you see any doubtful activity, address it promptly.
Educate Yourself: Stay knowledgeable about the latest frauds and security dangers in the Web3 space. Knowledge is your best defense.
These safeguards can seriously decrease the chance of falling victim to a crypto dusting attack.
Summing It Up
In conclusion, we summarize the key elements and the significance of staying vigilant about the crypto dusting attack on Tron network. Address poisoning attacks are dishonest methods that exploit tiny, apparently insignificant quantities of USDT in users' wallets. These attacks involve carefully staged steps, often leading to significant economic losses for unsuspicious victims. Comprehending how these attacks work and identifying the red flags is important to protecting your crypto assets. Through this case study, we've seen firsthand how a crypto dusting attack can affect a person. By understanding real-world examples, you can reasonably value the importance of diligence and cautiousness in cryptocurrency transactions.
PlasBit research team recommends users in the community use the most helpful protection methods to defend themselves from falling victim to address poisoning attacks. By following these measures and staying informed about potential USDT scams, you can minimize the risks associated with cryptocurrency transfers and maintain the safety of your investments. Remember that in the ever-evolving ecosystem of Web3, awareness and education are your most potent instruments for self-defense. By arming yourself with knowledge and adhering to best practices, you can enjoy the advantages of cryptocurrencies while mitigating the threats. We hope this article has provided you with the knowledge and tools required to navigate the ecosystem of cryptocurrencies safely and securely. Stay educated, stay alert, and continue studying the exciting opportunities of the crypto world while protecting your economic interests. We offer additional resources for further reading and learning cryptocurrency security, and our research section can help you stay well-prepared for reaching financial freedom.