An other complex and interesting investigation from ZachXBT led to the arrest of 3 young U.S. guys (Greavys - Malone Iam; Wiz - Veer Chetal, and Box - Jeandiel Serrano) for stealing over $230 million in cryptocurrency from a Genesis creditor. This case is very interesting, both because the scammers used a very sophisticated social engineering attack and because they decided to launder the money in some of the dumbest ways possible.
We will unveil the facts behind the $230 million cryptocurrency scam, that was carried out by three young men who through a sophisticated social engineering attack gained access to a crypto whale’s wallet. The stolen crypto was used to purchase luxury cars, watches, clothes, and extravagant gifts for women who turned them down anyway. They even spend more than $500,000 on one night in a nightclub. They literally did all the most obvious ways to be tracked down and arrested. If that’s not all, they recorded the scams' processes, giving authorities additional proof to charge them. This story is both daunting and funny since A) the person scammed was probably an early adopter of Bitcoin, and saw its fortune stolen from dumb kids with a complex but predictable social engineering attack, and B) These kids did all the dumbest things you can ever imagine to get caught: They bought expensive stuff, tried to convince girls to stay with them with fancy gifs, recorded themself while committing crimes, and featured their own name on signs that were paraded around in the club, paying around $570,000 bill per night. As you can imagine, 20-year-old kids spending that amount of money is not normal, and it’s natural to pose legitimate questions about the origin of those funds.
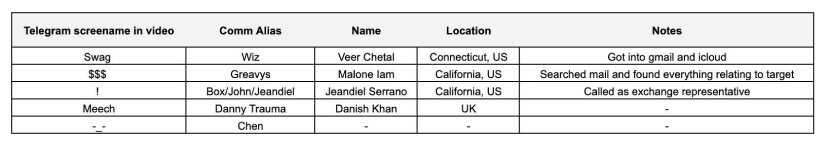
In this in-depth research, we’ll analyze and collect information from various sources, including the extensive analysis of ZachXBT, Cryptoforensic Investigators, ZeroShadow, the U.S. Attorney's Office of the District of Columbia, and other online sources. We aim to give you a holistic view of the scam, analyzing how scammers used social engineering tactics to trick the victim, how they tried to launder the stolen funds, and how they were arrested. Information and knowledge are your first allies to prevent being a victim of scams and keep your digital assets safe. Please also consider that recovering stolen funds is very difficult, and it’s possible only if the funds are stored on exchanges and they agree to freeze scammers’ wallets. If the funds are stored offline in personal cold wallets, recovering funds is possible only by obtaining the physical seed phrase from the scammers. Consequently, all the services that promise you to recover your stolen assets by paying an upfront fee are likely scammers. We’ll also explore how to recognize scam crypto recovery services.
$230 Million Cryptocurrency Scam: How Did These Kids Steal the Funds?
Even if the money laundering of scammers failed miserably, they were actually smart in implementing a quite sophisticated social engineering attack to trick the victim into revealing his private seed phrase. As you should know, you can get access to a self-custody crypto wallet only if you get its private seed phrase, a random sequence of 12 or 24 words that allows you to access the wallet. Brute-force attacks on seed phrases are likely impossible, as we explored in a previous analysis, since the probability of guessing a seed phrase is something like 1:10^71, resulting in extremely low possibilities. So, the only ways to get access to a seed phrase-protected crypto wallet are through A) physical stealing of the metal or paper card on which you wrote the seed phrase; B) Tricking you into revealing your seed phrase through a social engineering attack, and that’s the case of this $230 million cryptocurrency scam.
How Did this Social Engineering Attack Work?
The victim was a Genesis creditor (Genesis was a crypto lending platform that collaborated with Gemini in their Earn program, and they are currently refunding users) who was holding more than $230 worth of cryptocurrencies in his Gemini account. The victim basically transferred his crypto assets to another wallet owned by him, but in the process, he shared his screen with the scammers and inadvertently showed his wallet’s seed phrase, allowing scammers to control the wallet with the funds. Let’s explore this social engineering attack better.
Step 1: Impersonating Google support
The first step of this scam involved calling the victim with a spoofed number, impersonating Google support, and telling him that the Google account had been hacked. They get access to his mail; this is so they can find out which exchanges he has an account in, such as Gemini, and more relevant information that can act as a foundation for social engineering later, even stuff that is not directly specified. Consequently, they understand which exchanges and platforms the victim used, including Atomic Wallet, Blockchain.com, and Gemini.
Step 2: Impersonification of Gemini support and reset 2FA
To add credibility to the hacking risks, they called the victim impersonating Gemini support, creating in the victim a sense of fear for his crypto assets. This adds a layer of legitimacy to the threat of hacking, convincing the victim that the risk of losing all cryptocurrencies is real and imminent. Consequently, the victim changed the 2FA verification and sent the funds to a compromised wallet.
Step 3: The victim shared the screen and scammers got the private keys
In the third step, the scammers convinced the victim to share the screen on AnyDesk, and they saw the wallet's private key from Bitcoin Core, gaining access and being able to move funds to their wallets as a result.
Step 4: They split the money and divided it among different exchanges
In the final step, they divide the funds and move them across multiple exchanges and wallets, converting them into other cryptocurrencies between Bitcoin, Litecoin, Ethereum, and Monero. They tried to launder the money and convert some of it to fiat currency to be used in various ways.
What did They do with the $230 Million Cryptocurrency Scam Loot?
The most funny part of this scam is how these pathetic kids used the stolen funds. In fact, if you think about committing such a crime, as every “respectable criminal”, you should avoid making it known that you have accumulated such wealth, and you prefer to keep it secret. However, these kids were so enthusiastic and excited that they started spending money in many fancy ways, trying to attract girls and get social approval. They made numerous mistakes and created suspicions about the legality of their funds. Additionally, their tactics to attract girls never worked out, and they were refused various times even if they offered luxury gifts, including expensive bags and Lamborghini cars. What did they do?
Luxury Cars, Jewelry and Clothes
“If rappers wear a lot of expensive jewelry and clothes and have a lot of girls, if I wear that luxury stuff, I’ll get a lot of beautiful girls too." This is the dumb thinking of these scammers, especially Malone, showing how this generation is cooked and how social media and “alpha males” distorted the concept of “success” for these guys. Wearing an expensive watch or luxury clothes doesn’t guarantee you have charisma, and this is the demonstration. These guys should have read “How to be a scammer: 101 guide” before starting to spend the money. They completely lack common sense: Instead of keeping a low profile and taking time to figure out how to move out of the country to a no-extradition place, Malone purchased more than ten expensive cars, luxury jewelry, fancy clothes, and more superficial and useless stuff. Personally, I’m also wondering how car dealers and jewelry stores allowed them to purchase these expensive things without questioning the legitimacy of the funds, but probably, “with a surplus,” you can corrupt everyone or use a figurehead.
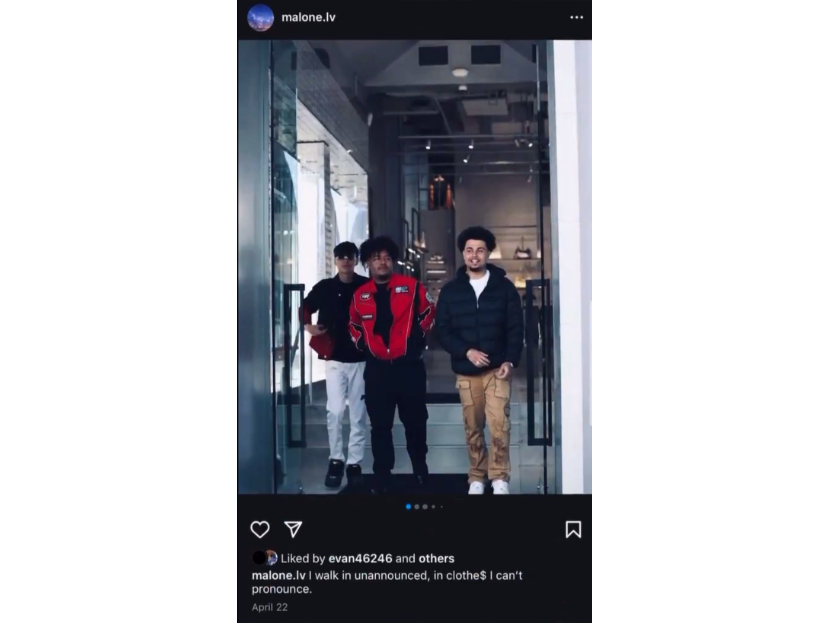
Expensive Gifts to “Attract” Girls
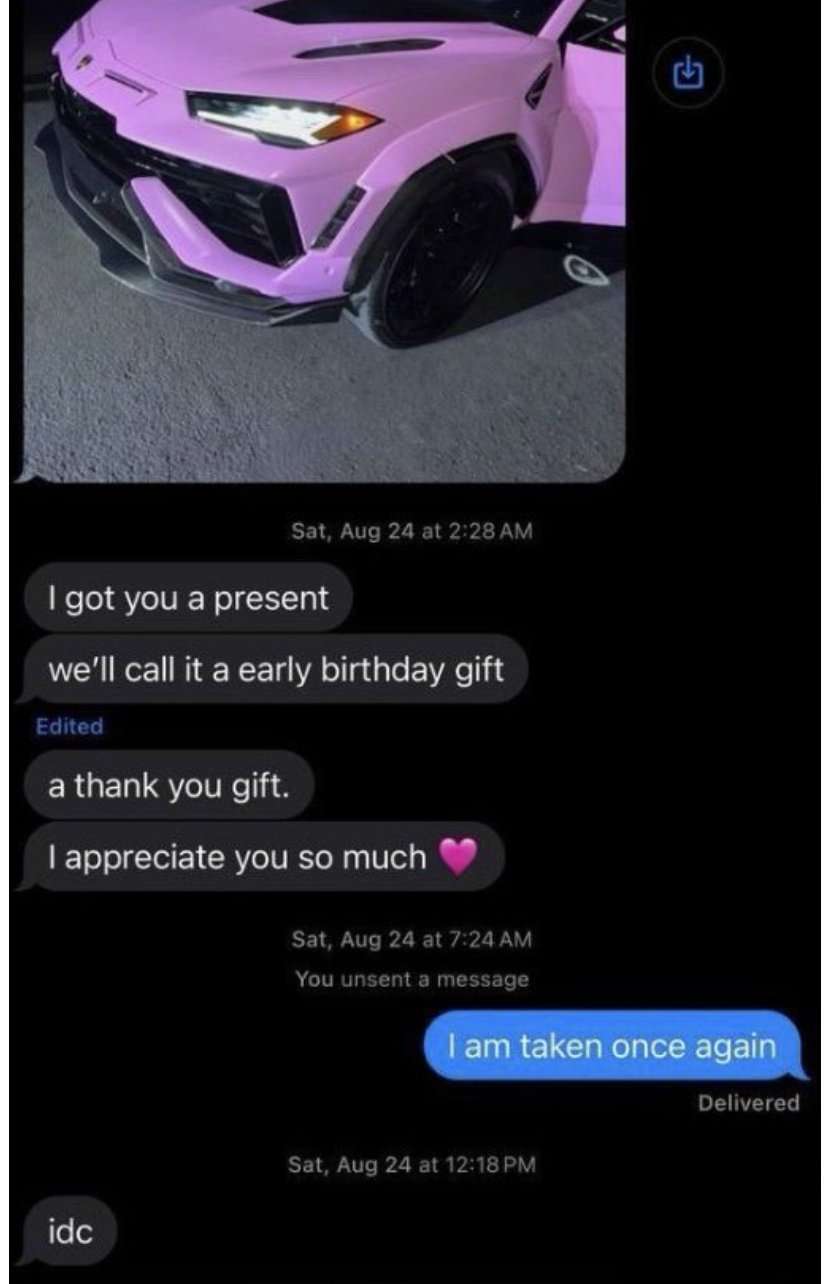
The most pathetic thing is thinking that every girl can be “purchased” with expensive gifts and money. Probably, these guys saw too many “alpha male” podcasts in which there are girls that sell their bodies on OnlyFans, but not all the girls are like that. Conversely, and fortunately, they are just a small minority. In general, even if you see rich people have a lot of girls, it’s not about money but charisma, lifestyle, humor, intelligence, and other qualities that cannot be purchased with money. Being rich can just amplify what you already are, and in the case of our scammers, amplified their being pathetic and superficial. Malone purchased something like 5 Birkin bags that cost around $50k each and a Lamborghini just to gift them to girls trying to attract them. The result? The girl who should have received the Lamborghini texted him, “I am taken once again”, without even saying “thanks”, and another girl who received a free Birkin bag just said to him something like, “Thanks, I take it, but it’s not my style,” and went away. This is a clear demonstration of how Malone’s brain is fried and the stupid tactics and thoughts he used to try to gain some traction with girls. After over a million spent on gifts, he didn't even receive a kiss on the cheek.
More than $500,000 Billed in Clubs every day
Another dumb thing our main protagonist, Malone, did, is to go out in clubs almost every day and spend around $500k in alcohol, fancy bottles, and signs. Wondering what they asked to write on signs? Their names, i.e., “@Malone”.
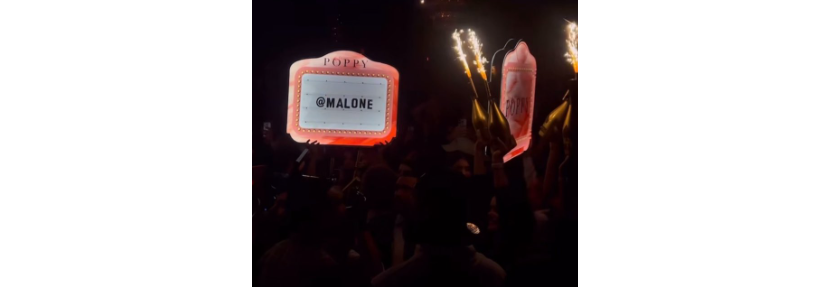
This is another reminder that before you launder $230 million in cryptocurrencies, you should participate in a “how to not be caught after committing a crime” class. Unbelievable stupid kids... This is a clear demonstration that, like winning a lottery ticket and losing all the money quickly, people who don’t actually work hard to become wealthy cannot handle so much money and will spend it on stupid and superficial stuff and activities, looking to elevate their social status and get social approvals.
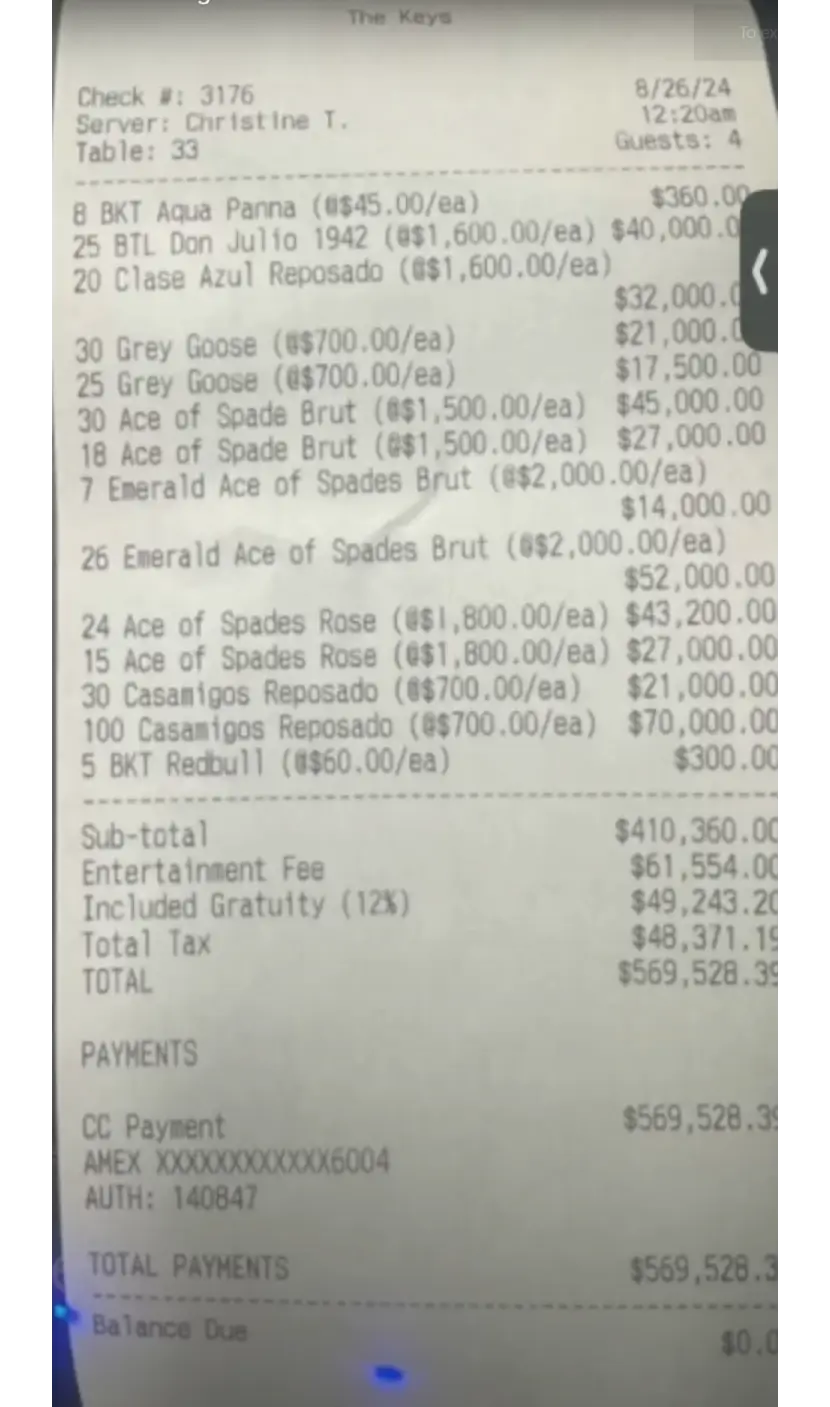
They actually overpaid alcohol, drinks, and cringe signs just to show people they are rich (with stolen funds), making the situation quite funny and sad at the same time. It’s also funny they actually paid $60 per Red Bull.. instead of less than $3.
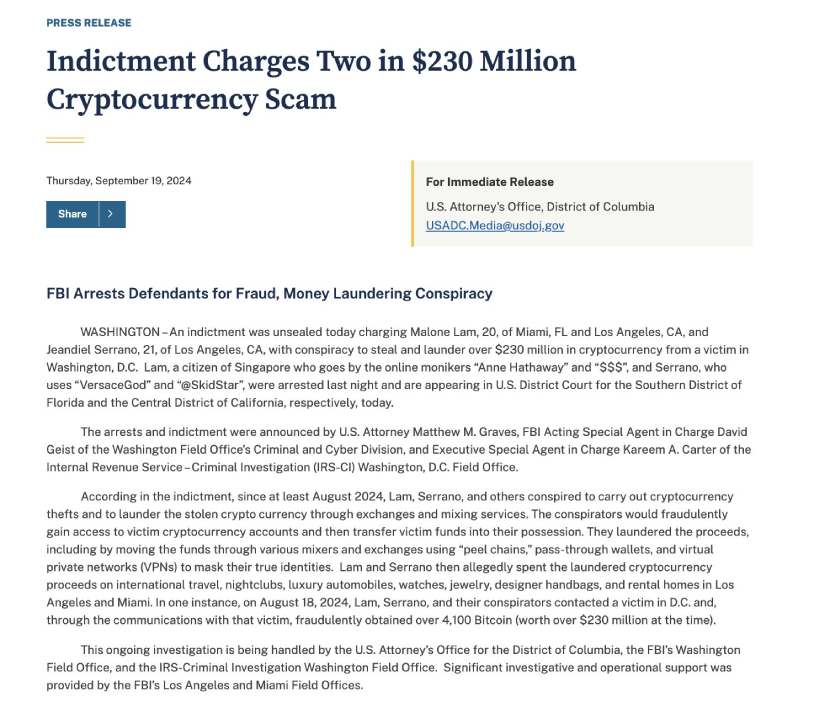
How Were The Scammers Arrested?
With an in-depth analysis, collaborating also with investigation firms such as Cryptoforensic Investigators and ZeroShadow, ZachXTB traced the stolen funds and has been able to identify the scammers and contribute to their arrest. Zach rebuilt the transactions that scammers executed to try laundering the money, highlighting how they used more than 15 exchanges and various cryptocurrencies, including Bitcoin, Litecoin, Ethereum, and Monero, before converting part of the funds into fiat currencies. Since most of the funds have been converted to XMR (Monero), scammers added a layer of privacy due to the anonymous nature of the Monero blockchain, however, they recorded all the processes on a video stream, forgetting to hide their real name from it. Additionally, while laundering the money and converting it to XMR, they accidentally linked the laundered funds with the dirty funds on multiple instances, creating a link that reveals that initial and final addresses are connected. However, as just mentioned above, the most evident proof recovered was the screen recording they did. I suppose the first rule of scammers/criminals is not to leave proof of the crime, but evidently, our young scammers didn’t think about it and recorded all the processes on Discord, allowing authorities and investigators to easily charge them for their criminal actions.
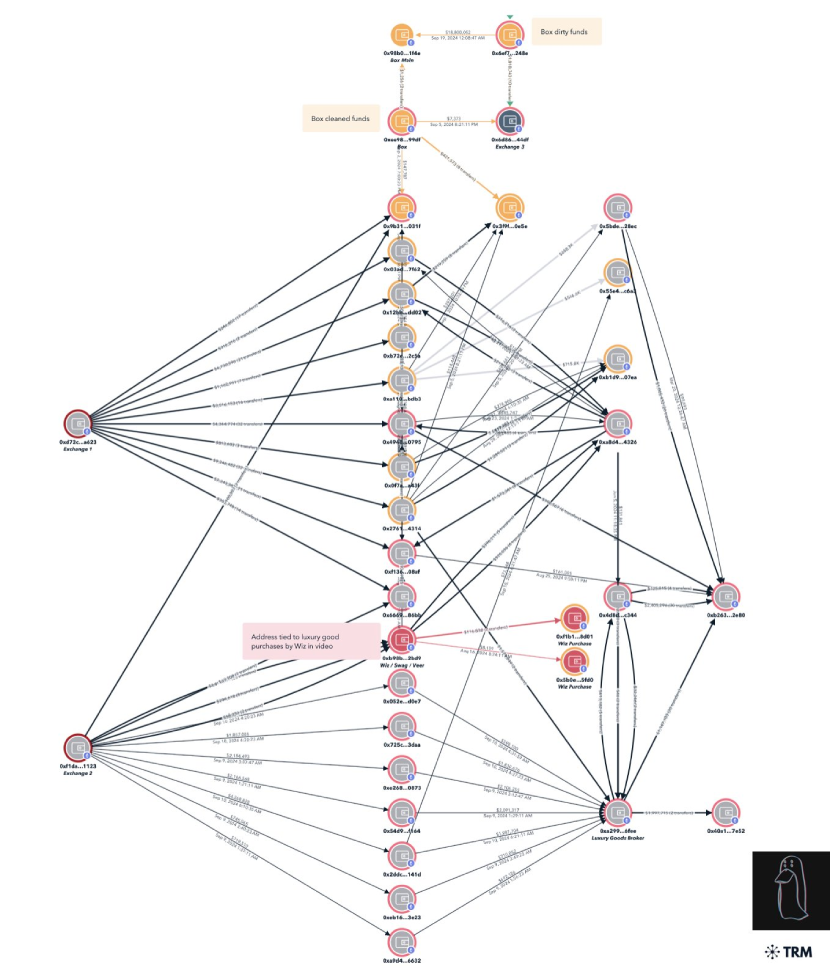
Additionally, the fancy (but short) lifestyle allowed investigators to use OSINT (Open Source Intelligence) tools (gathering and analyzing publicly available data for intelligence purposes) to reconstruct the activities and movements of the scammers via public platforms such as Instagram, Twitter, Discord, and more. The multiple clips posted by people in clubs clearly showed Malone, the name of one of the scammers, and were helpful to the authorities to locate and identify the people behind the scam. During the investigation, Zach collaborated with Binance to freeze some of the accounts used to launder the money, and currently, $9M+ has been frozen, and $500k has already been returned to the victim. On September 18, Box (Jeandiel Serrano) and Greavys (Malone Iam) were arrested in Miami and Los Angeles, and funds are being recovered by the financial authorities and investigators.
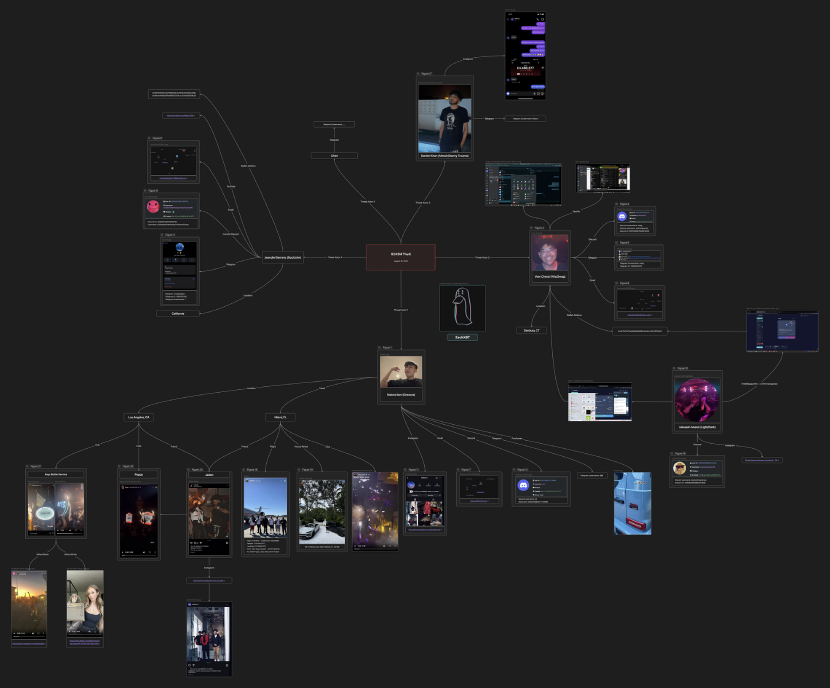
On September 19, an indictment was unsealed by the authorities and Box and Greavys have been charged for conspiracy to steal and launder over $230 million in cryptocurrencies from a victim in Washington D.C. In the document, the authorities clearly stated all the crimes committed, including crypto theft and money laundering through various mixers and exchanges using “peel chains”, pass-through wallets, and virtual private networks (VPNs) to mask their true identities.
Lessons from this $230 Million Cryptocurrency Scam
Scammers, even if young and quite dumb, are becoming more sophisticated day by day, and the unregulated and “wild” nature of cryptocurrencies doesn’t help to prevent such frauds. Many are wondering how the victim, holding more than $230 million in cryptocurrencies, could have been scammed by a group of fools, assuming that the victim must be minimally knowledgeable about cryptocurrency and security by holding this amount of money. However, if you start feeling fear for your assets’ security, you can be caught by panic and act irrationally without thinking twice about what you’re actually doing. Even if the crypto scam is somewhat sophisticated, with scammers gaining access to multiple accounts and information about the victim, it’s likely a classic “Indian call center” scam. Be aware that in a situation of panic, every person, even if expert, is more likely to be trapped. Another common scam related to this one is the fake recovery scam, in which people contact you to recover stolen assets, usually asking for expensive fees. Be aware also about this kind of scam because once your cryptocurrencies are transferred, it is very difficult to recover them, and you can do so only with the collaboration of authorities and exchanges, as happened in this case. Now, let’s recap some key points to bear in mind to not fall for this kind of social engineering scam.
Never share your seed phrase
Your seed phrase must not be shared with anyone; treat it like the keys to your vault. Even if the request seems legitimate and comes from reputable customer services of relevant exchanges or platforms that know your personal information in detail, they never need your seed phrase to offer you help. Keep your seed phrase offline, written preferably on a metal card, and store it in a safe place. For more security, consider dividing your seed phrase into two different metal cards so that even if you receive a physical attack, scammers need to know two different places and cannot get access to the wallet with only half of the seed phrase.
Use multiple wallets
Especially if you’re holding a huge amount of cryptocurrencies, as in this case study, consider using multiple wallets to spread the risks of theft. In this way, even if one of your wallets gets hacked, you lose only a minimal portion of your assets. However, remember that this method needs careful attention to safely conserve your seed phrases without losing them. People lose money on crypto in various ways, be careful and store your seed phrase securely.
Verify communications independently
If you receive a call, email, or message claiming to be from a platform you use, don’t act immediately. Hang up or close the email, and contact the company directly using their official website or customer support channels. Take your time and don’t act immediately; pause and think for some minutes with a clear mind. Most of the time, scammers aim to create a sense of urgency to create pressure and make you act in an irrational and impulsive way. Avoid taking action without thinking and assess the situation clearly.
Stay informed about security measures and emerging threats
As we mentioned before, your best ally in crypto security is knowledge. Scammers implement more sophisticated ways to trick you into revealing your personal information, passwords, and seed phrases, so recognizing a scam early is the best thing to avoid being trapped in it. Be informed and implement the highest security measures to minimize the risk of losses, including using hardware wallets, multiple wallets, storing your seed phrase in secure places, and more. For additional security, if you’re hodling large amounts of crypto, consider using multi-signature wallets.
Beware of crypto recovery scams
Recovering stolen funds is usually possible only if scammers deposit funds in centralized exchanges that have the ability to freeze the scammers' accounts. If the funds are moved to decentralized exchanges or self-custody wallets, recovering them is almost impossible if you don’t manage to recover the private keys, and it’s possible only to collaborate with authorities and physically recover the seed phrase from the scammers. Consequently, if someone contacts you to recover funds and asks for an upfront fee, he is likely a scammer. Legitimate services will not ask you for payment in advance to recover your funds, and informing financial authorities is a must anyway. Be aware of crypto recovery scams.
Regular audit of your security measures
Conduct periodic reviews of your security practices since scammers become more sophisticated day by day. Find your own vulnerabilities before scammers do it, and try to hypnotize all the possible ways in which you can be scammed so that you can implement proactive measures to prevent it. The most common way in which scammers trap you is by exploiting your pc or psychological vulnerabilities, so never let down your guard and implement the highest security measures.

Final consideration about this $230 million cryptocurrency scam
This scam highlighted both the sophistication that some young guys can implement to trick you into being trapped in their evil plan and the distorted perception of the world they have. In fact, even if they managed to execute a complex social engineering attack on a - plausible - expert cryptocurrency holder, their brains are fried, and they were unable to handle the stolen money without drawing attention to getting social approval and recognition.
It’s like they announced to the world “Hey! Look at me, I’m rich because I just stole millions worth of crypto! I’m cool now!”. It clearly highlights that these ones were insecure guys looking for recognition and, ultimately, girls. However, even with millions of dollars and giving away expensive bags and cars, they didn’t manage to have a single kiss from a lady. This is why we define these scammers as pathetic because their maximum ambition was going out in clubs and “being popular” by trying to literally “buy” girls. Fortunately, this strategy didn’t work, and all the girls involved had much dignity and gratitude for themselves for rejecting the advances of these young, pathetic, and clumsy scammers.
Remember, even if cryptocurrencies allow people to have full sovereignty and control over their own assets, this advantage comes at a cost: the responsibility of implementing effective security measures and not falling into scams. Adopt best security practices, be informed, and maintain a healthy level of skepticism.







