Hackers use sophisticated techniques and strategies to systematically hack users’ social media accounts, platforms, emails, and, most importantly, crypto wallets. It’s an increasingly dangerous threat, and the strategies are complex and require significant coding knowledge and skills. However, it’s possible to reduce the risks of being hacked by using advanced security measures following the latest best practices.
In this detailed research, PlasBit will analyze how brute-force attacks work and show a recent case study, explaining how a Vietnamese hacker has been able to steal crypto assets from a crypto exchange wallet. Let’s start answering the most important question: Can hackers steal crypto using brute-force attack on a crypto wallet? No, it's not possible since most cold crypto wallets use long, complex private keys (usually 12 to 24 words), making the possible combinations exceptionally extensive and requiring enormous computational energy and time. However, if you’re using a hot wallet or crypto exchange wallet, it is usually accessed through a common classic password, and it can be hacked more easily, depending on the complexity of the password.
If you’re using a crypto exchange wallet, you should also implement 2FA and a secure password for both the crypto platform and the email linked. Consequently, it’s necessary to implement the most effective security measures, which we’ll explore in this article together.
What is a Brute-Force Attack?
One of the most common ways hackers use to get access to your account is through brute-force attacks. How does it work? A brute-force attack implies systematically trying all possible combinations of passwords or keys until the correct one is found, using scripts and other advanced techniques to make the process automatic and fast. However, there are various types of brute-force attacks, and depending on the situation and the data, the scammers decide which one is more useful for their malicious goals.
Simple Brute-Force Attack
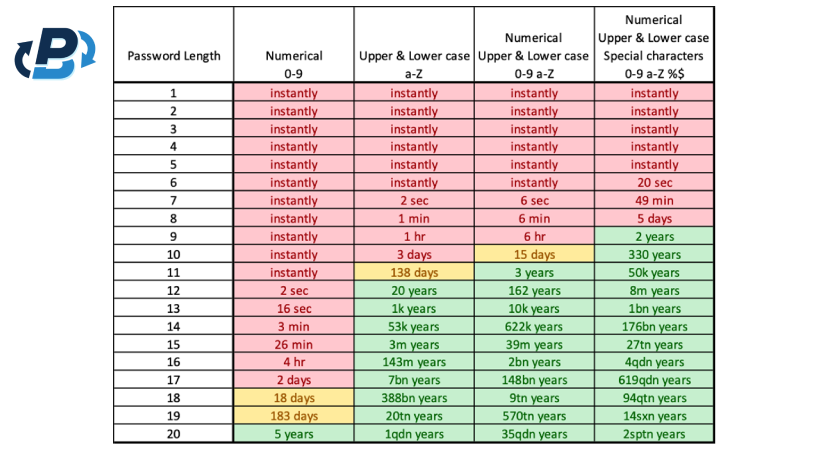
The first and most common version of this kind of hack is the simple brute-force attack, in which scammers crack passwords by trying every possible combination until the correct one is found. In this case, the time and computational energy needed depend on the length and complexity of the password, exponentially increasing with longer passwords that also include numbers and special characters. Considering the average computational power a common computer uses, the following chart shows how much time is required to hack a password, depending on its length and complexity. As you can see, the difficulty increases depending on the types and quantity of characters used and underscores the importance of implementing long, sophisticated, and unique passwords to increase the security of your account. However, it doesn’t consider that hackers might use high-performance computer networks that sum up the computational power of each one and decrease the time needed to hack the passwords. Additionally, we must consider that in the future, quantum computers can exponentially increase computational power, consequently reducing the time needed to hack even the most secure passwords.
Dictionary Brute-Force Attack
In a dictionary brute-force attack, the hackers use large lists of common and/or predictable passwords to reduce the time needed to guess the password and get access to the victim’s account. In fact, unlike the simple brute-force attack, hackers leverage human psychological bias and behavior, considering that people commonly use the same password methods or patterns, such as, for example, “Password123”, “P4ssw0rd”, “letmein”, “S3cr3t”, etc. This kind of attack requires less computational energy than simple brute-force attacks since the attacker doesn’t try every possible combination, but only the most used combinations and patterns. The most sophisticated hackers’ scripts also automatically include words that are contained in the email: For example, if your mail is “cryptotrader@gmail.com”, they might automatically try passwords like “CryptoTrader1”, “cryptotrader0”, etc., consequently increasing the possibilities of guessing the correct password. A good way to increase the difficulty of the password is to not use common words and password patterns, including, on the contrary, random sequences of letters with also special characters and numbers. The less the password is predictable, the higher its security.

Brute-Force Attack on a Crypto Wallet: Is it Possible?
Now, having understood the types of brute-force attacks and how weak passwords are relatively easy to hack, we can explore in detail if this kind of attack is possible to get access to a crypto wallet.
Brute-Force Attack on a Cold Wallet
Using a cold wallet allows you to implement higher security measures and drastically reduce the risks related to being hacked. Why? Because cold wallets are offline and come in the form of physical devices. They don’t have a classic password, and to get access to them, you literally need to steal the seed phrase, which is stored offline, usually in a metal card. Consequently, the only ways to hack a cold wallet and steal funds are:
A) Steal the physical card on which is written the seed phrase
It means the hacker discovers the physical location and commits theft by person.
B) Brute-forcing the seed phrase (likely impossible)
As we analyzed earlier, seed phrases are usually composed of 24 words and randomly generated from a catalog of 2048 words. Consequently, there are 10^80 possible seed phrases, and considering each human (8 billion people) on the earth had 1,25 wallets (to make the calculation easier), there would be 10^10 active crypto wallets. It results in 1:10^71 chance you’re hitting an existing wallet with brute force, and that’s an extremely extremely low possibility. Even using a supercomputer with a rate of 10^9 guesses per second, brute-forcing a 12-word seed phrase would be computationally infeasible because it would take 10^70 seconds, far longer than the age of the universe (10^17) to exhaust all possibilities. As you can understand, brute-forcing a cold wallet’ seed phrase is likely impossible with current technology, without even considering that not all active wallets have funds inside.
Brute-Force Attack on a Hot Wallet (DEX)
A hot wallet is an online crypto wallet that is always connected to the internet. Hacking a hot wallet is easier than a cold wallet since its private keys are generated online and the wallet is always available for access through a password (if you get access to the victim’s device). This is the main weakness because if a hacker gets access to your pc, he can brute force the password, which is generally easier and requires less time than hacking a seed phrase. Additionally, most of the hot wallets do not have the option to implement 2FA, and consequently, the hacker needs to get access to only one device to steal your crypto assets.
Hacking a hot wallet can be done in 3 ways:
A) Virus that reads your movements
Hackers can inject a virus into your computer and track all your movements, and if you insert your seed phrase, the hackers can read it and record your screen in real-time. Consequently, the hacker can use his device and get access to your crypto hot wallet by inserting the seed phrase that he discovered earlier.
B) Virus that takes control of your computer
Hackers inject a virus that takes control of your computer, and even if you don’t insert your seed phrase, he can brute-force by using a simple or dictionary attack to guess the password, allowing him to log in to your crypto wallet and drain out the funds.
C) Brute-forcing your seed phrase (likely impossible)
In this last option, the hackers implement a brute-force attack to guess your seed phrase. However, as in the case of the cold wallet, guessing a 12 or 24 words seed phrase is likely impossible, since it requires too much computational energy and time, making it likely impossible to hack your crypto wallet even with a super computer, considering the current technology.
To prevent a brute-force attack on a hot wallet, remember to implement an anti-virus in your computer, store your seed phrase and password offline, implement a secure and long password that includes also special characters and numbers, and, if possible, enable the Two-Factor Authentication (2FA). However, PlasBit recommends storing only the funds necessary for daily transactions in your hot wallet and using a cold wallet for your main long-term holdings.
Brute-Force Attack on an Exchange Wallet (CEX)
In the case of a crypto exchange wallet, things might be different, and hackers may be able to get access to the crypto assets easily. Why and how? To get access to your exchange crypto wallet, you are required to have a classic login with a username and password (and 2FA if you’re following the best security practices).
It means that a hacker can get access to your wallets in two ways:
A) Hackers get access to your mail linked to the crypto exchange wallet
As in the case study we’ll describe in the next section, if the hacker gets access to your mail through a brute-force attack, he can request password recovery, overtake the 2FA, create a new password and steal your crypto funds from the exchange relatively easily.
B) Hackers copy the exchange database server offline and try unlimited passwords
If the exchange doesn’t implement the highest security measures to protect its server, the hacker, by exploiting vulnerabilities in the software, such as SQL injection, outdated software, weak authentication mechanisms, or misconfigured permissions, copies offline the hash passwords database of the exchange (or he buys it on the dark web), and he can try unlimited combinations to guess the password, avoiding requests-limit set by the exchange. Once he finds the correct password through simple or dictionary brute-forcing, he can get access to the exchange and steal your crypto assets.
If you don’t set a strong password for both your mail and crypto exchange, it can be relatively easy for the hacker to guess the password (even less than a second). Remember to implement 2FA and strong, unique, long passwords for your email and crypto exchange.

Case Study: Vietnamese Hacker Gets Access to Exchange Wallet
Recently, a user reported to us a serious hack happened on a large crypto exchange. The scammer, who got access to the email linked to the user’s account on the crypto exchange, was able to steal all the crypto funds stored by the user on the exchange. Let’s analyze the steps that the scammer used.
Step 1: The hacker gets the password hash database of the email
Firstly, the hacker identified a security issue in the email provider (libero.it - Italian email provider) and purchased a long list of emails and a password hash database of the email provider on Telegram.
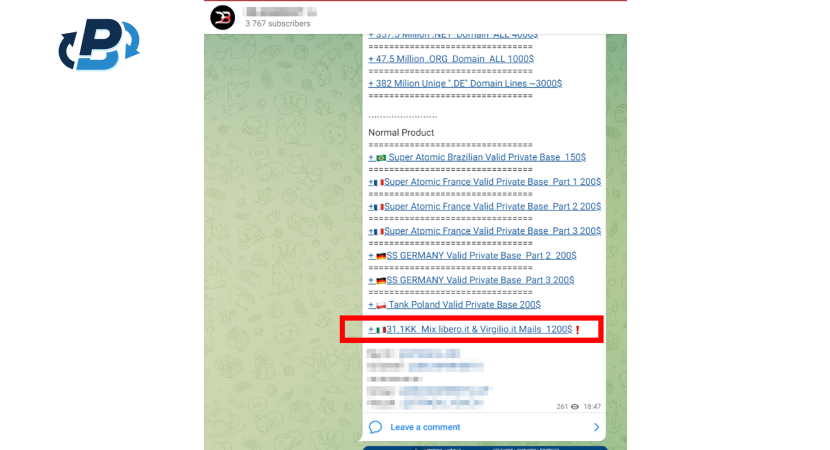
Step 2: The server system of the email provider is copied offline
In our case study, the email provider (libero.it) didn’t implement the highest security measures, and the hacker exploited the vulnerability through SQL injection, outdated software, weak authentication mechanisms, or misconfigured permissions. Consequently, after getting the emails, the hacker was able to copy the compromised server database system offline, allowing it to bypass the security measures of the email provider, such as the request limit for trying to insert the correct password. Finally, he was able to brute-force the password offline using unlimited possibilities.
Step 3: The scammer gets access to the mail
After guessing the password offline, the hacker can easily insert the correct password on the email provider, consequently getting access to the email. Once he is inside your mail, the game will become easy.
Step 4: The hacker requests a change of the password
In step 4, the hacker, having access to your mail, can easily reset the password, locking you out from your mail (especially if you didn’t enable 2FA, which adds an additional layer of security).
Step 5: The scammer gets access to your crypto exchange wallet
Once the scammer locks you out of your mail, he requests the password reset for your crypto exchange account. The crypto exchange sends the email to reset the password, and the hacker is already inside your mail, changing the password and getting access to your crypto exchange wallet.
Step 6: The mail linked is changed and you’re locked out
Once he is inside your crypto exchange account, he can also request a change of the email linked to your crypto exchange account, which will definitely lock you out.
Step 7: The hacker drains all your crypto funds
Once you cannot access both your email and crypto exchange accounts, the hacker literally wins. He has full access to your crypto exchange account (and also all the other accounts linked to your mail). At this point, he sends your crypto funds to his crypto wallet, and the transaction is irreversible. You lost your crypto funds and cannot recover them due to the immutable nature of blockchain technology.
Step 9: The hacker tries to deposit additional funds with your debit card
If that’s not enough, the hacker also tries to deposit additional funds with the bank card linked to the crypto exchange wallet. If your bank doesn’t require additional steps to approve the transaction, the scammer can succeed in depositing more fiat currency, consequently increasing the damage and fund loss. Fortunately, in our case study, the bank didn’t approve the transaction without the confirmation on the bank app on the victim’s mobile phone.
Step 10: The scammer disappears into thin air
Once the scammer withdraws all the funds, he disappears into thin air. Even if you can track the movements of the funds, the scammer uses various exchanges and mixers to spread the funds across different wallets, making it impossible to trace the original wallet and the person behind the attack.
How to track a hacker and discover its identity and location?
Even if recovering stolen crypto is likely impossible, the victim has been able to identify the location of the hacker. How to do that?
1. Try to regain access to your mail and crypto exchange wallet
Even if the scammer locked you out of the mail, you can contact the email provider and report the hack. They should be able to give you the access back and lock out the scammer, allowing you to regain access to the email.
2. Check the login reports
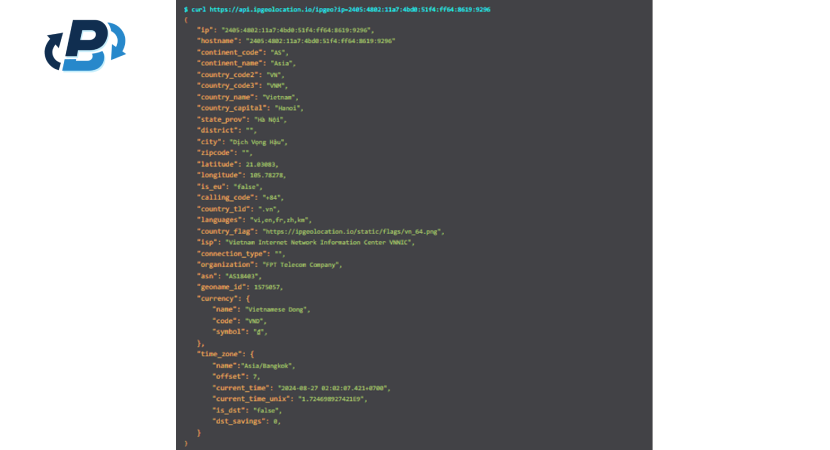
Some hackers commit mistakes, and sometimes they are actually lazy. This means that they might not have used a VPN or proxy, involuntarily revealing their IP address. In our case study, the IP and login information of the hacker was:
Operating system: Windows
Browser: Edge (Chromium Based)
IP address: 2405:4802:11a7:4bd0:51f4:ff64:8619:9296
Estimated location: Hanoi, HANOI, VN
3. Discover the position of the scammer
Consequently, using ipgeolocation.io, the victim was able to discover the location of the hacker, who was in Vietnam. Additionally, the victim discovered the latitude and longitude of the scammer and the ISP provider, which was linked to FTP Telecom Vietnam.
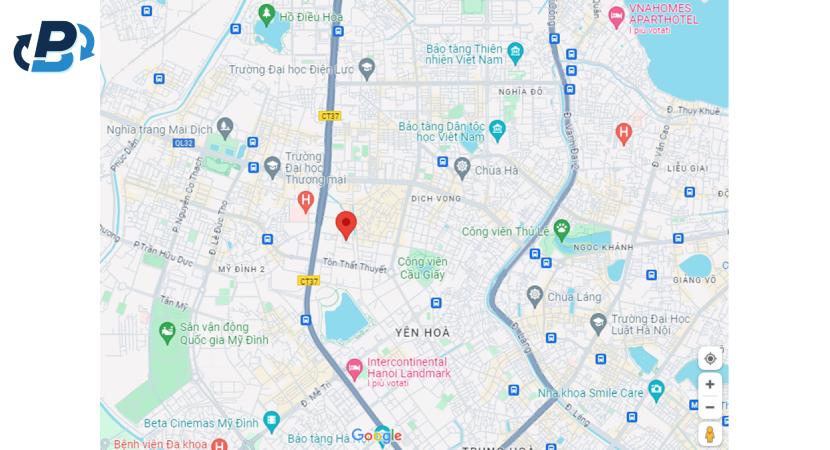
4. Verify what is the physical location on Google Maps
With the latitude and longitude, the victim was able to discover the physical building that was linked to the scammer's signal. The building is used by FTP Telecom Vietnam and other IT companies that could be linked to the scammer. Even if the position may not be so accurate because the scammer could act from a nearby building, the victim contacted the internet provider and provided all the data at its disposal, such as the IP, the date, and the hour. In this case, the hack occurred on July 21 at 9:14 PM (PDT).
5. Wait for additional information and take legal action
If the internet provider used by the scammer is legit, it is in its own interest to reveal the hacker's information and take legal action against him. If you’re lucky, the internet provider will send you the hacker information by mail so that you can take legal action, too.
Essential Security Measures to Protect Your Crypto Wallet
Protecting your crypto wallet in the right ways is essential. Never underestimate the importance of security measures. Here are the most effective best practices:
Use a cold wallet for long-term holdings
Cold wallets store the seed phrase offline, making it impossible for the hacker to get access to your crypto wallet without physically stealing your seed phrase. This means that the hacker must break into your house (or the place where you store the seed phrase) to steal the 24 words needed to access your funds. For additional security, you can also split the seed phrase into various parts, keeping them in different places and making it even more difficult for the hacker to get the complete seed phrase and access your funds. Using a hot wallet is fine if you need to make daily transactions, but remember to store your main holdings in a cold wallet, which is increasingly more secure and safe.
Link a safe mail
If you’re using an exchange crypto wallet, it’s extremely important that the mail linked is safe. Verify on https://haveibeenpwned.com/ if your mail has been part of a data breach, and always use long, complex passwords and two-factor authentication to add an additional layer of security. Remember, if your mail is hacked, the hacker can get access to your crypto exchange wallet and all other accounts linked to your mail, such as social media, apps, and, in some cases, also bank accounts.
Use a secure and unique password
It is never stupid to be reminded one more time that you need to implement a secure password. As we demonstrated earlier, a password consisting only of numbers and less than 13 characters in length can be hacked virtually instantaneously. Conversely, if you use numbers, upper and low cases, and special characters, using a random, long (more than 15 characters), the possibility of being hacked through a brute-force attack is almost zero (the hackers, even with a supercomputer, would need many years to hack it).
Implement 2FA
Implementing two-factor authentication (2FA) is necessary to reduce the risks of being hacked. If two devices are needed to get access to your mail or crypto wallet, you make the work difficult for the hacker, since it must gain control of both your mobile phone and computer. However, even with 2FA activated, scammers can be able to hack your account if you don’t implement the right security measures to protect it. For example, by sim-swapping your mobile phone, they can replicate or alter the messages received on your mobile phone. If you notice suspicious activities on your mobile phone, verify if you’re being a victim of a sim-swap attack.
Avoid public Wi-Fi at all costs
Public Wi-Fi is one of the most used ways to hack people’s devices. If a hacker gets access to public Wi-Fi, such as the ones of the airports, cafès, bars, restaurants, etc. (it’s very common), by connecting your device to it, you’re basically giving the hacker access to your data and device. Hackers can easily steal your passwords, data, and crypto funds if you’re connected to a malicious Wi-Fi. Never use public Wi-Fi since it’s the most common way to get hacked and be a victim of a data breach.
Use a VPN for increased privacy
VPNs (Virtual Private Networks) are a good way to protect your data from hackers and scammers. By hiding your real position, IP, and data, you can make it difficult for the hacker to get access to your information, adding an additional layer of privacy and security. For a safer and private connection, use a VPN to anonymize your traffic and not reveal your personal information to potential hackers.
Verify IP accesses periodically
Periodically verify the login to your mail and crypto wallets. By checking the IP address and location of the account connected to your mail and wallet, you can be able to verify if there are hackers or scammers that have access to your funds and data. For example, if you notice access from suspicious locations in which you’ve not been (generally hacks to occidental users come from Asia (Vietnam, India, China, Indonesia) or Russia), it’s a big red flag: Disconnect all the devices from your account and quickly change your password, implementing a new, more secure one. Attacks often come from Asian locations because, sadly, there are scam-factory prisons like the KK Park, in which people are forced to commit online scams under torture, specifically targeting European or American users.
Never click on suspicious links: Avoid phishing attacks
Hackers can get access to your data and devices by using malicious links in a phishing attack. By clicking on the hacker’s link, which could come from in the form of familiar links that differ for only a small character (such as twiter.com instead of twitter.com, for example), you’re basically allowing the hacker to inject a virus into your computer and track your online movements, discovering your personal information and passwords. If a hacker is tracking your movement through a phishing attack, it’s possible that he will wait until you insert your credentials on a crypto wallet and steal them to get access to it. Once he has injected a virus and is inside your wallet, he can withdraw your crypto funds, and they cannot be recovered, so be careful and don’t click on suspicious links.
Separate storage of private keys and passwords
A last important piece of advice is to keep private keys and passwords in different places so that even if the hacker gets access to your password, he cannot access your crypto wallet and vice versa. However, the seed phrase should be split into 2 different places so that you can increase the difficulty of recovering the full seed phrase that allows access to your funds.
In conclusion, brute-force attacks are increasingly common, and only by being aware of the most effective security practices can you have peace of mind and safeguard your crypto funds. PlasBit hopes this research can be useful to users and prevent them from being victims of hackers. Unfortunately, crypto users often underestimate security, but it should be the top priority. Always use secure, long, complex passwords for both your mail and crypto wallets, and remember to enable 2FA for an additional layer of security to protect yourself from brute-force attack on a crypto wallet.







