Security is a determining factor for operating in cryptocurrencies and is often underestimated. Indeed, a new type of attack is emerging, particularly on the Tron Network: USDT scams are attacks that leverage people's bias, manipulating and tricking users into stealing their USDT, whereas the scam process is insidious because it is done in stages and in order to execute this scam, you only need a small capital and set up a script that operates automatically. To fully understand the mechanisms of this new scam (which is also called crypto dust attack) and do our part to spread education and prevent these thefts, we will analyze a case study of one of the scams perpetuated in the last period on Tron, in which 59,400 USDT has been stolen.
How USDT Scams Work
Innovation in Web3 is rising, and the stage is set for a new bull market. But, along with the opportunities, the risks are multiplying: cybercriminals are always ready to innovate their manipulative techniques and find new ways to carry out theft and fraud. PlasBit's research team works to identify the crypto dust attacks, particularly on Tron, by analyzing the scammers' movements and educating users to prevent these frauds. The case study analyzed takes place on 10 October 2023, resulting in a tragic loss of USDT 59,400.
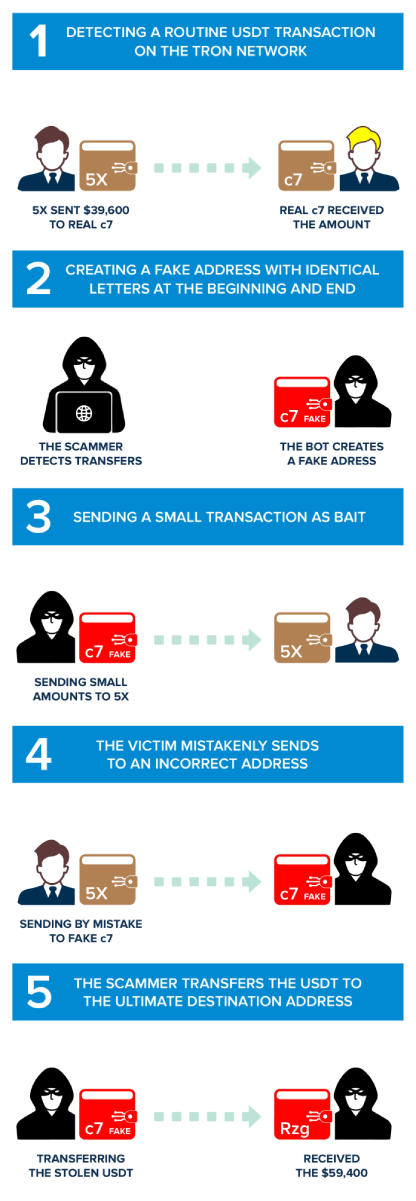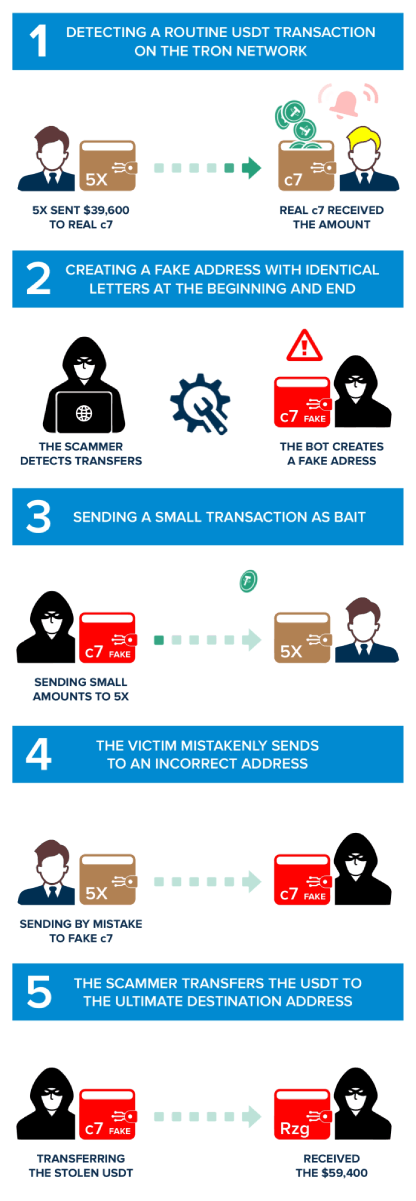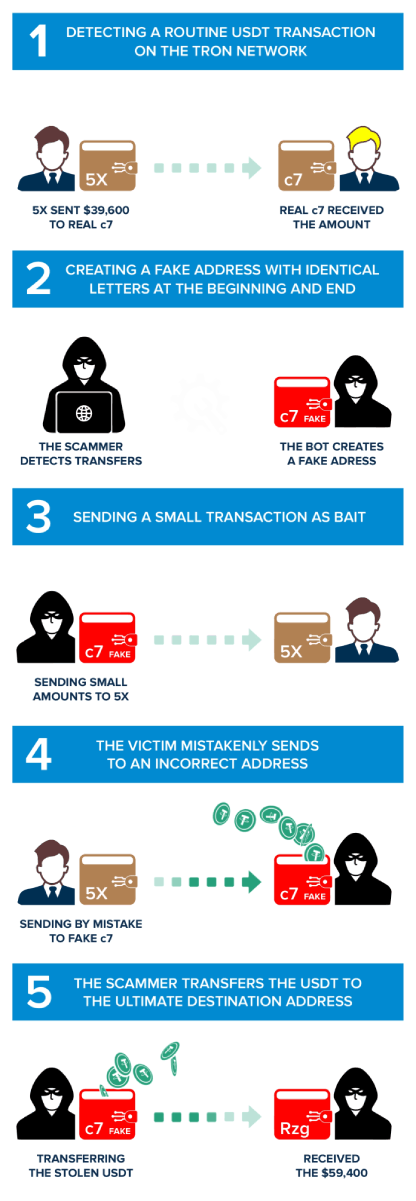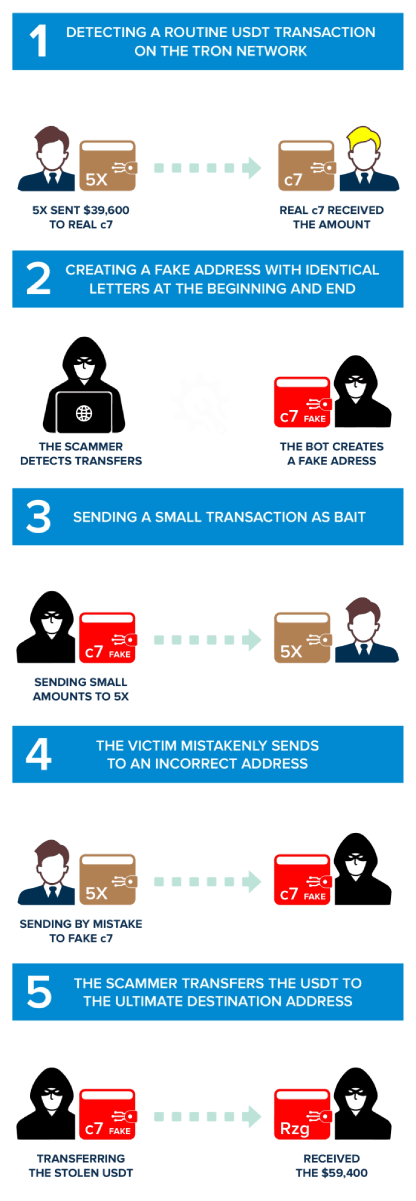
Phase One: Analyzing Tron Network for Standard USD Transactions
Simply, scammers start their attack by using computer programs to check transactions. They look at transactions involving a digital currency called USDT on the Tron blockchain. Their focus is on wallets that recently moved a lot of money. By going after big and busy wallets, the scammers hope to have a better chance of succeeding in their scam.
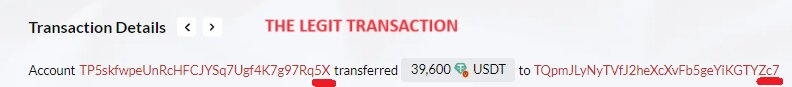
In our case study, the victim is TP5skfwpeUnRcHFCJYSq7Ugf4K7g97Rq5X, and we call it '5X' in the explanation, given the last characters of the address. '5X' constantly moves funds for legitimate transactions and has considerable cryptocurrency, making him a perfect victim of scammers.
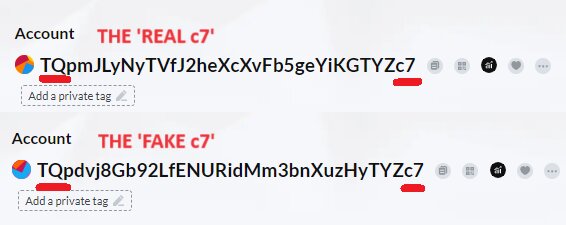
In this first phase, '5X' did a legit transfer to TqpmJLyNyTVfJ2heXcXvFb5geYiKGTYZc7, which we will call 'real c7' from now on. The scammers identified this transaction of 39,600 USDT on the Tron blockchain, done at 02:40 UTC on 10 October 2023. It is just one of many transfers between these two addresses, making '5X' the ideal victim for this type of attack.
Phase Two: Creating a Similar Tron Address
This is the phase in which scammers begin to prepare the premises of their evil plan. After verifying that there is repeated movement of funds between these two wallets, they create a new Tron address with the same initial and final characters as the 'real c7'.
The scammer's new address is 'Tqpdvj8Gb92LfENURidMm3bnXuzHyTYZc7', which we will call 'fake c7' from now on. This stage is the premise for the first contact between the scammers and the victim: he has set his trap and is about to make the first move.
Phase Three: The Scammers Send the Victim a Small Amount of USDT
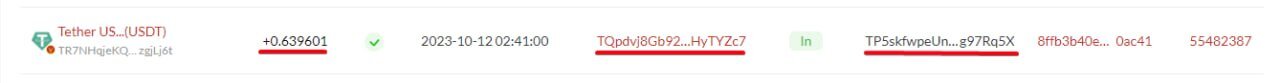
The scammers start the attack and first contact the unsuspecting victim. They send a small amount of USDT to the victim using the new address called 'fake c7. In our case, the scammers used a fake address ('fake c7') to send 0.639601 USDT to '5X'.
This move causes the scammers' address to be shown in the victim's transaction history. Usually, careless users, when making repeated transactions, copy the recipient's address from their transaction history for speed when sending money. This is a behavior that scammers understand very well, and they exploit people's bias in their favor. Being present in recent transactions, the scammers' 'fake c7' address, having the same beginning and ending characters as the 'real c7', has a good chance of being copied by the victim for future transactions.
Phase Four: Sending USDT by Mistake
This is where the scammers achieve their goal, stealing the victim's funds on the Tron Network and committing one of the most manipulative address poisoning attacks.
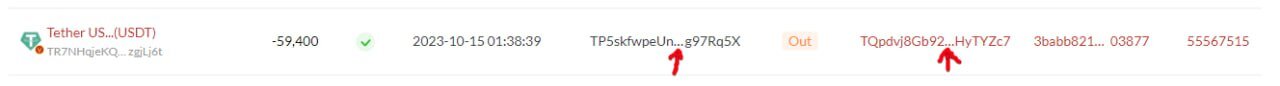
The victim, '5X', while making a usual transaction to 'real c7', inadvertently copies the address of the scammers ('fake c7'), from his transaction history. He verified only the first and last characters of the address without verifying the intermediate characters. This is a fatal mistake and delivers cryptocurrencies directly to scammers. This results from a studied and contrived manipulation of the victim's perception.
In the case study, in this transaction, we show that the victim '5X' mistakenly sent 59,400 USDT to 'fake c7', the scammers' address, which emulated the 'real c7'.
It is an irreversible phase; transactions on the blockchain cannot be undone, and the victim will never be able to regain possession of the cryptocurrencies. Is it possible to recover stolen funds? Unfortunately, it is improbable.
Phase Five: Automated Transfer of Funds to the Main Wallet
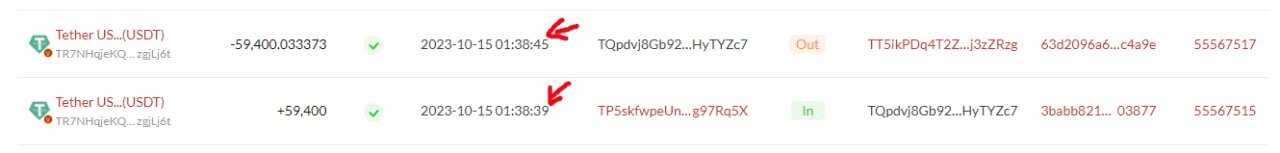
This is the final phase of the attack, and the scammers are now trying to hide any signs of the stolen money. They set up a bot on the 'fake c7' wallet that quickly moves the stolen funds to the scammers' main account in just 6 seconds. This step is really important because it helps the scammers disconnect the victim from the 'fake c7' wallet, gather all the money in one main account, and then make it vanish all at once.
In our case, this transaction, a bot sends the mistakenly received funds from "fake c7" to the scammers' main wallet, TT5ikPDq4T2ZB1CH7S3DcFmPR6ej3zZRzg.
We can see that the scammers' main wallet already has 629,389 USDT stolen from other frauds!
What Will the Scammers Do with the Stolen USDT?
Laundering the stolen USDT is a crucial step for scammers to obscure the origins of the funds and make them harder to trace. Here are some techniques they may use:
- Trading for Other Cryptocurrencies: Scammers may use cryptocurrency exchanges to trade the stolen USDT for other digital assets, such as Bitcoin, Ethereum, or privacy coins. These exchanges allow for asset swaps, making it challenging to trace the funds. Privacy coins, in particular, are designed to provide enhanced anonymity by concealing transaction details.
- Mixing Services: Cryptocurrency mixing or tumbling services are specialized platforms that take the stolen USDT and mix it with funds from various sources. These services break the link between the stolen USDT and its source, making it difficult for blockchain analysts to track the funds. Some mixing services may use CoinJoin or Confidential Transactions to enhance privacy.
- Peer-to-Peer Transactions: Scammers can engage in direct peer-to-peer (P2P) transactions with other users. P2P exchanges and platforms facilitate transactions without involving centralized intermediaries. These transactions can be more private, as they don't leave a trail on traditional exchanges. Scammers may also use encrypted communication channels to coordinate these transactions.
- Multiple Wallets: To add complexity to the trail of stolen USDT, scammers may spread the funds across various wallets. They might perform numerous internal transactions between these wallets, creating a web of transactions that is challenging to untangle. Each transfer between wallets could involve small amounts to obfuscate the movement of funds further.
Conversion to Fiat Currencies
- Cryptocurrency to Fiat Exchanges: Scammers can convert their ill-gotten USDT into traditional currencies like USD or EUR using cryptocurrency-to-fiat exchanges. These exchanges are regulated and require users to provide identity verification, but scammers often use fake or stolen identities to maintain anonymity. The converted fiat currency can be withdrawn to bank accounts.
- Over-The-Counter (OTC) Markets: OTC markets provide a less transparent method for converting cryptocurrencies to fiat. Scammers may find OTC buyers willing to trade cash for cryptocurrency in large quantities. These transactions occur outside traditional exchanges and are less likely to be monitored closely.
- Gift Cards and Vouchers: Scammers may use stolen USDT to purchase gift cards or prepaid vouchers, which can be used to buy various goods or services. Alternatively, they may sell these gift cards for cash. This method adds another layer of complexity to the movement of the funds.
Additional Strategies
- Offshore Accounts: Scammers may use offshore bank accounts in jurisdictions with lax regulations to further anonymize their funds. These offshore accounts can provide a level of legal protection and make it difficult for authorities to trace the origin of the funds.
- Investment and Asset Diversification: Some scammers may invest the stolen funds in assets like real estate, stocks, or businesses. These investments can distance the stolen assets from their illicit origins. Real estate, in particular, is often considered a desirable option for money laundering due to its potential for anonymity.
- Money Mules: Scammers may employ intermediaries or "money mules" to move and launder the funds. These individuals facilitate fund transfers, making it harder to trace the money back to the scammers.
In summary, scammers use a combination of tactics to obscure the origins of stolen USDT. They aim to create a complex and convoluted path for the funds, making it highly challenging for authorities, blockchain analysts, or victims to identify and track the perpetrators. Staying informed about these strategies and being cautious is essential for users to protect their digital assets and avoid falling victim to such scams. Combating these scams requires a coordinated effort among cryptocurrency platforms, regulatory authorities, and law enforcement.
In-Depth Analysis of Common Characteristics in USDT Scams
USDT scams, also called address poisoning attacks, on the Tron Network exhibit recurring patterns and common characteristics essential for cryptocurrency users to recognize and protect themselves. This chapter provides an extensive exploration of these shared traits to empower individuals with the knowledge to identify and defend against crypto dust attacks.
- Targeting Active Wallets: Scammers often select active wallets for fraudulent activities. These wallets belong to individuals engaged in frequent cryptocurrency transactions, such as traders, investors, or users participating in DeFi applications. By focusing on these wallets, scammers increase their chances of success due to the volume of transactions and potential targets.
- Mimicking Addresses: A prevalent tactic employed by scammers is the creation of fake addresses that closely resemble legitimate ones. Scammers carefully copy the initial and final characters of a target's wallet address, creating a near-identical mimic. To the untrained eye, these mimicked addresses can be virtually indistinguishable from genuine ones.
- The "Bait" Transaction: Scammers initiate contact with potential victims through a "bait" transaction. This initial transaction is usually of a small amount of USDT sent from the scammer's mimicked address to the victim. The objective is to test the victim's reaction and curiosity without raising immediate suspicion. The small size of the transaction may not prompt victims to scrutinize it closely.
- Exploiting User Behavior: USDT scammers are well-versed in typical user behavior, mainly copying recipient addresses from their transaction history. Users often do this to expedite future transactions. Scammers exploit this tendency by including their mimicked addresses in recent transactions, effectively "training" users to unwittingly select the scammer's address for future transfers.
- Cognitive Biases: Scammers take advantage of cognitive biases, and one of the most prominent is similarity bias. This bias leads individuals to focus primarily on the first and last characters of an address while paying less attention to the middle characters. The scammer's mimicked address leverages this cognitive bias, making it challenging for victims to detect discrepancies.
- Irreversible Transactions: The blockchain's immutability is critical in address poisoning attacks. Once a victim mistakenly sends their USDT to the scammer's address, the transaction is irreversible. Blockchain transactions are permanent and immutable by design, leaving victims with no recourse to recover their assets.
- Automated Fund Movement: Scammers deploy automated tools, such as scripts or bots, within their mimicked addresses. These tools are programmed to automatically transfer the stolen funds from the victim to the scammer's primary account. This automation allows scammers to break the connection between the victim and the mimicked address efficiently.
- Accumulation and Disappearance: In the final phase, scammers accumulate the stolen USDT in their primary wallet, consolidating the proceeds from multiple scams. After amassing a substantial sum, scammers may engage in various activities to further obscure their tracks.
Understanding the intricate common characteristics of crypto dust attacks is pivotal for cryptocurrency users to safeguard their assets and prevent falling victim to fraudulent schemes. By being well-informed, practicing caution, and developing an awareness of the strategies employed by scammers, users can significantly reduce the risks associated with address poisoning attacks on the Tron Network. Education and vigilance remain fundamental in protecting the cryptocurrency community from malicious actors and their deceptive tactics.
How To Protect Yourself From USDT Scams
Here are some tips to prevent fraud and be safe in the Web3 space:
- Verify Wallet Addresses: Before executing any cryptocurrency transaction, meticulously verify the recipient's wallet address. Pay close attention to each character and, when copying and pasting addresses, ensure there are no discrepancies or variations. Scammers often rely on minor alterations to mimic legitimate addresses.
- Use QR Codes: When possible, use QR codes to facilitate transactions. QR codes eliminate the need for manually entering an address, significantly reducing the risk of falling victim to address-mimicking scams. Ensure the QR code is sourced from a trusted and verified location, such as an official website or a secure application.
- Double-Check Transaction Details: Before confirming any cryptocurrency transaction, thoroughly review all transaction details, including the amount and recipient's address. Scammers may exploit users' haste to deceive them into sending funds to the wrong destination.
- Avoid Clicking on Suspicious Links: Exercise caution when encountering links, emails, or messages that prompt you to click on them. Scammers often employ phishing tactics to trick users into revealing sensitive information or downloading malicious software. If you are uncertain about the source, navigate directly to the website instead of clicking the provided links.
- Stay Educated: Maintain up-to-date knowledge about the latest scams and fraudulent techniques within the cryptocurrency space. Stay informed by following reputable sources, such as cryptocurrency news websites, forums, and social media channels where experts share insights and warnings about emerging scams.
- Use Security Software: Install robust security software and antivirus programs on your devices. Regularly update and scan your systems to detect and remove malware that may be utilized in scam attempts.
- Enable Two-Factor Authentication (2FA): Always activate two-factor authentication on your cryptocurrency exchange accounts, wallets, and other platforms where you store digital assets. 2FA adds an extra layer of security by requiring a secondary verification step for access.
- Keep Private Keys Secure: Safeguard your private keys and seed phrases. Store them securely, preferably offline, and maintain multiple physical copies. Never share this sensitive information with anyone; be cautious of any requests to disclose it.
- Utilize Two Wallets: Consider using two separate wallets. Use one wallet exclusively for day-to-day transactions and small balances. This wallet can be more easily accessible daily and may be connected to a debit card for everyday use, like PlasBit's wallet. Utilize a second wallet for secure storage, preferably a hardware wallet. Store most of your cryptocurrency holdings in this wallet, as it should be kept offline and only accessed when necessary. This wallet should have the highest level of security and protection.
- Beware of Unsolicited Offers: Exercise skepticism when confronted with unsolicited offers, particularly those promising substantial returns or requesting personal information. Scammers often use these offers as bait to lure individuals into their schemes.
- Report Suspicious Activity: If you encounter a potential address poisoning attack or fraudulent activity, promptly report it to relevant authorities and platforms. Many cryptocurrency exchanges and websites have mechanisms in place for reporting scams and suspicious users.
- Seek Legal Recourse: If you become a victim of a USDT scam, consider consulting with legal authorities. While the decentralized nature of cryptocurrencies can make recovery challenging, pursuing legal action can sometimes lead to positive outcomes.
- Share Information: Collaborate with the cryptocurrency community by sharing your knowledge and experiences. This community-based approach can help raise awareness and protect others from scams.
In conclusion, safeguarding against USDT scams on the Tron Network requires a combination of vigilance, awareness, and proactive security measures. We hope that in this PlasBit research, we have clarified how crypto dust attacks work and how to prevent them. By following these strategies and staying cautious, cryptocurrency users can significantly reduce the risk of falling victim to deceptive schemes and ensure the safety of their digital assets in the evolving world of cryptocurrencies.




.jpg)
.jpg)