Crypto romance scams exploit the profound desire for companionship, preying on the vulnerable and the unsuspecting. As we delve into the depths of this digital deception, it is crucial to recognize the amalgamation of trust, vulnerability, and financial entanglement that characterizes these scams. Through the lens of a real-life experience, PlasBit's research team will unravel the various stages of this intricate scheme, providing insights into the tactics employed by scammers to manipulate emotions and exploit financial innocence. Love, trust, and financial security are deeply intertwined in these narratives, making it imperative for individuals to navigate the digital ecosystem with an open heart and a vigilant mind.
The Trap Unfolds: A Detailed Look at a Real Case
Step 1: The Initial Deception
Our story begins with the protagonist, a 28-year-old individual navigating the complexities of life. In the digital realm, a seemingly innocuous "wrong number" message initiates a chain of events that will forever alter their course. The scammer, adopting the guise of an attractive Asian woman, strategically exploits the protagonist's initial skepticism and slowly gains their trust through a series of meticulously crafted messages. The victim, having previously received legitimate wrong number messages, fails to immediately discern the red flags that should have alerted them to the impending danger. This initial phase of the deception is marked by the artful creation of a persona that aligns with the victim's interests and desires, setting the stage for the following trap.
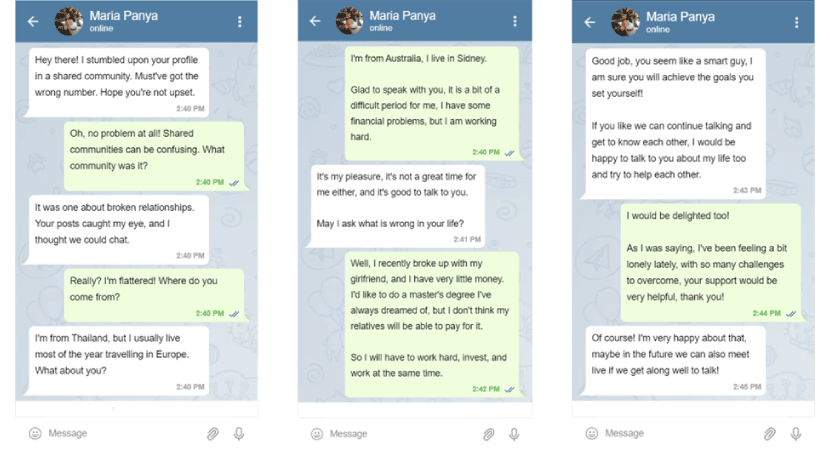
Step 2: Building a Virtual Bond
Loneliness and vulnerability become the fertile ground on which the scammer cultivates a virtual connection. The protagonist, seeking companionship, succumbs to the allure of the scammer's false identity. The scammer exploits the victim's trust by gradually revealing personal details, creating a sense of intimacy that transcends the digital world. Through clever manipulation, the scammer manipulates emotions like a puppeteer, leveraging the victim's desire for connection.
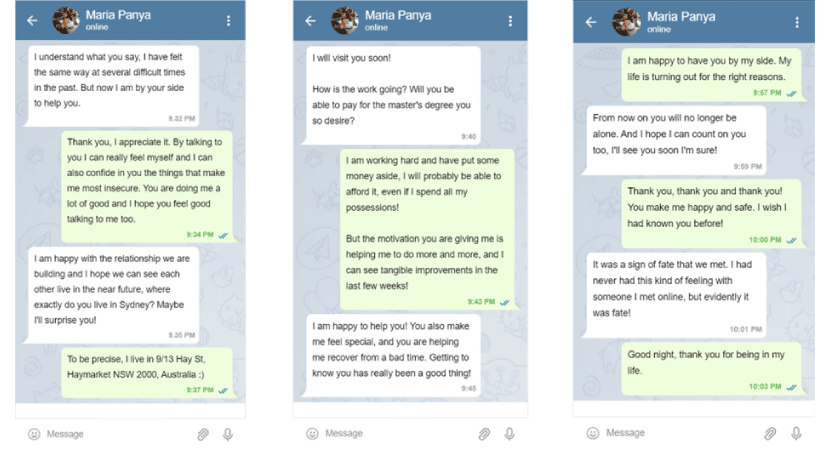
Step 3: The Cryptocurrency Investment
Unaware of the impending trap, the victim embarks on a financial journey initiated by the scammer's proposal. As the emotional connection deepens, the scammer introduces the concept of cryptocurrency investment, exploiting the victim's limited financial knowledge and capitalizing on their fears surrounding job insecurity. Fueled by a genuine desire for stability, the victim tentatively steps into the cryptocurrency arena. The emotional and financial consequences become increasingly apparent as the victim grapples with the aftermath of decisions made under the influence of meticulously orchestrated emotional manipulation.

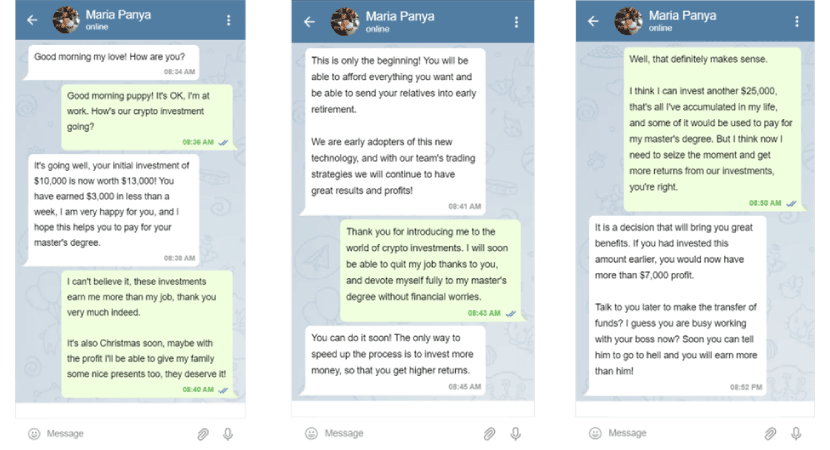
Step 4: Escalating Financial Commitments
With the initial crypto transfer made, the scammer skillfully guides the victim through a series of escalating financial commitments. Each step is strategically framed as a necessary progression to greater financial security. The victim, now ensnared in a complex web of promises and false assurances, unknowingly amplifies their financial exposure. As the victim navigates this fabricated investment scheme, the scammer artfully creates an illusion of success. Faux-progress reports and manipulated visuals are employed to simulate financial growth, reinforcing the victim's belief in the legitimacy of the venture. The investment scheme, designed to deceive, sets the stage for the climax of financial devastation.
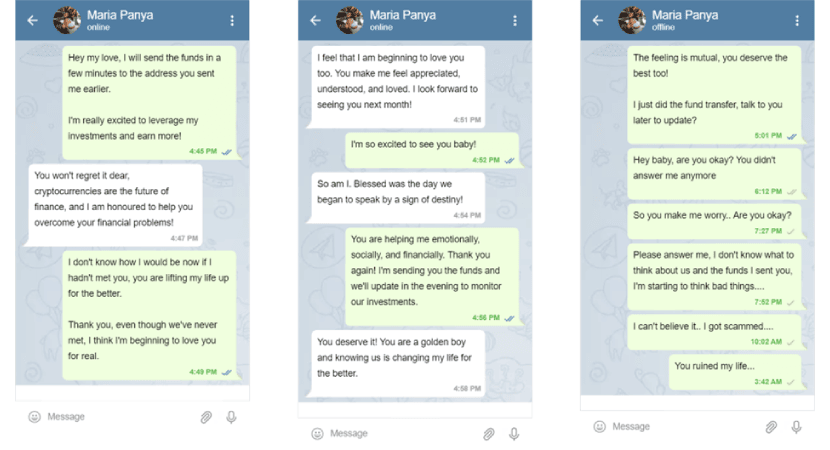
Step 5: Vanishing Act of Deception
As the financial commitment intensifies, a pivotal moment arrives when the scammer executes their vanishing act. The victim, trusting and hopeful, attempts to withdraw profits or seek clarity on the investment. However, communication from the scammer abruptly ceases. The once-attentive companion becomes elusive, and attempts to trace their digital presence yield nothing but empty voids. The victim is left grappling with the realization that the person they believed to be a confidant and partner in financial endeavors was nothing more than a mirage. The void left by the scammer's disappearance exacerbates the emotional turmoil, compounding the financial losses with a profound sense of betrayal. Tracking a crypto wallet is possible, but recovering the funds is almost impossible.
Protecting Yourself from Crypto Romance Scams
In the rapidly evolving crypto ecosystem, the rise of cryptocurrency has not only revolutionized financial transactions but has also given birth to a new breed of scams, including crypto romance scams. As online interactions become more prevalent, individuals seeking companionship can unwittingly fall victim to scams that exploit their emotions and financial vulnerabilities. We will explore the dynamics of this type of scam and offer comprehensive guidance on safeguarding yourself from these deceptive schemes.
Understanding Crypto Romance Scams
- The Allure of Romance: These scams typically begin with an individual establishing a romantic connection online. Scammers often create fake profiles on dating platforms, social media, or even dedicated crypto forums to lure unsuspecting victims into emotional relationships.
- Introduction to Cryptocurrency: Scammers use cryptocurrency's allure to add complexity to their schemes. They may claim to be involved in lucrative crypto investments, promising substantial returns or exclusive opportunities.
- Emotional Manipulation: Scammers excel in emotional manipulation, exploiting the vulnerability and trust of their victims. They may craft elaborate stories about personal hardships or financial struggles, creating a sense of sympathy and emotional dependence.
Recognizing Warning Signs
- Too Good to Be True: Be skeptical of overly positive and extravagant promises. Exercise caution if a new online connection offers quick and substantial financial gains through cryptocurrency.
- Anonymity and Evasiveness: Scammers often avoid revealing personal details or meeting in person. Consider it a red flag if your online connection is reluctant to share information about your identity and background.
- Requests for Financial Assistance: One of the most prominent signs of a crypto romance scam is the request for money. Scammers may fabricate emergencies or investment opportunities, urging victims to send cryptocurrency under the guise of helping them.
Protecting Yourself
- Research and Verification: Conduct thorough research on your online connection before investing time or emotions. Verify their identity, cross-reference information, and be cautious if inconsistencies emerge.
- Educate Yourself on Cryptocurrency: Equip yourself with a basic understanding of cryptocurrency. This knowledge will empower you to identify unrealistic promises and questionable investment schemes.
- Never Share Private Keys: Under no circumstances should you share your cryptocurrency private keys. Legitimate individuals will not request this information, and sharing it could result in losing your funds.
- Be Skeptical of Unsolicited Investment Opportunities: If someone you've just met online presents a sudden and unsolicited investment opportunity, approach it with skepticism. Consult with financial advisors or trusted friends before making any financial decisions.
- Report Suspicious Activity: If you suspect you are a target of a crypto romance scam, report the incident to the platform where you met the individual and, if applicable, to law enforcement agencies.
Motivations Behind Crypto Romance Scams
Understanding the psychological and emotional drivers that lead individuals into the snares of crypto romance scams is crucial for devising effective preventative measures. We will delve into the intricate motivations that scammers exploit to manipulate their victims, shedding light on the vulnerabilities that make individuals susceptible to these deceptive schemes.
Emotional Vulnerability and Loneliness
- Isolation and Longing: Many individuals seeking companionship through online platforms often experience a sense of isolation or loneliness in their lives. The desire for connection and intimacy can cloud judgment, making them more susceptible to the emotional manipulation employed by scammers.
- Escaping Reality: In some cases, individuals may be drawn to online relationships as a means of escape from real-life challenges or hardships. Scammers adeptly exploit this vulnerability by weaving narratives that provide an alternate, seemingly idyllic reality.
Financial Desperation
- Economic Struggles: Economic hardships can create a fertile ground for scammers to exploit. Individuals facing financial difficulties may be enticed by promises of quick and substantial returns, especially when presented in the enticing guise of cryptocurrency investments.
- Hope for Financial Improvement: Scammers play on the universal desire for financial improvement. By weaving tales of lucrative crypto opportunities or exclusive investments, they tap into the hope for a better financial future, enticing victims to part with their funds.
Trust in Online Platforms
- Perceived Security: Users often place implicit trust in the security measures of online platforms, assuming that the individuals they meet have undergone some form of vetting. Scammers exploit this trust by creating fake profiles that appear genuine and trustworthy.
- False Sense of Connection: The virtual nature of online interactions can create a false sense of connection. Victims may believe they have developed a deep bond with their online companions, making them more susceptible to financial requests disguised as acts of mutual support.
Lack of Crypto Literacy
- Unfamiliarity with Cryptocurrency: Many individuals, particularly those new to cryptocurrency, may lack the necessary literacy to discern legitimate investment opportunities from scams. Scammers leverage this lack of knowledge to introduce complex and fraudulent crypto schemes.
- Intimidation by Technology: The intricate nature of cryptocurrency and blockchain technology can be intimidating for some users. Scammers exploit this intimidation, creating an environment where victims feel compelled to trust the expertise of their online companions.
Social Engineering Tactics
- Personalized Manipulation: Scammers invest time and effort in tailoring their approaches to the individual profiles of their victims. By learning about personal struggles, aspirations, and fears, they can craft narratives that resonate deeply, heightening the emotional impact.
- Building False Trust: Scammers excel in building false trust through consistent communication and feigned emotional investment. Victims may be led to believe that their online companions genuinely care for them, making them more likely to comply with requests for financial assistance.
Conclusion
As explored also in crypto giveaway scams, crypto romance scams thrive on exploiting human vulnerabilities, both emotional and financial. By understanding these motivations, individuals can better equip themselves to identify and resist the manipulative tactics employed by scammers. Education, emotional resilience, and a healthy skepticism toward unsolicited online advances are powerful tools in the fight against scams.
Navigating the Spectrum of Common Crypto Scams
As the popularity of cryptocurrencies continues to rise, so does the ingenuity of scammers seeking to exploit unsuspecting individuals. We aim to provide an extensive exploration of various common crypto scams, shedding light on their intricate methods and offering insights into how individuals can safeguard themselves from falling victim to these deceptive practices.
Phishing Scams
- Email Phishing: Phishing involves deceptive attempts to acquire sensitive information such as usernames, passwords, or private keys. Scammers often send fraudulent emails masquerading as reputable entities, urging recipients to click on malicious links or disclose confidential information.
- Fake Websites: Fraudulent websites imitating legitimate crypto exchanges or wallets are prevalent. Unsuspecting users may land on these sites, unknowingly providing access to their accounts. Always verify website URLs and use two-factor authentication for added security.
Pump and Dump Schemes
- Coordinated Market Manipulation: In pump-and-dump schemes, groups artificially inflate the price of a cryptocurrency through coordinated buying. Once the price peaks, they swiftly sell off their holdings, causing a market crash and leaving unsuspecting investors with significant losses.
- Unrealistic Profit Promises: Scammers promoting pump-and-dump schemes often entice investors with promises of quick and substantial profits. Vigilance and skepticism regarding sudden price spikes are crucial to avoid falling prey to these manipulative tactics.
ICO and Token Sale Frauds
- Fake Initial Coin Offerings (ICOs): Scammers create fraudulent ICOs, enticing investors to contribute funds to a non-existent or worthless project. Thorough due diligence, including scrutinizing the project team and evaluating the viability of the proposed concept, is essential.
- Token Sale Impersonation: Impersonating legitimate token sales or airdrops, scammers trick users into sending funds to fake addresses. Always verify the authenticity of token sales through official channels and be cautious of unsolicited offers.
Fake Crypto Wallets
- Malicious Downloads: Scammers develop fake crypto wallet apps or software, often distributed through unofficial channels. Unsuspecting users may download these applications, compromising the security of their digital assets. Stick to official wallet providers and app stores.
- Hardware Wallet Tampering: Even physical cold wallets are not immune to scams. Purchasing from unauthorized or unverified sources can expose users to tampered devices designed to steal private keys. Always buy hardware wallets from reputable vendors.
Social Media Impersonation
- Fake Celebrity Endorsements: Scammers capitalize on the trust associated with celebrities by creating fake endorsements. They promote fraudulent schemes, enticing users to invest in fake projects. Verify endorsements through official channels and be skeptical of unsolicited investment advice.
- Impersonating Influencers: Influencers in the crypto space are sometimes targeted for impersonation. Scammers create fake profiles to engage with followers, promoting scams or fraudulent giveaways. Confirm the authenticity of accounts and never send funds based on unsolicited messages.
Address Poisoning Attack
- Manipulating Receiving Addresses: Address poisoning, also known as crypto dust attack, involves altering the recipient's crypto address during transactions. Scammers may intercept communication or compromise the device, replacing the recipient's address with their own. Always double-check the recipient's address before confirming transactions.
- Using Secure Channels: To mitigate the risk of address poisoning, use secure communication channels and verify the accuracy of crypto addresses through multiple sources. Be cautious of sudden changes in transaction details, and never rely solely on a single source for address information.
As the crypto landscape evolves, so too do the tactics employed by scammers. Being aware of common crypto scams, including the emerging threat of address poisoning attacks, is the first line of defense. Vigilance, skepticism, and thorough research are key elements in safeguarding oneself from falling victim to these deceptive practices. In the final chapter, we will consolidate insights and provide a comprehensive set of guidelines to empower individuals to navigate the crypto space securely.

Safeguarding Your Crypto Assets: A Call to Education and Vigilancee
As we conclude our exploration of the multifaceted landscape of common crypto scams, it becomes evident that education and vigilance are the linchpins of effective protection against deceptive practices. We emphasize the paramount importance of staying informed and share practical tips to fortify the security of your crypto assets.
The Power of Education
- Continuous Learning: Cryptocurrency and blockchain technology are dynamic fields. PlasBit security's team is always recommend staying informed about the latest developments, security protocols, and emerging threats. A well-informed individual is better equipped to navigate the complexities of the crypto space.
- Community Engagement: Engage with the crypto community through forums, social media, and reputable news sources. Sharing experiences, insights, and cautionary tales contributes to the collective wisdom that protects users from falling victim to scams.
Practical Tips for Security
- Secure Your Private Keys: Your private keys are the gateway to your crypto assets. Keep them confidential, and never share them with anyone. Store them in secure, offline environments like hardware wallets for enhanced protection.
- Two-Factor Authentication (2FA): Enable 2FA on all applicable accounts. This additional layer of security adds a crucial barrier for scammers attempting unauthorized access to your accounts.
- Verify Transactions: Before confirming any crypto transactions, meticulously verify the recipient's address. Use secure communication channels and cross-check details through multiple sources to avoid falling victim to address poisoning attacks.
- Use Reputable Wallets and Exchanges: Stick to well-established and reputable wallets and exchanges. Research and read reviews before choosing a platform, and be cautious of unsolicited recommendations.
- Stay Skeptical of Unrealistic Gains: Be wary of promises of unrealistically high profits or guaranteed returns. It likely is if an investment opportunity sounds too good to be true. Conduct thorough research before committing funds.
- Report Suspicious Activity: If you encounter suspicious profiles, scams, or fraudulent schemes, report them to the relevant authorities and platforms. Your vigilance can help protect others from falling victim to the same scams.
- Regularly Update Software: Keep your software, including wallets and security tools, up to date. Developers frequently release updates to address vulnerabilities and enhance security.
- Diversify Your Investments: Avoid putting all your crypto assets into a single investment or platform. Diversifying your holdings can mitigate the impact of potential losses in any one area.
Conclusion: A Secure Crypto Future Begins With You
As we navigate the ever-evolving landscape of cryptocurrencies, the responsibility for securing our assets rests firmly in our hands. By fostering a culture of continuous learning, engaging with the community, and implementing practical security measures, individuals can fortify themselves against the myriad scams that threaten the crypto space. Remember, a secure crypto future begins with you. Stay informed, stay vigilant, and empower yourself to safeguard your digital assets in this exciting but complex world of cryptocurrencies.







