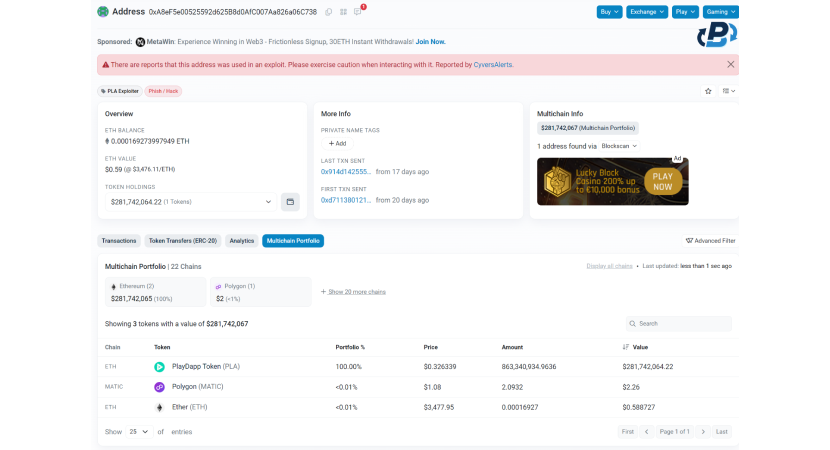
The cryptocurrency world has huge inherent risks, including asset volatility, scams, and hacker attacks. Recently, the hacker attack on PlayDapp has become a particularly interesting case study, especially because of how the team is handling the situation.
As we apprehended in this PlasBit's research about PlayDapp security breach, in the hacker attack on February 9, 2024, one or more scammers minted 200 million PLA tokens worth $36,500,000. They used a compromised wallet, probably managing to recover its private key for access. The PlayDapp team promptly acted on the hacker attack, offering the scammer a $1,000,000 reward if it would return the improperly minted and stolen tokens. The story does not end here; let's explore it further because there may be a positive end!
PlayDapp Security Breach: How was PlayDapp's Smart Contract Hacked?
The well-known blockchain gaming platform PlayDapp was severely hacked in February. Altogether, two attacks occurred that took a sum of about $300,000,000 worth of PLA tokens. How did the smart contract exploit happen?
- Vulnerability: The attack stemmed from an access control vulnerability within one of the main wallets that control PlayDapp's smart contracts, managing to recover its private key. This vulnerability essentially allowed the attacker to bypass security measures and grant themselves unauthorized privileges.
- Exploiting the Vulnerability: By exploiting this vulnerability, the attacker could add themselves as authorized minter for the platform's token (PLA).
- Minting and Stealing: With minting authority, the attacker had the ability to create new PLA tokens at will. These newly minted tokens were then transferred to the attacker's wallet, effectively stealing funds from the platform.
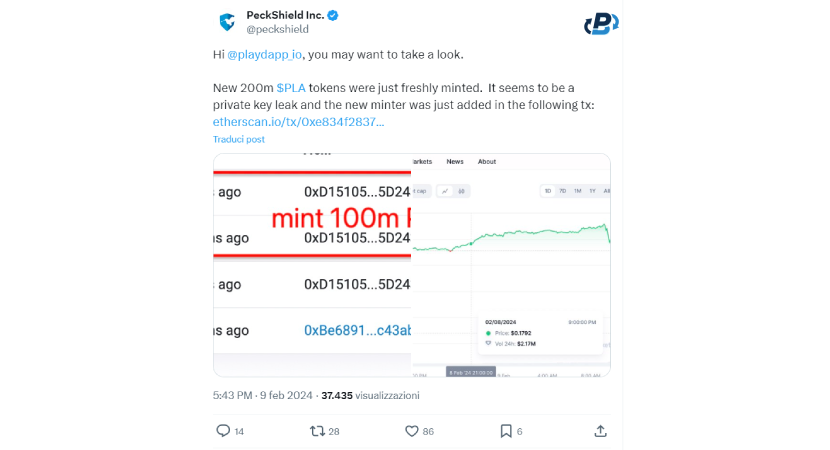
On February 8, the blockchain data and analytics firm PeckShield reported the exploit with an alarming tweet. They found an unusual mint of 200,000,000 PLA!
What did PlayDapp do to Address the Situation?
In response to the breach, PlayDapp quickly initiated measures to contain the situation. These actions included communicating with partner exchanges to suspend trading activities and preventing further exploitation of the vulnerabilities. In addition, PlayDapp contacted the hacker directly, offering a reward for the immediate return of stolen contracts and assets. In this way, they managed to keep PLA tokens from being sold to scammers easily on any exchange, however, the supply and token economy was altered, and the risk of subsequent token transfers remained. As if that were not enough, the hacker did not stop there.
The Hacker Attacked Again on February 12!
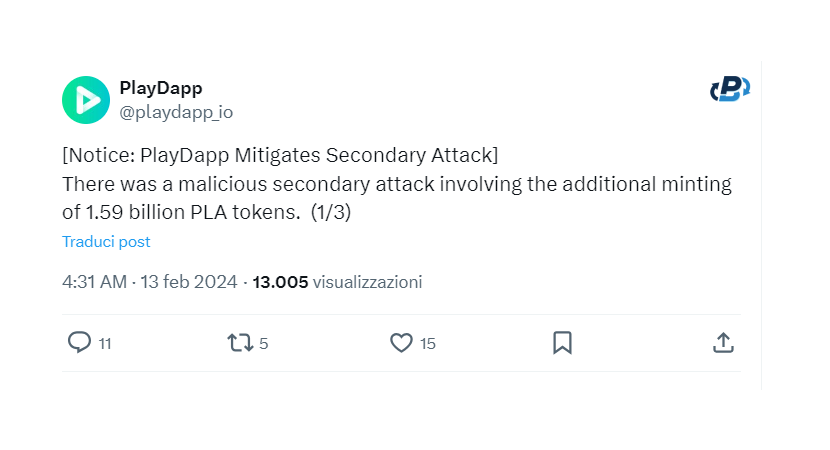
To make matters worse, although PlayDapp offered $1,000,000 to the scammer, this was not enough to resolve the situation. Having blocked all token transfers, however, the team handled the situation in a relatively healthy manner. But, on February 12, the scammers attacked again by minting another 1,590,000,000 PLA tokens, totaling about $255,000,000! These are serious numbers, but it would not have been easy for the hackers to exchange the loot for fiat currencies or other cryptocurrencies, the cryptocurrency's smart contracts being locked for protection.
How Has This Impacted the Price of PLA?
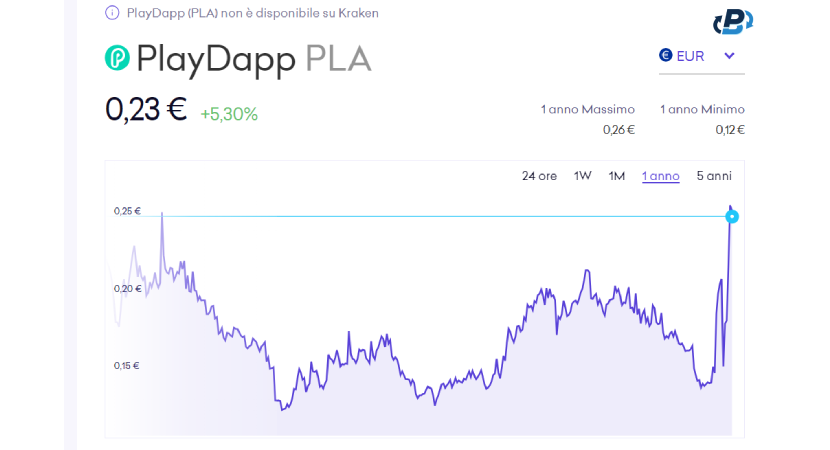
The price of the token, before they blocked all smart contracts, dropped from $0.182 to $0.148, but the trading volume quickly rose from less than $3 million to more than 60, unbelievable! Blocking trading on all the top exchanges helped cushion the risks of a collapse in price and investors' capital in the short term. Nevertheless, this would not have been enough to get the project back on track.
What Happened to the Stolen Funds?
The scammer's wallet has been reported on most of the exchanges, as the PlayDapp team promptly asked decentralized and centralized exchanges to block the scammer's address and make it impossible for them to convert the stolen funds. So, the funds remained locked in the scammer's wallet, except for a small amount, which, following the movements between wallets, arrives on an anonymous exchange application called FixedFloat. The peculiar thing that makes this case study even more interesting is that this specific cryptocurrency broker, FixedFloat, was a few days later exploited by 1800 ETH!
How Was the PlayDapp Security Breach Solved?
After promptly reacting to fix the problem, the incident caught the attention of the crypto community, and many new people joined PlayDapp. This caused the price of the token to rise, recovering and growing even higher than the price at the time of the hack. In a long article on their Medium blog, they explained how they are solving the problem: Through a migration of the token from PLA to PLD. Although this is a comprehensive mechanism, it may actually be the only concrete solution that solves the problem for good, considering that the hacker has no intention of returning the minted and stolen PLA tokens.
How Will the Migration from PLA to PDA Work?
The migration from PLA to PDA tokens is a crucial step undertaken by PlayDapp in response to a smart contract hack resulting in the issuance of 1.79 billion invalidly minted PLA tokens. Here's how the migration process will unfold:
1. Safeguarding Assets: PlayDapp is transferring all PLA tokens, including locked and unlocked holdings, to a new secure wallet for asset protection.
2. Suspension of Deposits and Withdrawals: Prompt communication with CEXes has enabled the suspension of deposits and withdrawals, minimizing potential losses.
3. Temporary Pause of PLA Smart Contract: The PLA smart contract is temporarily paused. A migration has been conducted based on a snapshot.
4. Collaboration with Coordinated CEXes: PlayDapp has collaborated with some CEXs to facilitate migration from PLA to PDA. Holders of PLA tokens on these exchanges will receive PDA tokens at a 1:1 ratio based on the snapshot timing.
5. Migration Portal for Other Holders: PLA holders who don't have wallets on coordinated CEXes can use a Migration Portal to initiate their migration process at a later date.
6. KYC Certification: Holders undergoing migration will complete KYC certification for AML compliance to ensure security and legitimacy.
7. Migration to PDA: After completing the KYC verification process, PDA tokens will enter a pending distribution status. Once the distribution is completed, users can confirm the on-chain distribution, and the requested PDA tokens will be delivered to their designated Ethereum wallet address.
8. Migration Period: The migration period will last for 24 months from the start date. Migration through the Migration Portal will be available for 12 months. Holders will receive an additional 12 months of customer service support after this period.
Is it so easy to hack cryptocurrencies? Fortunately not, but smart contracts must always be verified by an experienced audit team to avoid these hacks. In summary, the migration process from PLA to PDA tokens is meticulously designed to ensure the security and integrity of assets while providing a seamless transition for token holders. PlayDapp remains committed to transparent communication and continuous updates throughout the migration process.
What Exactly is PlayDapp?
PlayDapp is a gaming and gaming development platform that enables blockchain games to be accessible to everyone. By developing both their own interoperable games and supporting other companies' innovation through blockchain, they position themselves as potential leaders in decentralized blockchain games. The team, although it should have acted proactively to avoid revealing access to the private keys of an important wallet for the use of smart contracts, seems to have reacted well to the attack and promptly used all strategies and measures to contain the damage, which pleased the community.
What is the Mission of PlayDapp?
PlayDapp wants to allow users who are unfamiliar with cryptocurrencies and who only interact with Web2, for now, to use their platform to participate in Web3 games without the need to transact with cryptocurrencies. This denotes a great devotion to the inclusiveness of their platform and to fostering a gradual and increasing adoption of blockchain solutions through a user-friendly experience.
What is PlayDapp SDK?
The PlayDapp SDK service is designed to assist developers and companies facing challenges in building Web3 infrastructure by enabling them to connect their assets or desired digital items easily through a straightforward integration system.
Here's what the PlayDapp SDK offers:
- Simplified Integration: The PlayDapp SDK provides developers with the necessary tools to seamlessly integrate their assets or digital items with Web3 infrastructure. This reduces the time and effort required to implement the desired connection.
- Data 3.0 Conversion: The service enables data conversion into the 3.0 format, ensuring compatibility and interoperability with other Web3 services and platforms.
- Interoperable Data between Services: The PlayDapp SDK facilitates data exchange and sharing between different Web3 services and platforms, enabling better collaboration and integration within the ecosystem.
- Data 3.0 Management & Operational Tools: The service provides users with the necessary tools to manage and operate 3.0 data efficiently and securely.
- Integration with Web3 C2C Marketplace: The PlayDapp SDK supports the integration of data and assets with Web3 peer-to-peer (C2C) marketplaces, enabling users to buy, sell, and trade securely and reliably.
- Web3 Indicators & Data Analytics Dashboard: The service offers a comprehensive dashboard for monitoring indicators and analyzing Web3 data, allowing users to gain a clear overview of their Web3 ecosystem's performance and trends.
- Ecosystem Participation Reward: The PlayDapp SDK provides incentives for active participation in the Web3 ecosystem, rewarding users who contribute to its development and growth.
In summary, the PlayDapp SDK is a comprehensive solution to simplify and optimize the integration of assets and data with Web3 infrastructure, enabling developers and companies to fully leverage the potential of blockchain and decentralized technologies.
How do Smart Contracts work, and How are they Exploited?
Smart contracts are computer programs that automatically execute the terms of a contract between two parties. They are self-executing and operate on the blockchain, which is a decentralized and immutable ledger. The terms of the contract are encoded in lines of code, and the smart contract executes actions when predetermined conditions are met. Smart contracts offer several benefits, such as automation, transparency, and security, as they eliminate intermediaries and provide a tamper-proof system. However, smart contracts are not entirely immune to exploitation, and understanding how they work and how they can be exploited is essential in navigating the world of decentralized finance (DeFi) and blockchain technology. PlasBit emphasizes that smart contracts are not a replacement for traditional contracts but instead offer a complementary solution for specific use cases.
How Smart Contracts Work
- Decentralized Execution: Smart contracts operate on a decentralized network of nodes, meaning there is no central authority controlling their execution. Transactions are validated and recorded by multiple nodes, ensuring transparency and immutability.
- Code is Law: The terms of a smart contract are encoded into its underlying code, and once deployed on the blockchain, they cannot be altered. This "code is law" principle ensures that transactions are executed exactly as programmed, without the need for intermediaries.
- Automatic Execution: Smart contracts automatically execute predefined actions when certain conditions are met. For example, in a decentralized exchange (DEX) smart contract, the contract will automatically swap tokens between parties once a trade is initiated.
- Immutable Record: Every transaction and interaction with a smart contract is recorded on the blockchain, creating an immutable record of all activities. This transparency enhances trust among users and reduces the risk of fraud.
How Smart Contracts Are Exploited
- Code Vulnerabilities: Smart contracts are susceptible to bugs and vulnerabilities in their code, which can be exploited by malicious actors. Common vulnerabilities include reentrancy attacks, integer overflow/underflow, and improper access control.
- Front-Running: Front-running occurs when a malicious user exploits the time delay between the submission of a transaction and its inclusion in a block. By observing pending transactions, attackers can insert their own transactions with higher gas fees to prioritize their execution and profit from price discrepancies.
- Oracle Manipulation: Smart contracts often rely on external data sources called oracles to trigger certain actions. Malicious actors can manipulate these oracles by providing false or misleading information, leading to incorrect contract executions.
- Insufficient Security Audits: Smart contracts should undergo thorough security audits by experienced professionals to identify and mitigate potential vulnerabilities. Contracts deployed without proper auditing are at a higher risk of exploitation.
- Social Engineering: In addition to technical vulnerabilities, smart contracts can also be exploited through social engineering tactics. Phishing attacks, fake token sales, and rug pulls are examples of social engineering exploits targeting unsuspecting users.
In conclusion, while smart contracts offer many advantages in terms of automation and transparency, they also introduce new risks and challenges. Understanding how smart contracts work and the potential avenues for exploitation is essential for developers, investors, and users.

Preventing Involvement in Hacker Attacks and Smart Contract Exploits
Recently, hacker attacks and smart contract exploits have become a growing threat. Understanding best practices to protect your funds and prevent involvement in malicious activities is essential for ensuring financial security.
Use Secure Hardware or Software Wallets
- Hardware wallets like Ledger and Trezor offer a higher level of security by keeping private keys offline, away from potential online attacks.
- Software wallets like MetaMask and other anonymous BTC wallets are also secure when used correctly, but it's crucial to keep both the wallet software and the device used up to date.
Securely Store Private Keys
- Private keys are essential for accessing funds, so they must be stored securely and not shared with anyone.
- Avoid storing private keys on devices connected to the internet or in insecure environments.
Use Two-Factor Authentication (2FA)
- Enabling two-factor authentication (2FA) adds an extra layer of security by requiring a second verification method, such as a code sent via SMS or an authentication app.
Avoid Untrusted Exchanges and Platforms
- Choose trusted exchange platforms and wallets with a proven track record of security and reliability.
- Avoid using decentralized exchanges (DEX) without adequate research and understanding of the security measures in place.
Beware of Phishing Emails and Websites
- Exercise caution when responding to suspicious or phishing emails that request sensitive information or attempt to induce harmful actions.
- Always verify the URL of websites and ensure that you use only official and secure sites for transactions.
Keep Devices and Software Updated
- Ensure all devices used to access funds are updated with the latest security patches.
- Also, keep wallet and application software updated to manage cryptocurrencies.
Conduct Smart Contract Audits
- Before interacting with a smart contract or DeFi platform, conduct thorough research and verify that the contract has undergone security audits by industry experts.
- Avoid interacting with unverified contracts or those whose reliability is unknown.
Diversify Investments and Reduce Risk Exposure
- Diversifying cryptocurrency investments reduces the overall risk associated with holding a single asset.
- Avoid investing more than you can afford to lose and maintain a significant percentage of the portfolio in more stable assets.
Stay Vigilant and Act Promptly in Case of Issues
- Regularly monitor wallet activity and act promptly in case of suspicious transactions or anomalous activities.
- Report any issues promptly to relevant authorities and seek assistance from reliable and trustworthy sources.
Adopting these security practices to protect your wallet and assets significantly enhances fund protection and reduces the risk of involvement in hacker attacks and smart contract exploits. Awareness, caution, and the adoption of preventive measures are crucial for keeping cryptocurrencies safe in an increasingly complex digital environment.
Opting for Reliable Platforms with Proven Proof of Reserve
As we have verified in this research, the cryptocurrency world is full of dangers and possible security holes. As demonstrated by the analyzed case study of the PlayDapp security breach, the risks in using Web3 platforms with insecure smart contracts are high. Users should always do thorough research before making investments in tokens and cryptocurrencies: DYOR, do your own research. In fact, although all hacker attacks are impossible to avoid, users should pay attention to all red flags of possible projects. A good team should act proactively and install strict security measures that prevent possible smart contract exploits. Users, therefore, before investing in a platform, have a duty to carefully check the reputation of the team behind the project and research whether smart contracts have been audited securely by a competent team.
Some Others Platforms Hacked or Failed
For both Dapps, decentralized exchanges (DEX) and centralized exchanges (CEX), security is paramount. When doing your research to choose which platform to use, keep in mind that your assets must always be safe and that you cannot risk losing them beyond repair. For example, if you had invested in PlayDapp, although the team is progressively managing to find a solution to the issue, you would not have been able to sell your assets, and even now, you probably could not convert them back into the fiat consideration. Numerous other instances of this type have occurred, including for many exchanges, as happened to FixedFloat a few days after the PlayDapp incident. At FixedFloat, an intermediary platform for cryptocurrency exchanges, an attacker who was probably part of the team as a dev emptied the exchange accounts for the absurd amount of 1800 ETH. Another famous example is the collapse of the FTX exchange. In this case, the platform made illegal and improper use of users' funds and sadly imploded on itself, leaving many investors deprived of their funds and investments. Losing one's money in this way is no joke, and many people, as in the case of the collapse of Terra (LUNA), have lost their homes, committed suicide, and other dramatic acts. Remember that, right now, the most secure cryptocurrency is Bitcoin.
Prioritize to Check Proof of Reserve
The only way to safeguard yourself and use a secure platform is to verify that they have a clear and secure proof of reserve. Proof of reserve is a sum of funds that platforms keep as the counter value of money invested by users. Every self-respecting platform has a ratio of user assets to retained assets of at least 1:1. In the cases of the most secure platforms, as we do at PlasBit, for example, the platform's funds are clearly separated from the users' funds. In fact, on our site, we store only the platform's operational money online, have other reserves in cold wallets, and, most importantly, we store user assets securely backed with a 1:1 ratio distributed among various cold wallets. We hope you found this educational research guide helpful in understanding how PlayDapp was hacked and how the team responded to the attack with relatively good readiness and transparency. However, we emphasize, once again, the importance of using secure platforms with clear and convincing proof of reserve.