In the era of unparalleled connectivity and digital innovation, mobile devices have seamlessly integrated into the fabric of our daily lives. While these pocket-sized marvels enhance our productivity, keep us entertained, and facilitate instant communication, they also serve as a breeding ground for a new frontier of illicit activities: Common scams on mobile devices. As the prevalence of smartphones and tablets continues to rise, so does the ingenuity of scammers seeking to exploit unsuspecting users. In PlasBit's research, we will journey through the intricate complexities of common scams that plague mobile devices. From identity theft to financial fraud, understanding the intricacies of these schemes is paramount to safeguarding our digital lives.
Unraveling the Complexity of Mobile Device Scams
We will delve into the intricate nature of mobile device scams, exploring why they are dangerous and how users can defend themselves.
Defining Mobile Device Scams
Common scams on mobile devices are deceptive schemes designed to exploit vulnerabilities through smartphones and tablets. These deceptions can take various forms, from fake text messages and fraudulent calls to sophisticated fraudulent apps and phishing attempts. The ultimate goal of such scams may vary, but it often involves acquiring personal and financial information or gaining complete control over the user's device.
Why Mobile Device Scams Are Dangerous
Access to Sensitive Information: Mobile devices contain a vast amount of personal information, including banking data, sensitive login information, emails, and more. Targeted scams can enable attackers to access this information, paving the way for identity theft or financial fraud.
Risk of Malware and Spyware: Some scams aim to infiltrate devices with malware or spyware, allowing attackers to monitor user activities without consent. This invasion of privacy can have severe consequences, including the potential for recording conversations, accessing the camera, and more.
Financial Frauds: Mobile device scams often aim to deceive users into fraudulent financial transactions. It may include unauthorized purchases, misleading subscriptions, or demands for payment in exchange for threats of device damage or disclosure of personal information.
App Vulnerabilities: With the proliferation of apps, the vulnerability of installing malicious applications has increased. Scams may involve fake apps that appear legitimate but, in reality, gather sensitive information or harm the device.
A Case Study: SEC's Twitter Account Sim Swap Scam
A notable case study that happened yesterday is the alleged hacking of the SEC account.
What is the Context of this Evil Manipulation?
These are days of anticipation and excitement for the cryptocurrency world. The approval of the world's first Bitcoin ETF is being discussed in these hours, and its confirmation could bring a significant influx of capital and increase global adoption. It could be the so-called 'Crossing the Chasm' of Moore's technology adoption curve.
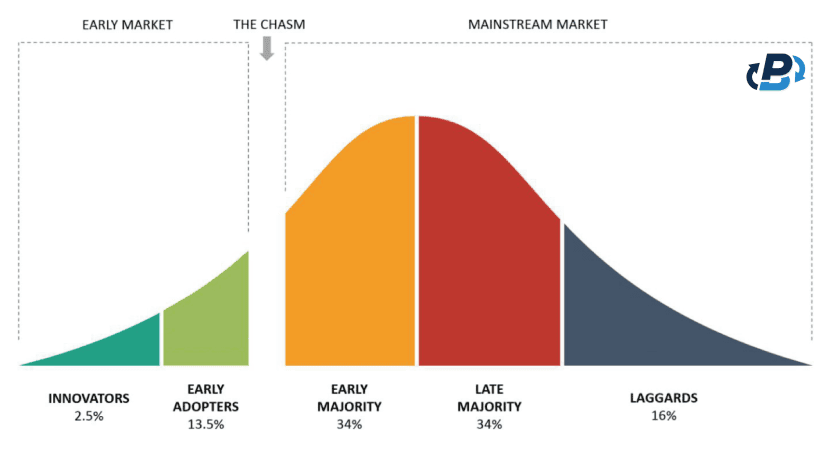
The Long-awaited Announcement: A Lie.
At 22:11 CET on 9 January 2024, the long-awaited announcement arrived. From the official SEC account, it is published.
"Today, the SEC grants approval for Bitcoin ETFs to be listed on all registered national securities exchanges.
The approved Bitcoin ETFs will be subject to ongoing surveillance and compliance measures to ensure continued investor protection."
It seems that a major turning point has been reached in the world of cryptocurrencies, but it hasn't: the Twitter account of the main investor protection body, the SEC, has been hacked, and the tweet is fake.
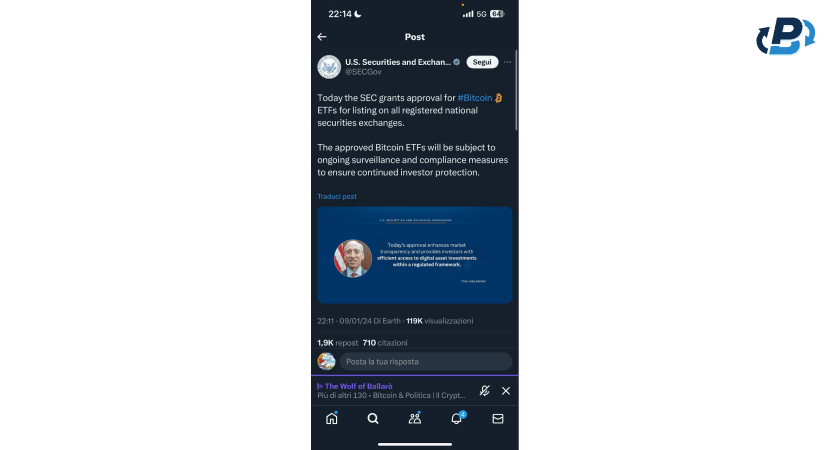
Gary Gensler's Denial
A few minutes later, after a major market reaction, came the denial of SEC chairman Gary Gensler. In his tweet, he admits that the Twitter account was hacked and that no Bitcoin ETF was approved. Plausible?
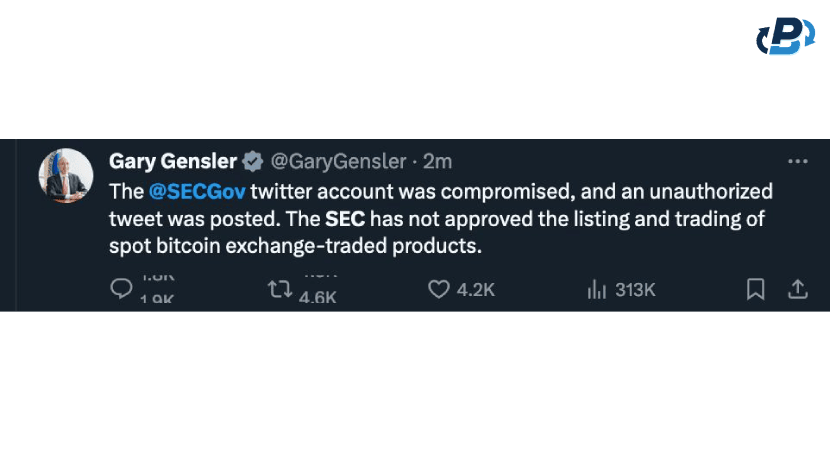
How Could this Happen? A Sim Swap Scam
One possible explanation comes from the security consultant called on Twitter @Plumferno.
Apparently, the SEC account was hacked despite two-factor authentication via a sim swap scam. The hacker duplicated the phone sim of the number associated with the SEC's Twitter account and posted the fake news to manipulate the market and profit heavily from the caused market volatility.
What is left of this story?
Even one of the most secure Twitter accounts in the world was hacked via a common mobile phone scam. There are many rumors about possible deliberate market manipulation or insider trading, but at the moment, the official explanation is a simple mobile phone scam.
Common Scams on Mobile Devices: Types and Tactics Explored
We will explore various mobile scams, shedding light on the intricacies of bluejacking, SIM swap scams, phishing scams, public Wi-Fi threats, fake apps, and more. By comprehending the nuances of these scams, users can better protect themselves in the ever-evolving landscape of digital deception.
SIM Swap Scams: Unraveling the Web of Identity Theft
As mentioned earlier in the SEC's Bitcoin ETF announcement case study, SIM swaps involve fraudulently transferring a user's mobile number to a different SIM card, giving attackers access to calls, messages, and, more critically, two-factor authentication codes. This technique is often employed in identity theft and financial fraud. Protecting against SIM swap scams necessitates heightened security measures. Users should contact their mobile providers to set up additional authentication layers, such as PINs or passwords, and monitor their accounts for suspicious activity.
Bluejacking: A Stealthy Invasion of Privacy
Bluejacking involves the unauthorized sending of unsolicited messages via Bluetooth to nearby devices. While typically harmless, it can be a precursor to more malicious activities. Users should be vigilant about enabling Bluetooth in crowded or unfamiliar places. While the impact of bluejacking is usually minimal, it serves as a reminder of the importance of maintaining Bluetooth security settings. Users should set their devices to non-discoverable mode and avoid accepting connections from unknown sources.
Phishing Scams: The Art of Deceptive Manipulation
Phishing scams involve tricking users into revealing sensitive information by posing as trustworthy entities. These can manifest through emails, messages, or fake websites that mimic legitimate ones. Recognizing phishing attempts requires scrutiny of communication sources, verifying URLs, and validating the legitimacy of requests for personal information.
Public Wi-Fi Pitfalls: A Haven for Cybercriminals
Public Wi-Fi networks pose security risks as they are susceptible to eavesdropping and man-in-the-middle attacks. Cybercriminals exploit these vulnerabilities to intercept sensitive information transmitted over these networks. Protecting against public Wi-Fi threats involves avoiding sensitive transactions on open networks, using virtual private networks (VPNs), and ensuring devices are configured for secure connectivity.
Fake Apps: The Trojan Horses of Digital Deception
Fake apps mimic legitimate ones to deceive users into downloading malware or divulging personal information. Vigilance in app source verification and scrutinizing permissions is critical to identifying these malicious applications.
App Store Vigilance
Users should exclusively download apps from official app stores, review permissions before installation, and stay informed about the latest app-related scams and malware threats.
Vishing: Voice Calls as a Vector
Vishing, or voice phishing, involves fraudulent calls to extract sensitive information. Scammers may pose as legitimate entities or authorities, leveraging voice communication's immediacy and personal nature. Users should exercise caution when receiving unexpected calls, especially those requesting personal or financial information. Verifying the caller's legitimacy through official channels is essential in thwarting vishing attempts.
Smishing: Unveiling SMS-Based Scams
Smishing, or SMS phishing, leverages text messages to trick users into revealing sensitive information or clicking on malicious links. These messages often create a false sense of urgency or emergency. Resisting smishing requires skepticism towards unsolicited text messages, avoidance of clicking on unknown links, and cross-verifying the legitimacy of messages with the purported sender.
The Role of Education in Fighting Mobile Scams
Education is a potent tool in combating mobile scams. Users must stay informed about evolving scam tactics, regularly update their cybersecurity knowledge, and share insights with their networks. Navigating the spectrum of mobile scams demands a comprehensive understanding of the diverse threats that can compromise digital security. By familiarizing themselves with the intricacies of bluejacking, SIM swap scams, phishing scams, public Wi-Fi threats, fake apps, and various other tactics, users can fortify their defenses and traverse the digital landscape with heightened resilience.
How Mobile Device Scams Spread
Mobile device scams spread through various avenues, including:
- Fraudulent Text Messages: Receiving deceptive SMS with malicious links or requests for personal information.
- Fake Calls: Scammers posing as representatives of companies or institutions to obtain sensitive data or induce financial transactions.
- Fraudulent Apps: Seemingly legitimate apps designed to collect personal information without the user's consent.
- Email Phishing: Receiving deceptive emails to trick the user into clicking on harmful links or providing confidential information.
The Need for a Preventive Approach
Given the complexity and ingenuity of mobile device scams, adopting a proactive approach is essential for protection. User awareness, education on security practices, and reliable security solutions can help mitigate risks and maintain a secure digital environment.
Deciphering Red Flags: A Guide to Identifying Mobile Scams
Deciphering the red flags that signal potential scams is crucial for users to safeguard themselves in the digital world. Recognizing these subtle indicators requires a keen understanding of the nuanced tactics employed by scammers. This chapter meticulously explores the multifaceted strategies for identifying red flags in mobile scams, providing an in-depth guide to empower users in navigating the complex landscape of digital threats.
Red Flags Unveiled: How to Discern a Mobile Scam
Social Engineering Manipulations: Like in crypto romance scams, they leverage social engineering to exploit psychological triggers, manipulating users into compromising their personal information. Be wary of communications that play on emotions or create a false sense of familiarity.
Unsolicited Outreach: Genuine entities rarely initiate contact without prior interaction. Be cautious of unsolicited calls, messages, or emails, especially if they involve abrupt personal or financial information requests.
Coercive Tactics: Scammers thrive on creating urgency to coerce users into hasty decisions. Question messages or calls that insist on immediate action to avoid purported consequences.
Requests for Personal Data: Legitimate entities do not seek sensitive information through unsolicited channels. Exercise skepticism when asked for passwords or Social Security numbers unless the request's legitimacy can be verified.
Impersonal Greetings: Scam communications often lack personalization and address recipients with generic greetings. Legitimate organizations typically tailor their interactions using the recipient's name.
In identifying mobile scams, recognizing red flags emerges as a critical skill. Users can fortify their defenses by understanding the intricate tactics, deciphering subtle indicators, and implementing robust security measures. At PlasBit, we believe that through vigilance and informed decision-making, users empower themselves to traverse the digital landscape securely, minimizing the risk of falling victim to deceptive mobile schemes.

Identifying Other Common Crypto Scams
Pump and Dump Schemes: In the crypto market, pump-and-dump schemes involve artificially inflating the price of a cryptocurrency to lure investors before swiftly selling off, leaving victims with significant losses.
Ponzi Schemes and Fake Investments: Cryptocurrency scams often manifest as Ponzi schemes or fake investment opportunities, promising high returns with little or no risk. Users should be skeptical of such schemes that sound too good.
Phishing Scams: Phishing extends to the crypto world, with scammers attempting to trick users into revealing private keys or credentials through fake websites, emails, or messages.
Fake Giveaways: Many scammers seek to attract attention by promising fake cryptocurrency giveaways. These seemingly generous offers can serve as vehicles for stealing personal data or requesting payments in exchange for participation. Users should exercise caution with such initiatives and carefully verify the offer's authenticity before participating.
Fraudulent Exchanges: Some scammers create fictitious cryptocurrency exchange platforms to steal funds from users. These exchanges may appear legitimate but are designed to collect personal and financial information. Investors should conduct thorough research before using new exchanges and prefer those with a well-established reputation.
Fraudulent ICOs (Initial Coin Offering): ICOs are similar to IPOs (Initial Public Offerings) in the traditional world but in the cryptocurrency sector. Some scammers promote fraudulent ICOs, asking investors to contribute funds in exchange for new cryptocurrencies that will never be distributed. Investors should exercise caution and carefully verify the legitimacy of any ICO before participating.
Pig Butchering: The pig butchering scam involves manipulating users' wallets through sophisticated hacking techniques. Hackers may take control of the wallet, break it down into small amounts ("butchering"), and move funds through multiple transactions to make tracking difficult. Users should secure their wallets with robust security measures and closely monitor suspicious activities.
In conclusion, the diversity of cryptocurrency-related scams underscores the importance of awareness and caution in the digital financial world. Users must continuously educate themselves about emerging threats and adopt robust security practices to safeguard their investments.
Reporting Crypto Scams: Navigating Regulatory Channels
As the popularity of cryptocurrencies rises, so does the prevalence of crypto scams. Recognizing the importance of robust reporting mechanisms is crucial in the fight against fraudulent activities within the crypto space. Reporting crypto scams safeguards individual users and contributes to combating fraudulent activities within the cryptocurrency ecosystem. Timely and accurate reporting helps regulatory bodies take swift action against perpetrators.
Reporting to the Federal Trade Commission (FTC)
The FTC is pivotal in protecting consumers from deceptive and unfair business practices. Users encountering crypto scams should file a complaint with the FTC through their official website or hotline. When reporting to the FTC, users should provide detailed information about the scam, including the nature of the fraud, the entities involved, and any financial losses incurred.
Reporting to the Securities and Exchange Commission (SEC)
The SEC oversees the securities industry, including certain aspects of the cryptocurrency market. Users encountering scams related to securities or fraudulent ICOs should report them to the SEC. The SEC provides an online complaint form for reporting securities violations. Users should provide accurate and comprehensive details about the scam they encountered.
Reporting to the Commodity Futures Trading Commission (CFTC)
The CFTC regulates commodities, including certain aspects of the cryptocurrency market. Users encountering fraudulent activities related to commodities or derivatives should report them to the CFTC. The CFTC offers an online form for reporting suspicious activities or scams related to commodities. Users should utilize this platform to provide essential information for investigation.
Reporting to the Internet Crime Complaint Center (IC3)
The IC3 is a collaborative effort between the FBI and the National White Collar Crime Center, which specializes in investigating cybercrime. Users encountering online fraud, including crypto scams, can file a complaint with IC3. When reporting to IC3, users should file a detailed complaint outlining the nature of the crypto scam, the entities involved, and any supporting evidence. It aids in a thorough investigation.
Other Reporting Avenues
Apart from the mentioned regulatory bodies, users can also consider reporting common scams on mobile devices to local law enforcement, state financial regulators, and relevant consumer protection agencies.
Effectively reporting crypto scams is essential in curbing fraudulent activities within the cryptocurrency space. Users should proactively report to regulatory bodies such as the FTC, SEC, CFTC, and IC3, providing comprehensive details to aid investigations. By actively participating in the reporting process, users contribute to the collective effort to create a safer and more secure environment within the dynamic world of cryptocurrencies.
Fortifying Your Digital Armor: Strategies to Protect Against Scams
In the vast landscape of digital connectivity, where opportunities abound, so do the risks of falling victim to scams. This concluding chapter empowers users with comprehensive strategies to fortify their digital defenses and protect themselves against many scams. Individuals can navigate the digital realm with confidence and resilience by incorporating proactive measures and cultivating a vigilant mindset.
Cultivating Digital Literacy
Stay Informed: Be updated about the latest scams, emerging tactics, and shared threat vectors. Regularly consult reputable sources for updates on cybersecurity and digital threats.
Verify Information: Before taking action online, verify the authenticity of information, websites, or contacts. Use official channels to confirm the legitimacy of requests, especially those involving sensitive information or financial transactions.
Strengthening Password Practices
Use Strong, Unique Passwords: Craft solid passwords for each online account, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information, such as birthdays or common words.
Implement Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security. This additional step ensures that access remains protected even if passwords are compromised.
Safeguarding Personal Information
Limit Public Sharing: Exercise caution when sharing personal information on social media or other platforms. Limit the amount of personal data exposed to reduce the risk of targeted attacks.
Be Skeptical of Requests: Question unsolicited requests for personal or financial information, whether through emails, messages, or phone calls. Legitimate entities rarely request sensitive data without proper context.
Secure Internet Practices
Use Secure Websites: Transact only on secure websites with "https://" in the URL. Avoid entering personal or financial information on non-secure sites.
Be Cautious on Public Wi-Fi: Exercise caution when using public Wi-Fi networks. Avoid accessing sensitive information or conducting financial transactions on open networks, and consider using a virtual private network (VPN) for added security.
Regular Software Updates
Regularly update operating systems, applications, and antivirus software to ensure the latest security patches are applied. Outdated software may contain vulnerabilities exploited by scammers.
Verify App Sources
Only download apps from official and reputable app stores. Check user reviews, verify permissions, and research the developer's credentials before installing any application.
Monitor Financial Statements
Frequently monitor bank and credit card statements for any unauthorized transactions. Report suspicious activity to financial institutions promptly.
Reporting Suspected Scams
If you encounter a suspected scam, PlasBit recommends reporting it to relevant authorities, such as the Federal Trade Commission (FTC), Securities and Exchange Commission (SEC), Commodity Futures Trading Commission (CFTC), or the Internet Crime Complaint Center (IC3). Promote awareness by sharing information about scams with friends, family, and colleagues. A collective effort to educate others enhances the overall cybersecurity resilience of the community. In the digital age, protecting oneself from scams requires a proactive and informed approach. By cultivating digital literacy, adopting secure practices, and staying vigilant, individuals can confidently navigate the digital landscape and reduce the risk of falling victim to scams. Remember, your digital security is in your hands, and the more fortified your defenses, the safer your online experiences will be.







