Crypto mixers, or tumblers, are services that maintain a user's privacy during digital transactions. These services work by pooling multiple users' coins together and then redistributing them, making it hard to trace the source and final destination of the funds. Jimmy Zhong leveraged these mixers by creating a series of intricate transactions to obscure his Silk Road withdrawals. Jimmy Zhong Crypto Mixers to launder the stolen 51,680 Silk Road bitcoins, blurring the origin of the bitcoins via a complex mixing process, making it very hard for investigators to trace the stolen bitcoins and connect them back to his real identity. That is how Zhong covered his digital tracks for many years.In the cryptocurrency world lies the story of Jimmy Zhong and his notorious theft from the Silk Road market, a scene-setter for the possibility of sinister uses in this system. The most famed of the darknet markets, Silk Road, epitomized the darker side of cryptocurrency's promise of privacy, enabling its users to make illegal transactions with its anonymous nature. Within this criminal digital bazaar, Zhong exploited a critical vulnerability in the system to orchestrate one of the most notable heists in crypto history and absconded with 51,680 bitcoins.
At the core of Zhong's operation were the means of laundering cryptocurrency through "crypto mixing." Also known as tumblers, such mixers are devised explicitly for cryptocurrency transactions. However, they are measures taken to protect privacy and, sadly, serve as a double-edged sword: they can potentially cloak a user's nefarious activities. Mixers break the direct link between deposit and withdrawal addresses, bringing a complex web of transactions that make tracking illicit funds much more difficult. The Silk Road saga and Jimmy Zhong Crypto Mixers' misuse drive this point that one can be an instrument for harmful elements in unregulated digital environments. As a regulated cryptocurrency marketplace, our platform, PlasBit, has a staunch duty to transparency and security, which is the opposite of the chaotic marketplaces common to the beginnings of cryptocurrency. PlasBit is a very safe platform under legal supervision to ensure that all users' funds are completely protected against any Silk Road incident.
Trying to Mask His Digital Trails
Crypto mixers, or tumblers, are services that increase the anonymity of cryptocurrency transactions. These services work by intermingling the digital assets of different participants, thus making it impossible to track where any specific funds came from or where they are going.
Pooling Funds
Users forward their bitcoins to a shared pool at the mixer's command, and the pool joins those bitcoins with others.
Aggregating Mechanism
In the pool, a mixer blends the funds randomly and scrambles them in thousands of disjointed transactions: the paths of these transactions become thoroughly entangled and genuinely impossible to trace.
Distribution
The bitcoins are then distributed to fresh addresses quoted by the users, excluding any service fees that might have been caused. These fresh addresses reveal no connection with the original holders, thus concealing any user's transaction trail.Crypto mixers do not primarily aim to anonymize transactions but break the direct linkage of the cryptocurrencies to the participants, making it harder to trace exchanged funds. This, in turn, gives participants the anonymity they would want to transact illegally.
Following the Heist
After stealing 51,680 bitcoins from Silk Road, Jimmy Zhong was faced with the problem of laundering them. He muddled the development's transaction history using crypto mixers to make the funds untraceable in the crime.
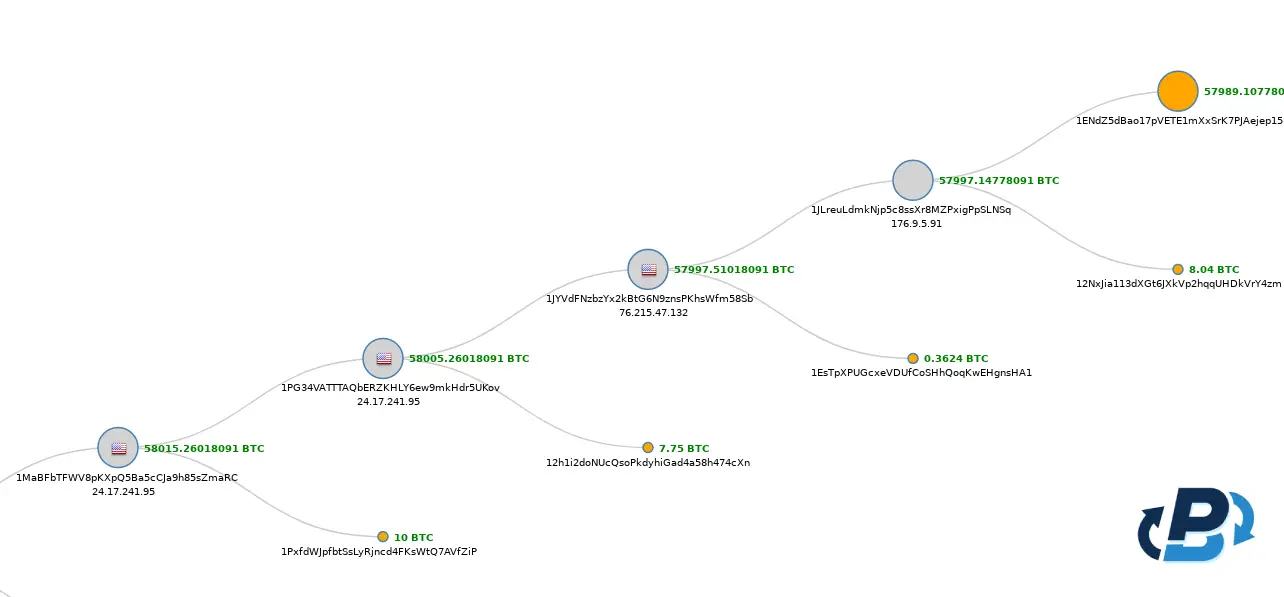
Anonymity Strategy
Zhong employed many mixers to shuffle his stolen bitcoins through many transactions while trying to dissociate the illicit funds from his wallets. By funneling significant amounts of bitcoins into those services, it would then redistribute smaller quantities to a network of addresses under his control, thus creating a tangled web of transactions and thereby hiding the flow of the fund. This worked very well initially, allowing Zhong to lead a life of luxury with the secret bitcoins underpinning it.
Ineffectiveness and Collapse of Jimmy Zhong Crypto Mixers' Strategy
Indeed, crypto mixers offer security on the surface, but their design makes them less effective than intended and somewhat defeats the purpose for which they were set up in the first place. In Zhong's case, these limitations played a pivotal role in his capture.
Volume and Visibility
The vast amounts of bitcoins that Zhong tried to hide are just too significant. Large volumes are easily detectable. Even if adequately mixed, large transactions are bound to attract attention since they absorb a significant proportion of the pool into one wallet.
Blockchain Forensics
With improvements in blockchain technology, the tracing of cryptocurrency transactions has also greatly improved. Blockchain forensics experts use complex algorithms to track transaction paths, detect mixing services, and possibly de-anonymize users. In Zhong's case, forensic experts had to use the tools to trace his mixed bitcoins down to the roots of the Silk Road.
Critical Errors
Zhong critically errored when he mixed his bitcoins with some clean transactions. In September 2019, he sold 118 Bitcoins from a wallet that contained legally obtained Bitcoins on his verified account. During this transaction, he unknowingly created a change address that received some of the mixed Bitcoins. This link provided the crucial clue investigators needed to link the stolen funds back to him.
Persistent Law Enforcement
The IRS and others are upping the ante on their cryptocurrency crime investigations. The keys to unraveling Zhong's schemes were caring about the details, accessing records from cryptocurrency exchanges, and analyzing blockchain data. However, in the long run, Jimmy Zhong crypto mixers did not serve as a shield against the law. The infusion of substantial transaction volumes, sophisticated blockchain analyses, and critical operational mistakes in order finally got him arrested and convicted.
The Early Days of Jimmy Zhong
Jimmy Zhong's adventure deep into technology and cryptos is a story of great talent and early fascination with the exploding digital world. He grew up in the 1990s in Cobb County, Georgia, feeling often isolated and misunderstood by his peers. This kind of social alienation pushed him to the comfort of the digital life; in this world, he thought he belonged more than in the schoolyard or family gatherings. From a very young age, young Jimmy had a fantastic insight into technology. By the time he reached middle school, he had already learned several programming languages. His bedroom, with its aging computer, became his haven where he would escape the challenges that faced him in his everyday life and create virtual landscapes. Jimmy's moment came in 2010 when he discovered Bitcoin. Introduced to the concept via online forums and tech communities, he was taken aback by cryptocurrencies' promise and revolutionary potential. Bitcoin was right on the frontier of technological innovation and potential financial independence, undeveloped and mostly unknown by the masses.
Jimmy began mining Bitcoin on his computer early in the cryptocurrency's life, distributing the network in a way accessible to most people with modest computational resources. Initially, the activity was a hobby, but it sowed the seeds of his severe further involvement in the crypto community. Engagement with Bitcoin at the early stage was simply curiosity and the feeling of being involved with something new and uncharted.With Bitcoin's value still negligible, Jimmy was more interested in the technology and the community of like-minded enthusiasts than the prospect of using it as a vehicle for investment. But this was all to change with the growth of bitcoin value, which would give direction and purpose to Jimmy's life, culminating in his now legendary exploits on the Silk Road. Long gone were the days of youthful exploration; the complex ethical and legal dilemmas he would soon be presented with could not have been more different.
About the Silk Road
The Silk Road was an online black market and essentially the host for the sale of illicit drugs. It was initiated by Ross Ulbricht, under the pseudonym Dread Pirate Roberts, in February 2011. The Silk Road operated as a Tor-hidden service, so access could only be gained via the Tor network. Users were assured security from governmental surveillance and scrutiny. Silk Road used the Tor network to hide the location of its servers, whereas all transactions on the system were made in Bitcoin to keep buyers and sellers anonymous.
Role in the Darknet Market
Silk Road was more than just a marketplace; it was a figurehead of the darknet economy. This opened the floodgates to the illicit trade of goods and services that ranged from narcotics to fake passports. With the anonymity of the dark web and the untraceable nature of Bitcoin transactions, Silk Road provided a relatively low-risk environment where users could engage in activities far removed from law enforcement and regulators. This successful model inspired many imitators, sealing the dark web's reputation as a haven for illegal activities.
Reputation of Cryptocurrencies
The excellent and wrong sides came with Bitcoin's popularity through the Silk Road. This demonstrated that cryptocurrencies could offer financial privacy and an alternative to the traditional banking system. On the contrary, it emphasized its potential to be misused, as Bitcoin became synonymous with criminal activities due to its relation to the Silk Road. Such a connection led to great skepticism and fear by the regulators and the public, shadowing the overall potential for cryptocurrencies in legitimate use.
The Heist Step-by-Step
What Jimmy Zhong perpetrated against the Silk Road is a notable crime in cybercrime history. It also shows how flimsy new platforms can be and how clever their users can be. The technical heist was pulled off via a combination of technical know-how and a deeply ingrained understanding of the vulnerabilities that accompany the typical cryptocurrency transaction.
Exploiting the Vulnerability
The fundamental at the core that Zhong had exploited was the transaction processing system of the Silk Road. The problem was a race condition; this is where a system is trying to do a couple of things simultaneously, but because of the nature of the device or system, the things need to be done in the correct sequence to be right. In Silk Road's case, when a user initiated a Bitcoin withdrawal, it created a window of opportunity allowing multiple executions of the same transaction before the first one was confirmed on the blockchain. This was due to the user interface's weak synchronization with the underlying database at the back end.
Technical Execution of the Heist
Jimmy Zhong's approach to exploiting this vulnerability was methodical and technically sophisticated:
Multiple Withdrawal Requests
Zhong learned that if he made multiple withdrawal requests very quickly, he would trick the system into processing more withdrawal requests than the amount he held in his balance.
Automated Scripting
Zhong most likely used automated scripts running to their best ability with this exploit. It permitted him to launch quick, repeated withdrawal commands at a speed that would have been impossible for a human to conduct manually. This way, he could exploit a race condition flaw before the balance was updated after each withdrawal by the system.
Watching the Blockchain
Zhong needed to meticulously monitor the blockchain to ensure the network didn't invalidate multiple transactions before any were confirmed. This close observation required a deep understanding of how these transactions were validated and added to the blockchain.
Withdrawal to Several Wallets
Zhong would have withdrawn the stolen bitcoins to several wallets to make it even harder to track his actions and better shield his ill-gotten profits. This move made tracing the stolen funds tricky and facilitated the money laundering of the bitcoins through the many available channels.
The Aftermath
The successful execution of the heist netted Zhong a total of 51,680 bitcoins, a staggering amount that showcased both the severity of the exploit and the vulnerabilities present in early cryptocurrency platforms like Silk Road. The sophistication in the methods used not only highlights the technical ability of Zhong but is also a stark reminder that calls for robust security measures in digital transactions and platforms are a necessity. This heist is a vital lesson for the cryptocurrency community on using secure, well-audited systems to avoid such incidents. It also reflects the broader implications for security in the fintech sector, where innovation often outpaces the establishment of comprehensive security protocols. security protocols in most cases.
Life After the Heist
At 22, Jimmy Zhong was thrown headfirst into orchestrating the biggest heist in cryptocurrency. For the first time in his life, he allowed himself to be involved in a lifestyle that, until then, he had only dreamt of. He used to live the life of the landed gentry, owning properties in the millions of dollars and a fleet of expensive cars. His lifestyle was also full of flashy social events and parties organized to impress and seek the favor of friends. Still, Zhong's inner life was complex and challenged under such an outward facade of luxury. His spending was motivated by an intense desire to prove his worth, a narrative of the same consistency as that of his childhood, full of social exile and bad memories. The first euphoria of the life of luxury soon vanished, leaving in its wake loneliness and paranoia about being discovered in hiding and the moral weight of his actions. This also led to a deterioration in his social relationships, whereby friendships and romantic interactions became overshadowed by the dynamics of his wealth, with the result often being mistrust and skepticism about the genuineness of those around him.
The Downfall
Several critical mistakes that brought Jimmy Zhong down and red-flagged him to law enforcement included his flamboyant lifestyle, with many buy-ins and an evident profile. His behavior was highly conspicuous and served as a warning sign. A crucial operational security mistake was consistently using the same IP address as his identity for cryptocurrency transactions. He would also share his wealth online in the most reckless way, trying to be an influencer and drawing unnecessary attention to himself, which made him a person of interest to various federal agencies. Law enforcement agencies have used advanced blockchain analysis to trace Zhong's obfuscated Bitcoin transactions to the Silk Road. Jimmy Zhong crypto mixers might have mystified the source of all the stolen bitcoins, but the sums of money were enormous. The mixing technologies are impossible to anonymize totally; they are explicit in their nature and design, hence attracting the eyes of law enforcement. Ultimately, Zhong's technical slipups and the basic capabilities of law enforcement led to his arrest and the unraveling of his secret life, funded by the Silk Road heist.
Jimmy Zhong From Silk Road Heist to Legal Troubles
Arrest and Legal Proceedings
The revelations in court were about how Zhong had meticulously covered his tracks and how the Bitcoins had been stolen. The tale of Jimmy Zhong and his career on the Silk Road would finally culminate in his arrest and the subsequent court case. He was charged with offenses such as wire fraud and money laundering, allowing the trial to delve into the intricacies of his sophisticated heist and his extravagant lifestyle funded by ill-gotten gains. It would be explained to the courtroom how Zhong meticulously covered up how he stole the Bitcoins. He was so remorseful; even after the overwhelming evidence showed his guilt, Zhong said he had brought bad things to himself and others because of his actions. He was sentenced to a very lenient one-year-and-one-day prison term in 2022 due to his cooperation and remorse.
Post-Trial Adjudication and Monitoring
After serving his sentence, Jimmy Zhong, who exploited a vulnerability in the Silk Road marketplace to steal over 51,680 Bitcoins, completed his prison term in April 2024. Following his release, he is now under a period of supervised release, during which probation officers will monitor him to prevent any potential re-offending. Life indeed can be very harsh on a convict, not only inside a prison cell but also outside in the real world, with a badly damaged reputation, poor career prospects, and very few social ties. A convict would further have his life significantly complicated due to a criminal record if he ever decides to travel or work, as he will always be under the vigilant eyes of the public and police officers.
Financial Considerations and Current Lifestyle
The court ordered his fortune in Bitcoins to be taken up, plus the other assets he had accumulated from his criminal earnings, including his luxury cars, private jets, and investment in real estate. While the seized assets are taken to satisfy legal and financial penalties, the tax obligations on previously liquidated Bitcoins still stand, potentially leaving Zhong with a tax bill to manage even after losing the bulk of his fortune. That, on top of everything else, proves difficult due to cryptocurrency values' highly volatile nature. He is now a Lyft and Uber driver, an about-turn from his luxurious life. This drastic change highlights the extent of his downfall, leaving him feeling alienated and full of regret, as his high-society friends have shunned him.
PlasBit Offering Trust and Security in the Cryptocurrency World
Our Economic Freedom and Security
Launched in 2020, PlasBit provides sophisticated financial services with the prime objective of harnessing blockchain technology's transformative power. At PlasBit, we believe in making a borderless financial system quite detached from governmental delimitations, leveraging people's economic freedom and fundamental rights to control their financial destinies.
Innovating with Unmatched Security
In digital currencies, where digital theft looms large, as in Jimmy Zhong's Silk Road heist, security is not just an option but the cornerstone of trust and reliability. At PlasBit, we learn from vulnerabilities exposed in such incidents to fortify our platform against similar threats.
Salient Security Features of PlasBit:
Two-Factor Authentication
Our platform enhances security through robust two-factor authentication, including SMS, email verification, and support of authenticator apps, making unauthorized access almost impossible.
24/7 Customer Support
We ensure that you are constantly catered to, so with our round-the-clock customer support via live chat or email, all your inquiries or issues will be met quickly.
Withdrawal Confirmations and Login Alerts
Verification for withdrawals is confirmed through susceptible procedures, and login alerts have been made available for sending, giving users total control and coverage over their accounts.
Cold Storage Safeguards
Regarding incidents like Zhong's, for instance, in which large sums were at odds, we keep 100% of our users' cryptocurrencies in cold storage. This way, our client's assets are not at risk from an online threat and are accessed only under the most secure conditions
.
Conclusion Jimmy Zhong Crypto Mixers and Robust Security with PlasBit
Jimmy Zhong, who had 51,680 bitcoins siphoned from Silk Road, vividly illustrates cryptocurrency mixers' critical role in the digital finance landscape. This suggests that he happened to be a good user of the mixing service to launder stolen funds. On the one hand, it proves the quality of such services in providing transaction anonymity, while on the other hand, it points out their possible misuse to mask proceeds from crime. Crypto mixers, or tumblers, are designed to enhance privacy by pooling and mixing the coins of various users. This way, the trail of funds gets obfuscated, giving them a veil that complicates tracing transactions back to their sources; hence comes the anonymity valued. But on the same note, this can be a kind of protection for such nefarious actions, as with one Zhong, who could leverage such systems to keep his actions under wraps for several years. This is a sad truth based on the core risks involved in the underregulated use of cryptocurrency mixers.
They can serve an essential purpose for anyone willing to remain private, yet that uncanny use probably involves money laundering. In this duality, crypto platforms must implement superlative security and compliance protocols.PlasBit represents an effort leading in the complex challenges of the cryptocurrency exchange landscape. PlasBit aims to rid crypto mixers of the negative connotations they face by observing high-security parameters that guarantee the integrity of each transaction on its platform. Our approach is twofold: enhancing user privacy while rigorously guarding against illegal activities. At PlasBit, our commitment to regulatory compliance ensures that our users have a secure environment to guard their assets from external threats and internal vulnerabilities. We store 100% of our users' funds in cold storage, ensuring that assets are unreachable from online risks and accessible under the strictest security conditions.
But in the end, while this digital currency landscape is being opened up as never before, allowing for absolutely free usage, it will also dictate a higher level of security and watchfulness than ever before. Based on a solid security framework and compliance with regulations, PlasBit does everything possible to ensure that our platform remains a safe harbor in the turbulent seas of cryptocurrency. It is only then that PlasBit empowers users, putting first the confidence in interaction with digital assets, knowing they are safe and secure, featuring from the many perils emphasized by the cautionary tale of Jimmy Zhong crypto mixers misuse. As time progresses, PlasBit remains set at the pace for security and trust in the cryptocurrency industry, where our users can realize their maximum potential in their digital assets in a secure and regulated environment.







