Having too much money can become a heavy burden, because you eventually run out of places to hide it in. The simplest way to relieve that burden used to be having vaults and treasure chests to hide your money from prying eyes. Today, we store value in cryptocurrencies, yet we can somehow still bury them in the depths of a hardware wallet, which is just a fancy treasure chest. If you’re aching for your own crypto treasure chest to hide Monero in, here is how to set up Monero on Ledger. You need to open the Ledger Live app on your PC, search through the app catalog for “XMR” and install the Monero wallet app, download and install the Monero GUI wallet to your PC, open the program and press “Create new wallet from hardware,” choose your hardware wallet model, create a password, then you will need to continue the process on your Ledger, press “Export view key” which will export the seed phrase to your PC, then check the Ledger for the Monero icon to confirm it is all set up.
Note that your seed phrase is actually being saved in the Ledger. While creating a Monero GUI wallet from a hardware wallet, you will be able to view the seed as a list of words because it’s encrypted and saved in the Ledger as your key. You also can't transfer XMR from your GUI wallet on the desktop without the Ledger being connected to your PC, and you will need to sign the transactions physically using your Ledger, which serves as an extra layer of security. Here is a breakdown of how to set up Monero on Ledger with pictures, followed by a detailed analysis of the kind of attacks and schemes you should guard your Ledger against.
A Visual Guide on How to Set up Monero on Ledger
1. Open the Ledger Live app on your PC and search through the app catalog for “XMR” to find the Monero wallet, and press “Install”. Make sure the Ledger is connected to your PC for the entire process.
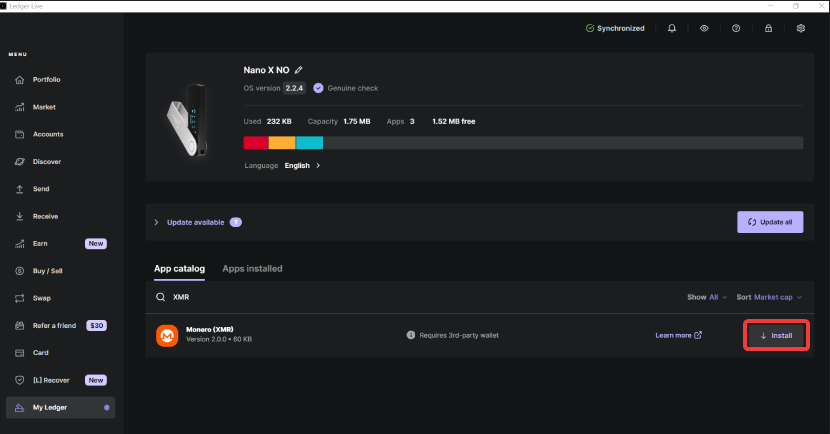
2. Wait until the wallet is installed.
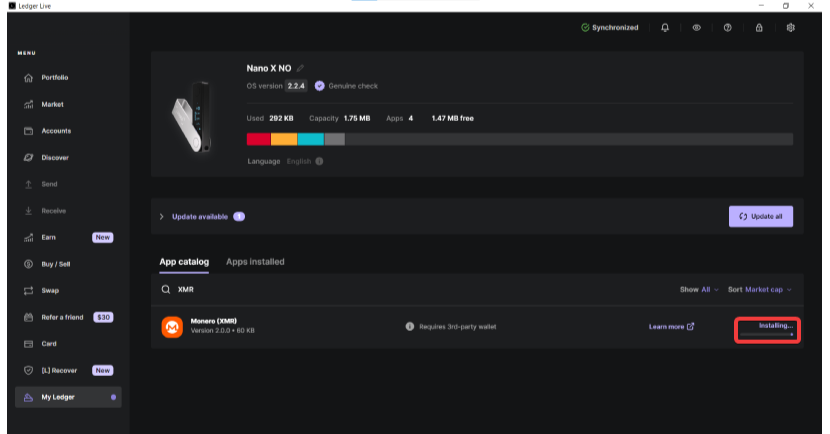
3. Download the Monero GUI wallet. Once installed, open the program and choose the “Create a new wallet from hardware” option. Keep your Ledger connected.
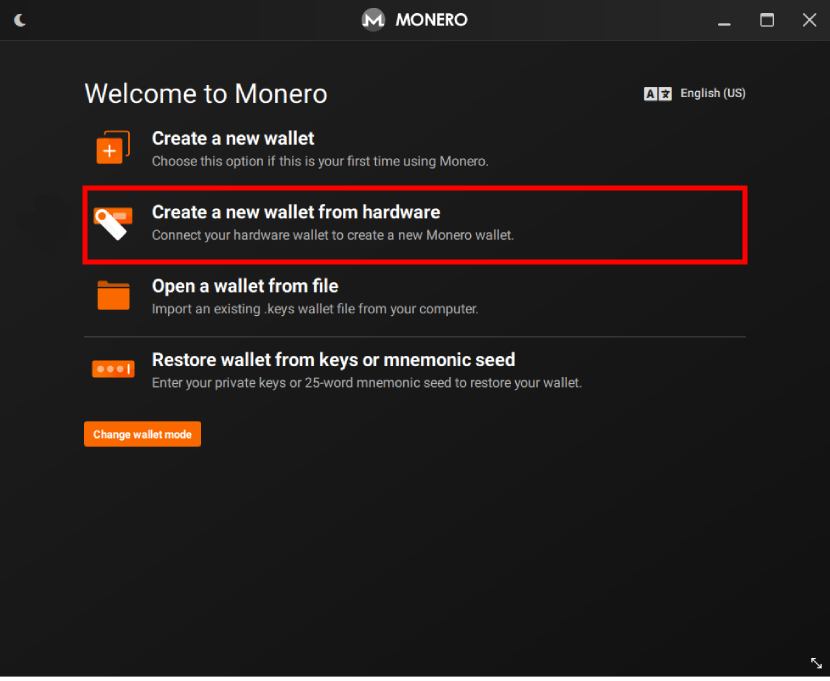
4. Choose your hardware wallet model.
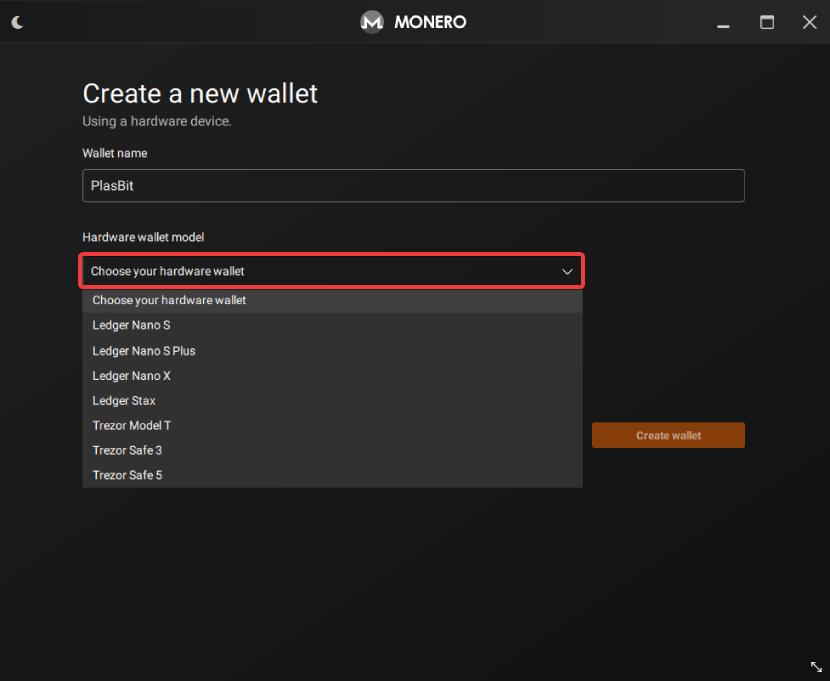
5. Make sure “Create a new wallet from device” is selected, then press “Create wallet.”
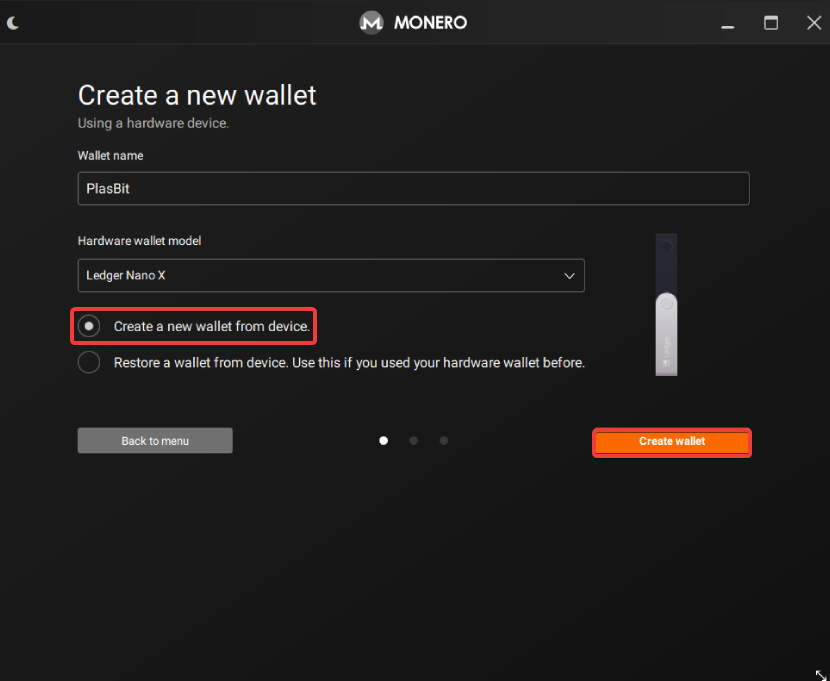
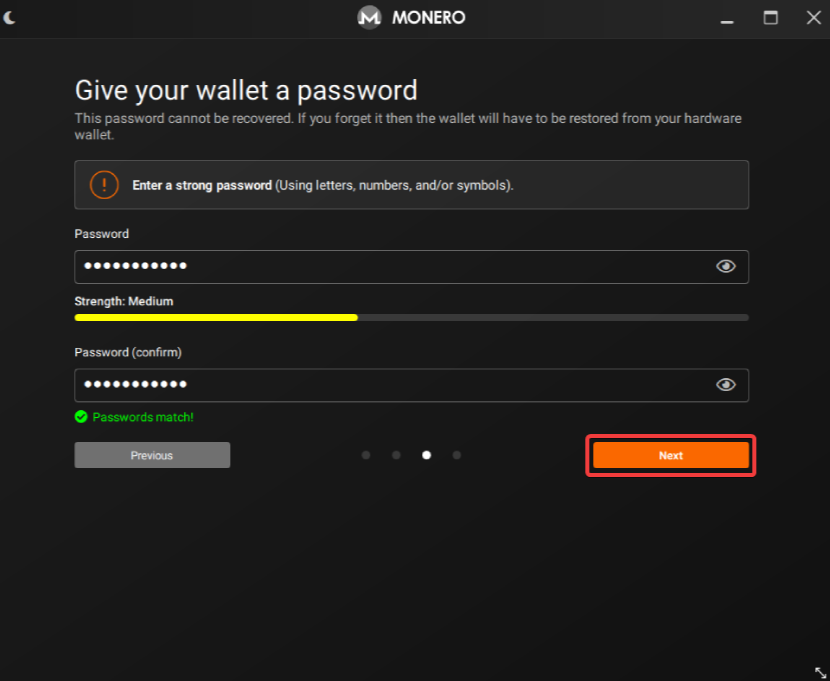
6. Create a password for the wallet, then press “Next.”
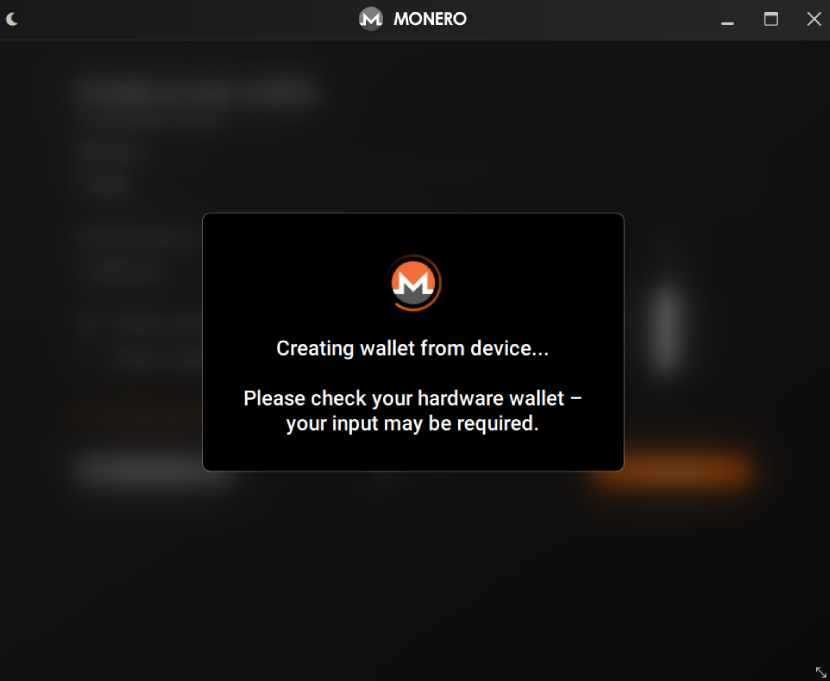
7. A message will appear, asking you to continue the process on your hardware wallet.
8. Press “Export view key” on the Ledger.

9. Press the button again to export the seed phrase to your device.

10. Check the Ledger for the Monero icon to confirm it is all set up.

That's it, your Monero wallet on Ledger is all set up!
Safety Precautions with Ledger
I previously wrote on Monero and the safeguards it introduces for user privacy. In short, Monero is by far the most private crypto in the world. It is designed from the ground up to discourage and thwart any transaction and user analysis that could reveal Monero owners and their wallets. Monero still has its weaknesses, but they are largely due to weaknesses arising from the Internet infrastructure and user inertia in overcoming them. We all want fast, simple solutions that take no thinking and make us feel comfortable. That’s a problem, because the most obvious solution to solving Monero’s weaknesses is to go offline, meaning to buy a Ledger and park your Monero on it. Using Ledger with Monero can make you feel like you’re invincible, but it actually increases the attack surface of your Monero wallet(s) and makes you more exposed to all kinds of scams and schemes.
Why use Ledger then? While a Ledger does expose you to more attacks, it lessens the impact of each individual attack or scam. If your computer gets infected with crypto-stealing malware, Ledger will ensure that at least some of your crypto stays safe, when without Ledger you’d probably lose all your crypto. The problem is that there are no clear-cut safety precautions on how to protect your Ledger from multiple attack vectors. Should you keep it in a safe, bury it in your backyard, or wear it on a lanyard around your neck? Well, it’s not so simple. Now that you know how to set up Monero on Ledger, it’s time to creatively defend it from cyber attackers. I have devised a couple of safety precautions on the most common attack vectors online, which I think can be applied to Ledger with crypto on it, but first let's try to understand how attackers think. Crypto is nothing more than information, so how should you guard your information against cyber attackers?
Thinking like a pirate
Pirates used to roam the seven seas and randomly attack traveling merchant vessels. Pirates didn’t want to confront anyone head-on unless they were desperate or suicidal, which wouldn’t make them pirates for much longer. They weren’t honorable, brave, or even competent; the most fitting description is that they were “scurvy dogs.” Rather than Jack Sparrow, they were unassuming and looked more like the “I’m the captain now” meme, counting on the element of surprise more than anything else. The ones that were successful in the long run arguably had the backing of states and acted as their agents, scouts, and spies. The word “pirate” simply means “attacker,” and the same logic that they used to choose their targets applies to crypto attackers, who roam the internet in search of easy prey.
As you’re browsing for the Ledger to buy, you probably want to just get it over with, but that can put your Monero in danger if you’re not careful, because you might have already been earmarked by cyber pirates. They are constantly scanning the internet for easy targets, counting on people being too busy to dive deep into how to set up Monero on Ledger and think for themselves. Cyber pirates have a huge incentive to insert backdoors in software and hardware used to process cryptocurrencies and wait for the prey to catch itself without exposing them to danger, which can happen to you too. For example, cyber pirates can sell used Ledger wallets with their software already installed in hopes that you will use those Ledgers and willingly put your Monero in them. What they are unlikely to do is find your home address and smack you in the face with a $5 wrench.
The $5 Wrench Attack
XKCD published a famous comic titled “Security” that seems to propose a simple way to crack encryption, with the implication that the same principle can be applied to stealing cryptocurrency or hacking associated devices. Instead of building a complex million-dollar computer cluster to crack an encryption algorithm, the comic proposes that thieves can kidnap a crypto HODLer, drug him, and smack him with a $5 wrench until he reveals the password of his encrypted laptop.
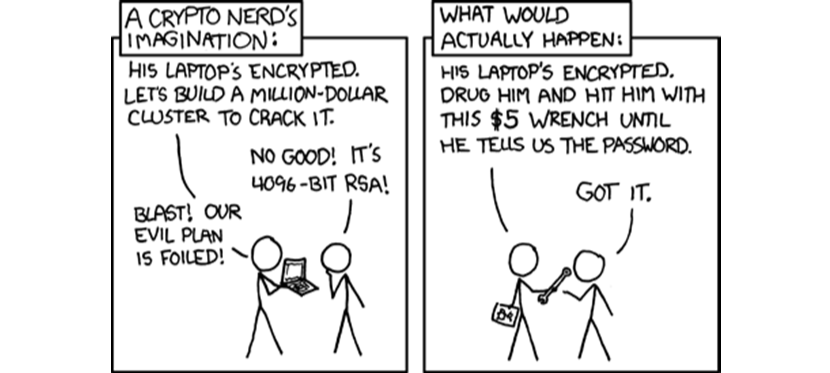
I’m not sure if the author made this comic tongue-in-cheek, because it is otherwise based on boomer-tier logic that grossly oversimplifies how cryptocurrency theft occurs. Contrary to what you’ve seen on the TV, giving someone the Jack Bauer treatment does not produce any worthwhile information. People in pain or undergoing intense torture tend to turn into an incoherent mess or simply pass out from shock rather than saying who they work for. To make the punchline in the comic even more bizarre, it also proposes giving drugs to the victim, apparently so that he feels less pain. Remember the part of the plan where they get information by causing pain with the wrench? Yeah, it makes zero sense, doesn’t it? Drugs would also lead to a real danger of accidentally overdosing the HODLer, which is a bad idea for extracting information unless the thieves are also masters of the ouija board.
Finally, the thieves in the comic would find themselves hard-pressed to escape with their loot, because taking someone hostage, forcibly drugging him, and beating him to a pulp with a wrench isn’t exactly the pinnacle of stealth. They might have a head start, but that kind of mess makes global headlines, prompting law enforcement agencies to mobilize significant resources to find the thieves. This isn’t a jaywalking grandma that earns a slap on the wrist; if need be, cops would mount a countrywide or an international manhunt and wouldn’t rest until they got the thieves.
Making HODLers spill their beans
XKCD comics, including “Security,” are made by Randall Munroe, who Wikipedia describes as an engineer. He seems smart and should be well-versed in cybersecurity, so how come he made such a gross oversimplification? Can it be that he is so clueless about how things work in the real world? While it’s possible that he’s naive or that he was just poking fun at paranoid crypto nerds, I think the more likely scenario is that “Security” is a reflection of the kind of content cyber pirates make and spread to reveal HODLers. Whether Randall realizes it or not, “Security” is in essence a sophisticated psychological test. I suspect that it became a widespread meme because cyber pirates realized that it is a test and amplified its reach across the internet to identify HODLers. How you react to “Security” reveals whether you have crypto, which ones, where you’re HODLing them, and which security measures you’re using to protect them. The comic also vastly exaggerates the effectiveness of physical violence in extracting information, making HODLers focus on guarding against physical attacks rather than data mining, trickery, or phishing.
It seems preposterous that “Security” could do all that, because it is just an unassuming stick-figure comic, but that’s exactly how cyber pirates would present themselves on the internet. If I were a cyber pirate, “Security” would be the kind of memetic content I would churn out and mass distribute to identify HODLers and make them spill their beans. It is similar to walking around a crowded train station and randomly blurting out, “My friend’s wallet got stolen here yesterday.” People hearing that would instinctively reach for their wallet, revealing where they’re holding it. In that moment of anxiety, they might start excitedly talking to whoever they’re with, revealing even more information about themselves and their wealth.
Revealing your passwords
Another popular XKCD comic is “Password Strength,” which deals with the topic of choosing a strong password. The premise is simple — instead of choosing passwords such as Tr0ub4dor&3, which are hard to remember, it’s much better to choose a longer password, such as “correct horse battery staple.” The idea is that password length dramatically increases password strength, which is true, provided that you don’t use common dictionary words, such as “correct,” “horse,” “battery,” and “staple.” This comic is another example of bafflingly wrong cybersecurity advice that is also a psychological test, this time prompting people to talk about and reveal hints about their passwords.
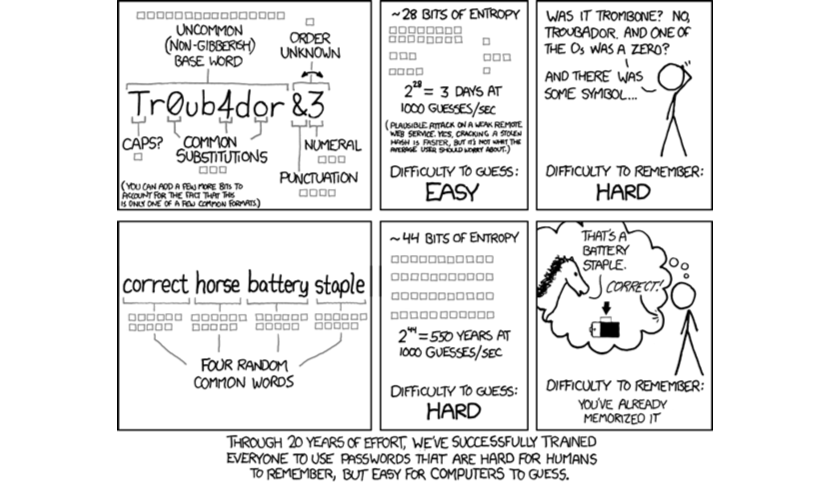
Cyber pirates relish that kind of misinformation because it gives people false confidence in using dictionary words in their passwords. It’s been long known that cyber pirates reveal passwords by using a dictionary attack, which means going through the list of most commonly known passwords. How do they create the list? They hack user accounts, servers, and devices, and also scan the internet for memes such as “Password Strength.” Anyone foolish enough to use “Tr0ub4dor&3” or “correct horse battery staple” as a password might as well have put “admin” or not have used a password at all.
The Dead Internet Theory
“Security” and “Password Strength” are just two examples of low-quality content that gained worldwide attention for no apparent reason. The two comics achieved memetic status and are by now immortal on the internet, making their rounds on all social platforms and ensuring that every new generation of internet users gets to see and react to them. There are serious articles on the “$5 wrench attack phenomenon" and even a few websites called Correct Horse Battery Staple that generate passwords for visitors, which I’m sure won’t be added to any kind of list or dictionary. So, how does that kind of content gain visibility? For a while now, people have been proposing the idea that the vast majority of users on the internet are not human.
I think that there is some merit to the Dead Internet Theory, but that it is poorly worded. In my opinion, some small fraction of internet users are not human, about half of internet content is not generated by humans, and the vast majority of online interactions are not human. That means that upvotes, likes, shares, views, and other metrics are in the vast majority of cases arbitrary and artificial, and likely boosted by an algorithm to promote a certain kind of content that generates engagement and makes people overshare sensitive information. Each platform has its own rules on how it calculates engagement metrics and prefers to exaggerate them to impress investors and give an aura of being vibrantly alive. On YouTube, there is an entire science on how the platform calculates and counts a view on a video (30+ seconds per video are a view, no more than 4–5 repeat views from one user per 24 hours, etc.).
Reddit Data Mining
No platform is as egregiously fake on the entire English-speaking internet as Reddit, with bots allowed to freely post alongside other users and even moderate entire communities. Reddit notoriously had to fake user activity in its early days through bots, which later became a norm on the platform. Reddit features suspiciously popular meme threads that pose inane questions in the vein of, “What is your favorite movie and your favorite color?” Those threads regularly have tens of thousands of upvotes but only a couple hundred comments. Answers to those questions can be used to data mine users, meaning to compile a database of information that cyber pirates can use to brute-force security questions and passwords. Those threads get tens of thousands of upvotes, which can be explained by braindead users or by bot activity. I keep harping on about how our metadata is being gathered wherever we go on the internet, but now you can see there’s a different source of danger — us accidentally spilling the beans and oversharing information with total strangers when we think it’s socially acceptable to do so.
Theft Through Fake Content
Another danger comes through fake content, especially one that is designed to evoke strong emotions and a knee-jerk reaction. You should presume that every image you see online has been manipulated in some way, even if the manipulation is as innocuous as cropping it to remove the watermark. Images can also be maliciously edited, but thanks to AI-like tools, that can now be done with video and audio and everyone can fall victim to it, even extremist organizations. The funniest example of cyber piracy I ever saw was members of an extremist group posing for a victory photo over a battle-charred landscape while holding a banner with their Bitcoin address. A cyber pirate stealthily photoshopped the group’s Bitcoin address out of the photo and added his own before releasing the edited photo into communities aligned with that group so that he gets donations intended for them.
Of course, that plan could gloriously backfire when the cyber pirate’s Bitcoin wallet gets associated with extremism and the cyber pirate tries to cash the Bitcoin out of the system. Whenever you see images where a person is holding a banner, placard, or a sheet of paper with some message, keep in mind that it’s exceptionally easy to edit the message to read whatever the poster wants it to read. Posts originating from Twitter, Reddit, and Facebook are especially susceptible to that because they tend to host low-resolution images that have artifacts that hide the telltale marks of digital manipulation. Until the entire internet adopts something like David Chaum's encryption paradigm, be wary of all content that you don't know the source of.
Protecting Yourself and Your Ledger
Now that you know what lurks on the open internet, you can prepare yourself accordingly. Here is some guidance on how to protect your information and your Ledger from cyber pirates.
Buy an Authentic, Clean Wallet
The first hurdle in our how to set up Monero on Ledger guide is getting a proper Ledger wallet. Let’s say that you order a Ledger wallet and the package looks like it’s been opened. You check the Ledger and find scratches on it, which could be from someone using tools to pick it apart or from customs officers opening it. Is the Ledger safe to use or not?
The official guidance on checking your Ledger is that:
- a Ledger can arrive in an open package, which isn’t a cause for concern
- if the Ledger has scratches or isn’t in pristine condition, that is not a problem
- if the Ledger has been initialized before, that’s a red flag
- if the Ledger asks for a PIN, it’s been initialized before and you should not use it
- if the accompanying papers are filled out, the device has been used before or has been tampered with
The Ledger wallet can still be reset to factory settings if it’s been used, which will wipe its internal memory, deleting all settings, apps, and private keys from it, but you might not be comfortable using it.
Use the Authentic Ledger Live app
The Ledger app is another vector of attack, with adversaries offering a fake Ledger Live app that serves as a backdoor to the hardware wallet. The only authentic source of the Ledger Live app is the official Ledger.com website. Fake Ledger Live apps will ask you for the 24-word recovery phrase, which the real app will never do. When it’s about to finish setting up, the Ledger Live app will prompt you to check if your Ledger wallet is authentic. Accept the check, and if the device is authentic, you will get a notification in the app. Every time you connect the Ledger wallet to the app, the authenticity check will run again, but you can also run it manually. However, the authenticity check cannot check that the software on your Ledger is authentic. The fake app is most often offered through phishing attempts, such as through email spam, so it’s wise to exercise caution and never click suspicious links. Also, the phishing might come through ads shown in search engine results and on social media, which is why you should use an adblock-friendly browser and an adblock (sorry, Chrome users).
Use a Mnemonic Technique for Your 24-Word Seed Phrase
Initializing the Ledger will provide you with a 24-word seed phrase. It is a one-time process that puts your Ledger into word form — by using the seed phrase, you or anyone else who knows it can restore your Ledger wallet and spend the funds in it. So, it’s important that you are properly paranoid about safeguarding your seed phrase, which means never putting it in digital form, such as in a text file or photographing it. To more easily remember the seed phrase, you can use a technique similar to the one shown in “Password Strength” — create an entire story around the seed phrase and make it meaningful to you. For example, you can imagine that you’re walking through a house and seeing objects and people in a way that refers to the seed phrase words. The important part is that you are emotionally invested in the story; it should be something that matters to you, which will help you remember it for the rest of your life.
Create Segmented Personas
Whenever you’re using a service or a website, you should have dedicated hardware or software for it, and for it alone. The device you use for cryptocurrencies should only be used for cryptocurrencies, and nothing else. That applies to all other websites and services you want to use regularly. So, if you want to use Reddit, go right ahead, but try to use a separate phone or computer for it. If you can’t, at least use a specific browser, preferably in private mode, to minimize the impact of tracking cookies. For each persona, create a different backstory. Pay attention to unusually popular low-quality content that breaks social norms or tries to provoke a reaction from users. Feel free to give false answers in comment sections of such content, in data mining threads, or when you identify something as a psychological test. That makes cyber pirates waste time and effort.
PlasBit’s Unique Guide to Cyber Safety
There might be many guides on how to set up Monero on Ledger, but this one is uniquely ours. PlasBit is at the cutting edge of cybersecurity, treading where nobody dares to go and addressing inconvenient truths years ahead of the curve. Setting up your Ledger to hold XMR is straightforward, but how you guard your Ledger and your crypto is up to you. You shouldn’t blindly listen to anyone, not even PlasBit. Make up your own mind and create a security system that doesn’t attract attention and doesn’t cause you undue stress. We at PlasBit wholeheartedly endorse cypherpunk ideals, such as privacy and autonomy in financial dealings and we encourage you to do the same. PlasBit is built from the ground up to represent a new paradigm in finance and cybersecurity, with forward thinking and creative, holistic proposals and solutions. If you like the way that sounds, stay tuned for more of my awesome PlasBit content.







