The news of Roger Ver’s arrest and extradition to the US for unpaid taxes on his Bitcoin dropped like a bombshell in May 2024. The IRS used a method it dubbed “clustering analysis” to figure out the movement of the cryptocurrency influencer’s Bitcoin across wallets and conclude that he failed to pay $48mm in taxes on it before renouncing his US citizenship in 2014. That naturally aroused curiosity from cryptocurrency holders, especially those who have a significant stake in Monero, who are wondering if the IRS has a similar method for Monero. So, can the IRS track Monero? No, they can’t, but they have contracted two companies, Integra FEC and Chainalysis, promising each $625,000 to figure out a way to crack Monero’s privacy protections. So far, there is no indication that they’ve had any success, and their official blogs show no sign that they’ve come close.
There is no announcement from the IRS on whether Monero has been cracked either, which is telling, but there is enough circumstantial evidence that the US government and the private sector combined don’t have the manpower to do it. One piece of evidence is that the IRS issued several rounds of menacing letters to alleged or confirmed cryptocurrency holders, urging them to report themselves or suffer dearly, which is in essence pleading and begging people for free labor. When even that wasn’t enough, the US government resorted to bullying exchanges into delisting Monero. But, there is one exchange that stands undaunted and will keep offering ways to exchange Monero to BTC.
Monero Under Scrutiny
In a May 13, 2019, conference about preventing the misuse of cryptocurrencies in cybercrime, the Under Secretary for Terrorism and Financial Intelligence, Sigal Mandelker, singled out Monero. She called it an innovative product that is anonymity-enhanced and noted that industry compliance with regulations is crucial in preventing ransomware attacks, such as the WannaCry 2.0 global attacks that took $140,000 in Bitcoin ransoms that were converted to Monero. That marked the beginning of the Can the IRS Track Monero game of cat and mouse.
Mrs. Sigal highlighted the fact that terrorist attacks have become very cheap and that, across millions of transactions linked to terrorist organizations, on average, one such transaction is less than $600. She emphasized that no money can flow to terrorists, because they can apparently MacGyver an explosive vest out of duct tape and supplies to kill hundreds. But, wishful thinking is one thing, and reality is another — although her office has over 800 seasoned professionals, she hinted that it doesn’t have the manpower to trace all cryptocurrency transactions.
Rather than talk about the danger of outdated computers in critical infrastructure, such as hospitals, airports, power plants, and schools, Mrs. Sigal suggested the only thing any government can suggest: the people should perform free labor for the government. She said in her speech that people who are in the business of accepting or transmitting cryptocurrency are seen as “money transmitters” who have to file regular reports on suspicious activities and abide by anti-money laundering regulations. That is, people who send or process cryptocurrency transactions have to snitch on themselves and each other, or they risk getting punished when others snitch on them.
That is a classic Prisoner’s Dilemma situation, in which two prisoners are tempted to snitch on each other in order to reduce their individual sentence. The catch is that if both stay silent, both will walk free, but if both snitch, both will get severely punished. When played with actual people and repeated over hundreds or thousands of rounds, the prisoners always discover that the best strategy is to say nothing and do nothing.
Study of Monero Traceability
Monero will soon get more attention, this time in the form of academic research. In May 2020, Carnegie Mellon University published a study titled “Alt-Coin Traceability” in which they explore the transaction traceability of Monero. First launched in 2014, Monero transactions initially did not mandate decoy ring signatures (called “mixins” in the study), which made it fairly easy to trace pretty much all Monero transactions. But, in the 2016–2018 period, the Monero network was upgraded several times, and mixins became mandatory, with their number rising to 10. If you’re interested in how ring signatures work, I wrote a section on them in my article on Monero traceability.
The authors of the study found a clever way to trace Monero, one that has to do with impatience. They realized that the vast majority of Monero holders will spend their Monero as soon as they get it. By grouping together transactions that happened within, say, 5 minutes of each other, it becomes easier to eliminate unrelated transactions and narrow down who is sending Monero to whom. The study cites an experiment that was run in 2017 and used a network with zero mixins, leading to 90% accuracy. Once you can identify some owners of transactions, the entire network’s privacy starts unraveling, revealing Monero owners even when they used the maximum number of mixins.
CipherTrace Develops A Monero Tracking Toolset
In August 2020, a cryptocurrency analysis firm, CipherTrace, proudly announced that it developed a toolset for the Department of Homeland Security to trace Monero transactions, which took them two years and netted them $2.4 million from a government contract. The Twitter (now called “X”) post with the announcement now leads to Mastercard’s website, indicating Mastercard acquired CipherTrace. Still, the announcement was enough to spark a heated debate — can the IRS track Monero with that tool?
The Cipher toolset apparently allowed visualization of Monero transactions, but it was not as precise as tools that do the same with Bitcoin transactions. The reason was that the toolset presumably gathered public information from exchanges, or in the words of the CipherTrace CEO, “It’s really more of a probabilistic game.” So, how reliable was the toolset? The same CEO stated that the chance goes as low as 78%, which shouldn't be good enough to be accepted in court. The only use for such a toolset and its visualizations is to give law enforcement agencies leverage so that they can put people in a Prisoner’s Dilemma and make them snitch on themselves or others. If those people say and do nothing, the toolset is useless because any lawyer worth his salt can challenge its results in court and get them dismissed.
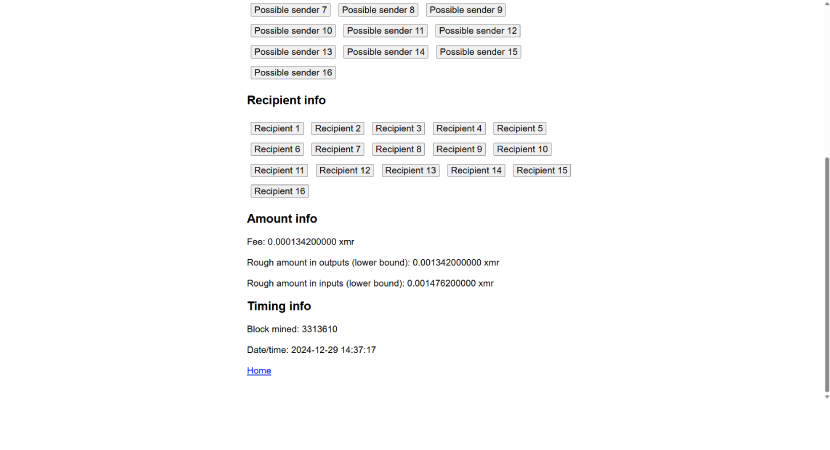
By 2024, Binance and other cryptocurrency exchanges delisted Monero, which also removed a lot of information on Monero transactions that those kinds of tools used. There are still tools that can do a transaction analysis on Monero, but they can’t do any kind of automated clustering analysis. One of them is eXaMineR, and it allows you to go into any Monero transaction and eliminate mixins one by one until you’ve narrowed down the possible senders. How do you know which mixins can be eliminated? If you’re one of the senders or recipients, you can cross out your transaction details to narrow down the list of potential suspects. The below screenshot shows it in action.
IRS Ramps Up Pressure On Cryptocurrency Holders
That same month, the IRS sent a new wave of tax warning letters to suspected or known cryptocurrency holders, asking them to amend their tax returns. The letter came in three variants, with one being a stern warning that promised an audit in case the recipient failed to respond and the other two being educational letters on the recipient’s obligation to pay taxes on cryptocurrencies. Those letters were first sent out in 2019 to 10,000 recipients, indicating a new chapter in the Can the IRS Track Monero saga.
In September 2020, the IRS posted a tender asking applicants to provide tools and methods for tracking Monero transactions, which the IRS couldn’t do itself because of “limited investigative resources.” The tender was posted by CI (Criminal Investigation), the same division of the IRS that brought down the dark web marketplace Silk Road, and it offered $625,000 to anyone who can provide innovative solutions that can reveal any information related to people doing Monero transactions. Applicants first had to submit a prototype and then refine it so that it works alongside IRS’ internal tools and systems.

In October 2020, two investigation companies experienced in cryptocurrency matters, Integra Fec and Chainalysis, applied to the tender and promised to deliver tools and methods for cracking Monero’s privacy features and tracking its transactions. The tender terms stated that each applicant had 8 months to deliver a working solution to get paid. Neither company’s website shows announcements or news related to either accepting or completing the tender for the IRS.
In August 2021, CipherTrace announced a new set of enhanced tools for tracking Monero. The press release curiously focused on financial institutions and claimed CipherTrace’s tools are the perfect solution to minimize money laundering risks that come with cryptocurrencies. One month later, Mastercard bought CipherTrace, indicating that the announcement was just to fluff up the company price before acquisition.
Mass Delisting of Monero
Unable to track Monero transactions to a satisfying degree, the US government started pressuring cryptocurrency exchanges to delist Monero or they’ll be shut down. On October 15, 2021, the US Department of the Treasury issued a press release focused on curbing ransomware threats by stopping payouts to criminals. Instead of finally updating critical infrastructure computers running Windows XP or 7 that can be shut down by a rogue employee with a USB stick, the US government focused on punishing the middlemen. The first victim was SUEX OTC, an exchange where 40% of transactions were linked to adversaries, meaning the majority of transactions were harmless. The exchange was put on the sanctions list, effectively shutting it down.
Other exchanges will feel the heat too, leading to a wave of Monero delisting. By the end of 2024, these exchanges denounced Monero:
- Bittrex
- Kraken
- ShapeShift
- OKX
- BitBay
- Huobi
Japan and South Korea have banned Monero completely, while Australia is on the verge of it, encouraging banks to delist it. I have to mention the sudden LocalMonero shutdown in May–November 2024 as well, which is in retrospect clearly a victim of the same push.
As a result of the stigma around Monero, even ransomware negotiators don’t want to deal with it, because they can be seen as accomplices. If there’s a thorough investigation into the ransomware incident, a negotiator will be unable to explain what he did with Monero or provide any proof that he tried to help. The stigma around Monero means that an institution infected with ransomware that demands a ransom in XMR will have nobody to turn to.
Monero Network Improvements and Updates
Meanwhile, the Monero developers are diligently working on updating and upgrading the network to minimize the exposure of transaction details to the public. On April 27, 2024, one of the Monero devs, Luke "Kayaba" Parker, posted a blog post on Full-Chain Membership Proofs (FCMP). Remember how the mixins started at 0 and then rose to 10? In an August 13, 2022, update to the Monero network, the mixin count was increased to 15, but with the proposed FCMP feature, the mandatory mixin count will be 100 million, effectively including the entire blockchain’s worth of decoy signatures with each transaction.
The goal of FCMP is to replace rings in the Monero network entirely and thwart potential attacks on the Monero network that come as a consequence of their use. One of those attacks is called “EAE attack” (Eve-Alice-Eve). Simply put, the EAE attack happens when a node in the Monero network repeatedly performs transactions with the same recipient in order to do a statistical analysis of mixins and other features of the network. There are other related attacks, such as Tainted Dust and Overseer, that refer to situations when more than one node is repeating transactions in order to analyze the Monero network. Those three attacks are still no better than the CipherTrace probability tool, but the devs want to discourage any kind of probing of the network.
Speaking of which, the same blog post talks about forward secrecy against an adversary that wants to use quantum computing to analyze the entire Monero network. The FCMP solution is only one of several proposals that explore how the Monero network can be upgraded without scrapping the entire XMR blockchain. The main feature of FCMP is sender anonymity, but other proposals include other features that are denoted as “Spend Authorization + Linkability” or “++.” Quantum computing is still far from being consumer-grade, but the gist of FCMP and FCMP++ is that the Monero community wants to make sure that the answer to "can the IRS track Monero" remains a definite “no.”
PlasBit’s Neutrality and Monero
Ten years after launching, Monero is the most resilient cryptocurrency. Despite being called out and specifically targeted by the US government, including the IRS, the network is still working just fine. That goes to show just how indestructible an idea can be when it’s developed in line with cypherpunk principles and worked on by the entire community. Monero’s resilience and indestructibility are what made it the target of those who see it as evil and the last refuge of those who see it as good. But, I posit that Monero is neither. Demon to some, and an angel to others, it may be a hellraiser, but it is ultimately just a tool to defend one’s privacy, which people have been doing for centuries. Monero is a digital whisper inside a digital envelope carried by a digital courier and passed on in digital darkness behind closed digital doors and after a secret digital handshake.
PlasBit is also neither good nor evil; it is just an exchange, albeit one that’s in line with Monero’s idea of resiliency and indestructibility. PlasBit's goal is to be neutral, no matter what happens in the world, and provide services within reasonable limits and legal restrictions to everyone we can. We are also a community, one that's working on promoting cypherpunk ideals of strong privacy and financial independence through electronic technologies, come hell or high water.







