A cryptocurrency wallet gives each individual the ultimate power to decide over his or her finances, or at least that’s what it’s supposed to do. But, one such wallet also has to work its magic by contacting the ethereal world of the Monero network, where many angry and malevolent spirits roam. To work properly, a Monero wallet needs to contact the ethereal plane of the internet, dodge the malevolent spirits, and update its balance sheet, which is called “syncing.” The question is then, How long does it take Monero daemon to sync? It usually takes about 13 hours if you choose the “advanced” option, which means having your own local node and downloading the 70+ GB blockchain file to your computer, but if you use simple mode and connect to a remote node, which is the computer of another user who has the blockchain synced, the download size is about 3–5 GB, which will take about 15 minutes. These time estimates also depend on your internet connection, the type of wallet you choose, the PC hardware, and the node settings. In extreme cases, when the wallet has not been synced with the Monero blockchain for a long time (a few years), it’s easier to make a new wallet and transfer your funds to it.
Here is an explanation of why it can be a maddening experience to wait for the XMR wallet to sync and what it has to do with demons.
The Internet is Made of D(a)emons
One theory states that the entire internet is demons communicating with one another. The theory makes much more sense when we take a look at the history of cryptographic communication, in particular the three tomes of “Steganographia” printed in 1606. The book was thought to have been one of the early works on black magic, especially with regards to summoning spirits to do the owner’s bidding. However, Steganographia is actually a work on cryptography, in which the mystique of black magic and demonology is used to add another layer of security to messages supposedly conveyed by spirits.
People who wanted to hide their communication would bury it under layers of drivel, which to others sounded like they were possessed by demons. In effect, the hidden message was indeed conveyed by a spirit, who would whisper it only to those in tune with the demonic world. If you take a look at internet traffic, you would see something similar — a deluge of drivel in which there is a meaningful, valuable message known only to the sender and the recipient. That’s the case with Monero traffic as well, leading to confusing and frustrating situations as you wait for the XMR wallet daemon to sync with the Monero network.
The demon/daemon reference is not a coincidence. In a rare instance of creative inspiration, computer scientists in 1963 decided to name computer processes that silently run in the background “daemons,” referring to unseen spirits that arrange everything in the world, which was an idea apparently used in physics as well to explain how atoms and molecules move about. Monero wallets also use a daemon to sync with the Monero network, and how well your XMR wallet daemon works is the biggest factor in how long it takes for your wallet to sync.
Why Does a Monero Wallet Sync?
In short, a Monero wallet has to update its private ledger and make sure everything is legit by copying a part of the XMR blockchain or the entirety of it. The easiest way to understand that process is to imagine a bank using a spreadsheet to keep track of financial transactions and account balances. Each transaction is recorded in a separate cell in the row, and when the day is over, another row is added and the process is repeated. But, in that kind of spreadsheet, the data would be searchable, readable, and copyable. That’s not the case with Monero, which focuses on privacy and encrypts the data, which is why the answer to how long does it take Monero to sync? is not clear-cut.
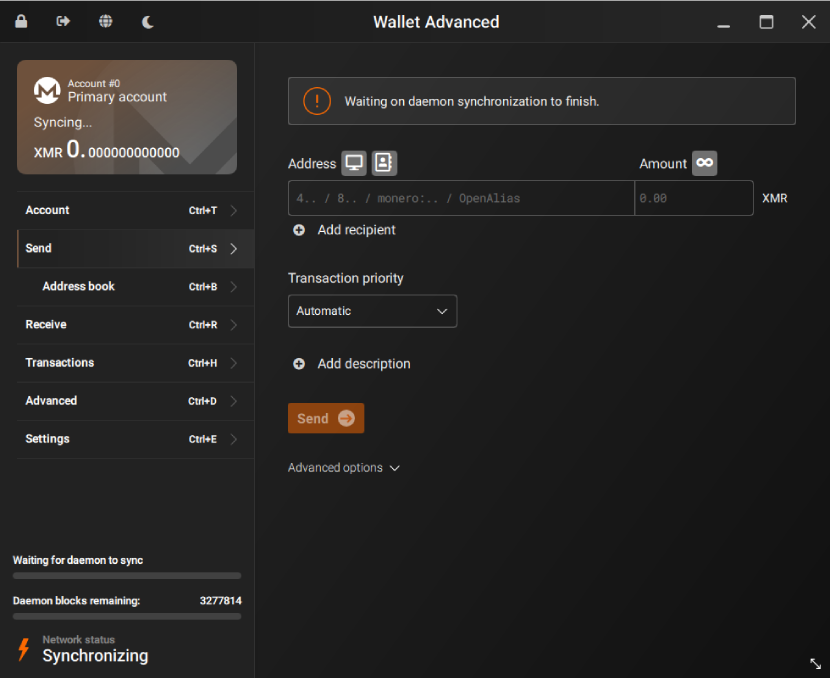
To obfuscate transaction details and user balances, Monero’s blockchain is designed so that each “row” is encrypted, meaning that human-readable data is turned into strings of seemingly gibberish data so that only the person with the original data knows what it is. The kicker is that in XMR’s case the wallet needs to go through all the transactions and decrypt them all to know which ones belong to the wallet. In a bank, there are supervisors and procedures in place to ensure that people and systems who fill out the spreadsheet don’t make too many mistakes, and when they happen, that they can be reversed. That is because banks rely on trust, which is not how Monero works.
Sync Times Explained
Monero wallets operate under the following three assumptions, which are the three reasons why there is no clear answer to how long does it take Monero to sync:
- nobody can be trusted
- Monero is sent in an adversarial environment
- all metadata is being gathered and analyzed by an adversary
When a fresh Monero wallet is first started up, it tries to connect to a Monero node and download the “spreadsheet,” which in Monero’s case is called “blockchain,” and go through it row by row, which are in XMR terms called “blocks.” There is nobody to do the work the wallet has to do, because that could be an adversary looking to defraud the user, so the wallet does all its calculations from the very first block. That’s why the initial sync takes so long. The wallet will still need to sync up before a transaction is processed, but the daemon will do it every once in a while and keep everything running smoothly.
Speeding Up Sync With a Remote Node
A Monero wallet takes gibberish from the Monero blockchain, verifies its integrity, and then stores it locally. There is a shorter way — you can connect to a remote node that will scan the XMR blockchain for you to speed the process up, but that introduces some risk in the process. Remote nodes are seen as unreliable because you have to share some data with them, though that may help improve wallet sync times for XMR users who are already having an unreliable internet connection. Here is a list of 250 remote XMR nodes and their info, such as how out of sync with the blockchain they are and which extra features they have.
When the wallet reaches the most recent block, it still has to sync up, but instead of days, it only takes minutes or hours, again depending on circumstances, which is why there is no definitive answer to how long does it take Monero daemon to sync. But, we did run a test that revealed it’s indeed a maddening wait.
Our Test of XMR Wallet Syncing
We tested the official XMR wallet sync time on our hardware at PlasBit. We used a machine with these specs:
- CPU: i5-13400 CPU
- Storage: Toshiba 1 TB SSD
- RAM: 16 GB
- Internet speed: 900 Mbps download and 100 Mbps upload
That’s a solid workstation that can handle pretty much any general computing task. For that computer, the answer to how long does it take Monero daemon to sync was 13 hours in advanced mode, during which the daemon used roughly 70 GB of traffic.
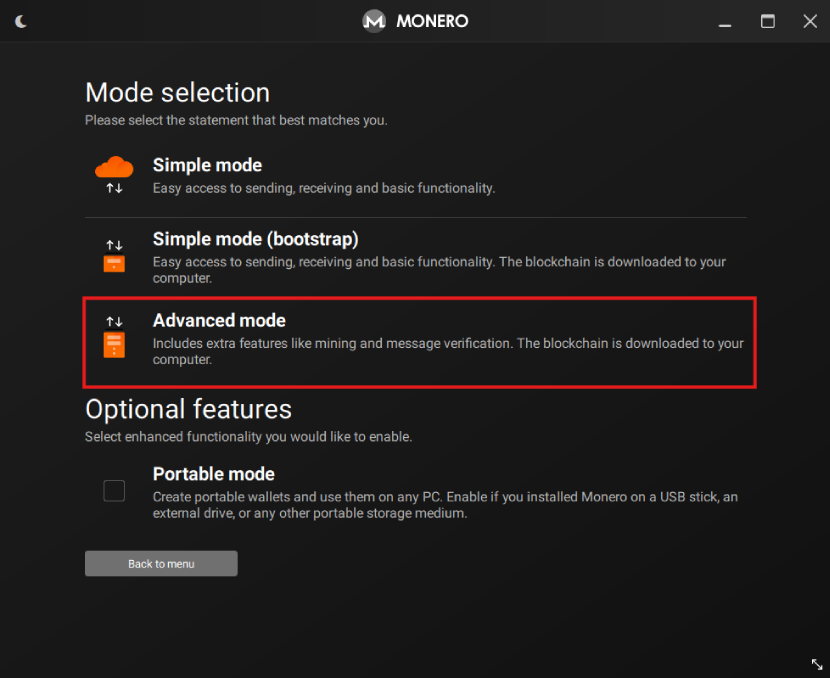
The advanced mode downloads the entire XMR blockchain, but there is also the simple mode, which makes some privacy and security concessions to significantly cut down the time needed. The problem with the simple mode is that you need to put some trust in either hardware or software you don’t control, which exposes you and your metadata to potential adversaries.
Why Bank Transactions Are Instant
Banks use shortcuts that depend on mutual trust to ensure that their clients don’t have to wait around for the transaction. When a bank receives a seemingly valid transaction, it has systems in place to automatically approve it, trusting that both parties are acting in good faith. The details of the transaction are kept in the “spreadsheet” and someone will eventually take a look at that client’s transactions to make sure they are not fraudulent. If there is a police investigation later on into that client, all the details of all their transactions are available for analysis in a plainly readable format.
Other financial institutions also trust their users, creating a circle of trust. For example, when you send money from your PayPal account to your bank account, the transaction is instant. If you take a closer look at your bank account after a couple days, you’ll notice the money is available for spending right away, but the transaction took 3–5 working days to actually process; in that time, the bank had people look over your transaction and confirm it. That in itself doesn’t sound problematic, but combine it with how the internet works, and there’s potential for disaster if there are adversaries in the system.
The Internet of Trust
It turns out that banks aren’t the only ones using the principle of mutual trust. When you connect to the internet, there is implicit trust between all the parties involved that your traffic will end up where it’s supposed to go and that the other side’s response will end up with you. Your request for a specific internet address is sent to your local ISP, then your regional ISP, then your national ISP, which puts it in a pool of requests from which ISPs from the entire world can take what they please.
The official name for this is “border gateway protocol” and you can find a very boring and technical explanation of how it works, but the gist of it is trust. All the ISPs trust each other that nobody will take what isn’t theirs and send users to the wrong address, which does happen from time to time due to glitches and human error. Now combine that with the fact that financial transactions are also sent over the internet, and you should start to see the reason why Monero takes so long to sync.
In April 2017, a Russian ISP started siphoning traffic that did not belong to it but didn’t take just any internet traffic. The ISP curiously focused only on traffic related to financial institutions, such as Mastercard and VISA, and select security companies, such as Symantec. The incident was caused by the government-controlled Rostelecom and lasted about 6 minutes, during which 36 blocks of internet traffic were affected in a way that suggested intentional hijacking. The traffic apparently still ended up where it’s supposed to be, but it passed through Russian-owned hardware, allowing Russians to analyze it.
How Metadata Analysis Reveals Private Info
Even the mere metadata analysis of financial and security transactions can tell a lot about who is paying whom for what, especially when done across a group of people interacting with a common target. For example, if Alice sends a payment to Bob right around New Year’s Eve, it could be anything. But, if Bob receives 49 other payments for the exact same amount around the same time, it’s possible that there’s some sort of event where Bob is the organizer and the amount is the entry fee.
Therefore, based on metadata analysis of just the amounts and times of those transactions, it’s a possibility that there will be a New Year’s Eve party with 50 guests and that Alice will be one of them. Meanwhile, Alice, Bob, and the 49 other guests think that their transactions are private and that nobody knows they’re going to Bob’s party. If one of them does something illegal at the party, Alice, Bob, or any other attendees can be implicated in the act because there is data leading back to them. In short, that’s called “guilt by association” and is fairly common when law enforcement agencies need to save face by persecuting whoever is a possible culprit.
Combine that kind of persecution with automated analysis of social media content and you get a scary panopticon in which all behavior patterns and associations become known to an unseen party that can at any time decide to act to stop potential offenses and wrongthink. The worst part is that law enforcement agencies don’t even need probable cause to do this kind of invasion of privacy; by using financial services of any bank and social media, we all waive our right to privacy. Go ahead, read Facebook’s/Meta’s Terms of Service, and you’ll see that they aren’t even hiding it; they call it something along the lines of “sharing data with third parties to improve our services.”
How Roger Ver Got Busted
The Alice scenario sounds like paranoia until something like it actually happens. I recently wrote about Roger Ver’s arrest in Spain, which was due to a similar kind of transaction metadata analysis that we imagined Alice in. Basically, in 2014, Roger renounced his US citizenship but allegedly forgot to report all his Bitcoin, for which he was supposed to pay taxes. In 2024, based on something the US government calls “clustering analysis,” which supposedly discovered that Roger had a hidden Bitcoin stash, he was arrested and extradited to the US.
Besides the fact that the phrase “clustering analysis” is just a fancy name for guilt by association, Roger’s fault was that he publicly associated himself with a Bitcoin wallet while thinking he’s beyond reproach. As soon as he did that, any transactions going through that wallet became associated with him, but it took 10 years before he realized how wrong that choice was; his arrogance was his undoing. Staying private in the cryptocurrency world requires leaving a minimal footprint whenever you use crypto, which is why XMR is my favorite crypto.
Prior to his arrest, Roger also dared to publish a book that criticized Bitcoin, for which there are strong indications that the US government will take it over and turn it into a regulated, taxable financial asset. For that, it needs to funnel as many crypto users into BTC as possible before springing the trap. In any case, it is indisputable that the US government is conducting a “clustering analysis” on Bitcoin wallets, tracking where the funds are moving and trying to nab people for dodging taxes.
Monero’s Privacy Protections
Monero is unlike Bitcoin in that it is designed to thwart all metadata and clustering analyses and provide maximum privacy protection through several mechanisms. That comes at the cost of less trust in the system and its components and longer waiting times due to wallet syncing and all the daemons conversing with each other. Those protections are all based on code and encryption, such as:
- RingCT
- Stealth Addresses
- Ring Signatures
Combined, they make it all but impossible to figure out who owns which Monero wallet and who is sending Monero to whom, but any government can still track users through their IP addresses, associate them with a potential offense, and just arrest the whole lot. ISPs are a massive weak point in internet traffic security, aggregating metadata on users, which can reveal cryptocurrency users and their activities.
That problem is likely to remain unsolvable in the foreseeable future, because it has to do with the underlying infrastructure of the internet. You can’t avoid using it, but you can minimize the impact of ISPs on you by switching things up a bit from time to time, such as by using a different VPN or just a different hardware or software setup. Whenever possible, use default values, because someone can track you through your settings. For example, it's possible to fingerprint Tor or clearnet users based on which window resolution they’re using or which fonts they have installed.
Monero Wallets
The biggest part of the answer to how long does it take Monero daemon to sync is your hardware, but the XMR wallet you use also factors into it. Here is a brief overview of the most popular XMR wallets out there. Choose at your discretion and only after thorough research.
Exodus Wallet
This is a closed-source Monero wallet, which means its actual software code is hidden. The Monero community considers this a red flag, because it requires users to trust it, while Exodus Wallet could be doing anything behind the scenes to compromise wallets and balances. Indeed, some hacking attacks on Monero wallets were done on users who used Exodus Wallet, though that isn’t conclusive proof Exodus Wallet is unsafe.
Cake Wallet
Cake Wallet was launched in 2018 and quickly gained a reputation for being user-friendly. It is an open source wallet, meaning you can check out its code and compile the wallet yourself if you so choose. Cake Wallet is available for mobile devices too and features Cake Pay, a service with which users can purchase goods and services using crypto. It supports background syncing and has the “Aggressive” setting for syncing, which further reduces XMR sync times.
Feather
Another open source wallet, Feather was launched in 2020 with the goal of making XMR use beginner-friendly. It is a lightweight wallet written from scratch in C++ and can be run in virtual machines too. Feather supports hardware wallets and multiple operating systems that focus on privacy. Users are invited to find and report bugs that can lead to loss of funds in Feather, which will get them a bug bounty of up to $3,000 in XMR.
Monerujo
Android-only open source wallet for XMR that is available on the Google Play Store. It has the SideShift exchange integrated into the wallet, allowing users to convert XMR for BTC, DASH, DOGE, LTC, and ETH. The gimmick of this wallet is the CrAzYpass (sic!) encryption, which has a dedicated whitepaper authored by the Monerujo head developer, m2049r. The CrAzYpass encryption asks the user for a password, hashes it with the CryptoNight algorithm, and uses the hash as the actual password for the wallet.
PlasBit As A Trusted Partner
Traditional banking requires full trust and little time, while syncing a Monero wallet requires zero trust and a lot of time. Those are two extremes, each of which has a trade-off, but I think there is a happy balance, which is finding trusted partners to build long-term relationships with. For me, that partner is PlasBit, which has shown a fervent dedication to cypherpunk principles, especially the notion of digital privacy and decentralization, which is something we sorely need in today’s era of mass uniformity. You can read more about in my article about PlasBit being a cypherpunk torchbearer.
No matter what you choose, you will have to use the internet, which is quickly becoming a tool for surveillance. It is being subverted and used against us, particularly by adversaries equipped with automated solutions, so we have to network and innovate in line with cypherpunk principles to create something brand new that can’t be exploited so easily. You can do it all alone, of course, but beware of having to face your daemons.







