The FBI has accused Tornado Cash of allowing the Lazarus Group, a sanctioned North Korean cybercrime organization notorious for some of the largest hacks in crypto space history, to launder hundreds of millions of dollars from their hacking proceeds. Roman Semenov co-founded Tornado Cash, the notorious crypto mixing service accused of enabling over $1 billion in illicit transactions, including proceeds from major cyberattacks and ransomware. He is charged with one count of conspiracy to commit money laundering, one count of conspiracy to violate the International Economic Emergency Power Act, and conspiracy to operate an unlicensed money-transmitting business, and if found guilty of all counts, he faces a combined maximum sentence of 45 years in jail. Roman is a Russian national who fled the US, believably to Dubai, and got all of his assets blocked after getting into the FBI's most wanted list.
Cryptocurrency mixers
Tornado Cash was a Cryptocurrency mixing service. Cryptocurrency mixers, also known as cryptocurrency tumblers, are a service that mixes digital currencies to make it more difficult to trace the funds back to their original source. Mixers are often used to improve the anonymity of cryptocurrencies like Bitcoin. They work by pooling funds from multiple sources for a random period and then distributing them to destination addresses. This process makes it difficult to trace the exact origin of the coins because all the funds are lumped together and distributed at random times.
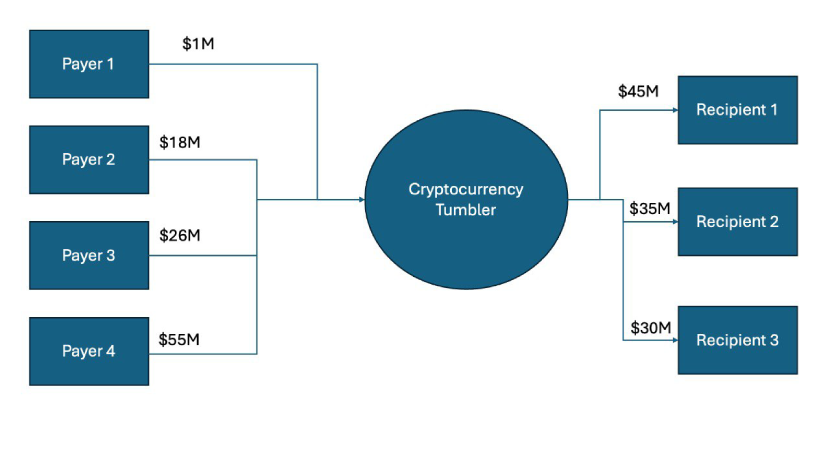
For instance, in the diagram above, four entities are paying a total of $100 in whatever crypto is supported by the tumbler, and three recipients receive a total of $100. The tumbler mixes the currencies received from the debtors and distributes the total among the creditors, according to the total amount owed to them, irrespective of who paid that amount and what was used to pay it. Mixers can have legitimate uses, such as enhancing privacy. However, they are also often used by criminals to launder money from illegal activities like drug trafficking, fraud, and extortion. Mixers provide anonymity, but legitimate users could unknowingly pool their coins with criminals. There isn't much information about how many cryptocurrency mixers exist, but in 2022, the U.S. Treasury Department did not just sanction Tornado Cash; they also sanctioned Blender.io, making it illegal for U.S. citizens, residents, and companies to use them.
Are Cryptocurrency mixers illegal?
The concept is not illegal; its implementation can be. The idea of enhancing privacy in cryptocurrency transactions is not necessarily unlawful. Mixers who follow KYC and AML rules can operate legally; for instance, if all the entities mentioned in the diagram above had been subject to KYC rules, the operation of that mixer would be considered legal. The case for questionable legality of cryptocurrency tumblers is based on the lack of KYC and the consequent potential use of mixers for illegal activities, money laundering, and financing terrorism. Most countries have strict KYC and AML rules; those jurisdictions tend to monitor currency tumblers very closely and stop currency tumblers that do not follow them.
Tornado Cash
Tornado Cash is an open-source, non-custodial, fully decentralized cryptocurrency tumbler that runs on Ethereum Virtual Machine-compatible networks. It offers a service that mixes potentially identifiable or "tainted" cryptocurrency funds with others to obscure the trail back to the fund's original source. It is a privacy tool used in EVM networks where all transactions are public by default. The project is governed by a decentralized autonomous organization(DAO) that uses the $TORN token as a voting system for protocol updates. Tornado Cash uses multiple smart contracts that accept different quantities of ETH and ERC-20 deposits. These deposits can later be withdrawn to a different address by providing cryptographic proof, breaking the link in the chain between the sender and the recipient. Zero-knowledge proofs increase privacy, as there is no way to link a withdrawal to its deposit. In August 2022, the Office of Foreign Assets Control (OFAC) alleged Tornado Cash had been laundering more than $7 billion in Cryptocurrency since it became operational in 2019.
OFAC further alleged that Tornado Cash was an essential tool used by North Korea's Lazarus Group to launder $455 million worth of stolen crypto funds; OFAC added it to the Special Designated Nationals (SDN) List, a list of individuals and companies acting for on behalf of targeted countries. The list also includes individuals, groups, and entities, such as terrorists, narcotics traffickers, money launderers, etc, that are not explicitly associated with a targeted country. In November 2022, OFAC re-designated Tornado Cash based on its alleged use by North Korea to launder illicit proceeds of cybercrime and theft of digital assets. According to the Treasury, the increased anonymity and complexity in tracking funds flowing through Tornado Cash begs to be exploited by bad actors. OFAC claimed that Tornado Cash had inadequately prevented its misuse for malicious cyber activities. They successfully claimed that Tornado Cash was not just open-source code but technology packaged and offered as a business service by an association of people.
The legal case against Tornado Cash co-founders
U.S. treasury and Dutch authorities' legal case against the individuals behind Tornado Cash, Alexey Pertsev, Roman Storm, and Roman Semenov, was based on their providing a business service without asking questions as to the identity of the users or the motives behind their using it. The US law enforcement agencies charged Roman Storm and Roman Semenov with three indictments.
- Conspiracy to commit money laundering.
- Violations of the International Economic Emergency Powers Act (i.e. violations of sanctions).
- Operating an unlicensed money transmitting business.
Roman Storm is currently under arrest in the US. His legal team filed a motion to dismiss the charges on account that he was only a developer, but it was not successful at the time of writing this article. Law enforcement agencies in the US and the Netherlands argued that Alexey Pertsev, Roman Storm, and Roman Semenov were not just software developers but were also running a service. Semenov was actively involved in promoting Tornado Cash in media and on online platforms, where he provided Tornado Cash users with advice on anonymizing their transactions. After Semenov was alerted that Tornado Cash was being used to launder large volumes of stolen virtual currency for the Lazarus Group, he and his fellow co-founders continued to pay for infrastructure supporting the Tornado Cash service and took steps to increase the anonymity of the Tornado Cash service without appropriate measures to address the known illicit use by North Korea.

In April 2022, Semenov learned that an Ethereum address that was publicly attributed to the Lazarus Group and identified on the Specially Designated Nationals and Blocked Persons List (SDN List), containing hundreds of millions of dollars in stolen proceeds from the widely publicized $620 million Ronin bridge heist, was being used to send funds through Tornado Cash’s service. Semenov and his fellow co-founders put in place a front-end sanctions screening service, but did so knowing that this would be easy to evade, and did not take steps to sufficiently address active abuse by North Korea. Despite his possession of information from publicly available blockchain analysis and inquiries from media, Semenov consistently ignored or downplayed the evidence that Tornado Cash was being used to launder stolen virtual currency for North Korean, continued to participate in the operation and maintenance of the Tornado Cash service, and took no meaningful actions to prevent or mitigate the risk of actors using Tornado Cash to launder proceeds from their illicit activities following subsequent high profile heists.
The Lazarus Group
The Lazarus Group, also known as Guardians of Peace or Whole Team, is a hacker group made up of an unknown number of individuals and alleged to be run by the government of North Korea. The United States Department of Justice has claimed the group is part of the North Korean government's strategy to undermine global cybersecurity and generate illicit revenue in violation of sanctions. According to a North Korean defector, Kim Kuk-Song, the unit is known as 414 Liaison Office in North Korea. The earliest known attack that the group is responsible for is known as "Operation Troy", which took place from 2009 to 2012. The operation was a cyber-espionage campaign that utilized unsophisticated distributed denial-of-service attack (DDoS) techniques to target the South Korean government in Seoul. They were also responsible for attacks in 2011 and 2013. It is possible that they were also behind a 2007 attack targeting South Korea, but that is still uncertain.
A notable attack that the group is known for is the 2014 attack on Sony Pictures. The Sony attack used more sophisticated techniques and highlighted how advanced the group had become. The Lazarus Group reportedly stole US$12 million from the Banco del Austro in Ecuador and US$1 million from Vietnam's Tien Phong Bank in 2015. They have also targeted banks in Poland and Mexico. In 2016, a bank heist attributed to the group included an attack on the Bangladesh Bank, successfully stealing US$81 million. In 2017, the Lazarus group was reported to have stolen US$60 million from the Far Eastern International Bank of Taiwan. However, the actual amount stolen was unclear, and most of the funds were recovered.
The Ronin Network Heist drew OFAC's attention to Tornado Cash
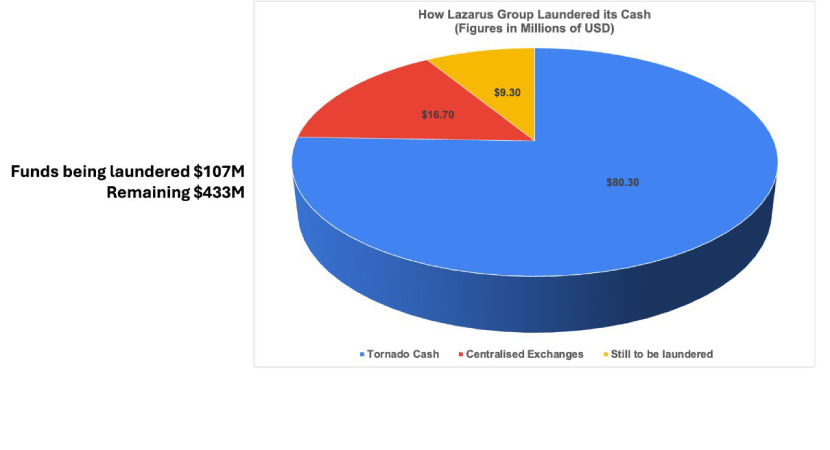
The Ronin Network is tied to the popular blockchain game Axie Infinity; it suffered a security breach on March 23, 2022. Sky Mavis, a blockchain gaming company, built and controlled the Axie Infinity game. The hack involved the compromise of Sky Mavis's Ronin validator nodes and Axie DAO validator nodes, which allowed the threat actor to drain the funds from the Ronin bridge in two transactions. The Ronin chain has nine different validator nodes; five are needed for any deposit or withdrawal. Four Sky Mavis validators and 1 Axie DAO were hacked in the attack. As of April 14, 2022, the attacker had managed to launder 18% of the heist. Initially, the attacker converted stolen USDC for ETH in Decentralized Exchanges to prevent it from being seized. Issuers control stablecoins and, in some cases, can freeze tokens involved in illicit activities. Then, they started laundering $16.7 million worth of ETH through three centralized exchanges. As the affected exchanges publicly announced they would work with law enforcement to establish their identity, the attacker changed their laundering strategy and started using Tornado Cash to send transactions for $80.3 million worth of ETH. The attacker's blockchain activity shows that another $9.7 million worth of ETH is in intermediary wallets prepared to be laundered, most likely also through Tornado Cash. The remaining $433 million was left in the attacker's original wallet.
Investigators managed to track the stolen funds and labeled the addresses associated with the attacker, ensuring that the investigator's clients could be alerted if they received any of those funds. On April 14, 2022, the U.S. Treasury's Office of Foreign Assets Control (OFAC) announced new sanctions against the thief's Ethereum address and listed the owner of this address as Lazarus Group, a sanctioned entity in the U.S. and, therefore, U.S. persons and entities could not transact with that address; the North Korea state-sponsored group could not cash out any further funds they continue to hold onto through US-based crypto exchanges. It is not surprising that the attack has been attributed to North Korea. Until 2021, the majority of criminal activities of the Lazarus Group were directed towards companies located in Asia. The Ronin network is decentralized, but its creators were located in Vietnam. Many features of the attack mirrored the method used by the Lazarus Group in previous high-profile attacks, including the victim's location, the attack method (believed to have involved social engineering), and the laundering pattern utilized by the group after the event.
This attack was also the smoking gun to link Tornado Cash with money laundering activities on behalf of the Lazarus Group and start the process that led to the Cryptocurrency mixer being sanctioned in the U.S. and its creators charged. Tornado Cash may be sanctioned in the U.S. and other countries but still operates. Apparently, the Lazarus Group went back to using it after the U.S. seized another Cryptocurrency tumbler, Sinbad.io, in November 2023. An investigation by Elliptic (a company founded in 2013 that pioneered the use of blockchain analytics for financial crime compliance) revealed that the Lazarus Group might have gone back to Tornado Cash to launder $112.5 million stolen from exchange HTX and its HECO cross-chain bridge in November 2023. According to other investigators, the Lazarus Group allegedly sent over 40 transactions to Tornado Cash in mid-March 2024.
Are they punishing people for writing code?
Many considered Alexey Pertsev's arrest and the charges against Roman Semenov controversial; protesters maintained that software developers could not be held accountable for their software use, especially if they provided open-source code. In the United States, many programmers think they are protected by the First Amendment, or, in other words, the right to free speech. Coding is a language; therefore, coding is the equivalent of expressing your thoughts, i.e., Free Speech. This argument has been challenged several times; for instance, in 2019, the US Justice Department charged several individuals with spoofing, using an algorithm to trick a market. One of them, a developer, was accused of creating an algorithm that enabled a London trader to overstate demand for stock market future artificially.
The tactic sparked the 2010 "flash crash" that saw the U.S. stock market lose $1 trillion in value in just 36 minutes. Programmers risk ending up on the wrong side of the law because they were involved in projects they thought were interesting but had criminal intent or could be used for criminal activities. The U.K. and the U.S. have passed laws like the Computer Misuse Act (U.K.), the Fraud Act, Data Protection laws, and the Investigative Powers Act. Consequently, programmers may be liable even if they do not know they are violating a law. However, the prosecution against Alexey Pertsev, Roman Storm, and Roman Semenov was not based on their having created open-source code. The prosecutors maintained that they did not just write open-source code; they had created an entity that provided a service and intentionally did not perform any KYC check or AML monitoring even when they became aware that Lazarus Group was using their services to launder money. In other words, they were not prosecuted as software developers but as co-founders of a business facilitating money laundering and handling funds from illegal activities.
The Legality of Privacy Enhancing Technology
Privacy Enhancing Technologies (PETs) themselves are not inherently illegal. For instance, encryption and anonymization tools are widely used and legal. Data protection regulations and user privacy rules can only be implemented using PETs. There are several legitimate uses of privacy-enhancing codes. Encryption Regulations and Compliance with Data Protection Laws governing the collection, storage, and processing of personal data benefit from solutions that anonymize data to comply with requirements for pseudonymization in regulations like GDPR. However, in some cases, PETs can raise questions of legal liability; for instance, they may limit the ability to identify the source of a breach. The line dividing the legal and illegal use of PETs lies with the activity that privacy-enhancing software is meant to protect. When it shields perpetrators of illicit activities, the legality of the software may be questioned. A software developer's defense rests on the awareness of the purpose of the code. Open-source code, for instance, is often used as a component for packages. The code may support a completely legitimate process, such as verifying a total; still, the nefarious purpose of the package can only become apparent once all the blocks are put together.
Why is Tornado Cash still active?
The U.S. and several European jurisdictions sanctioned Tornado Cash but could not close it. Its decentralized design, accessibility through alternative networks, legal ambiguities surrounding its use outside the U.S., and continued demand for privacy contribute to its ongoing operation despite sanctions. Tornado Cash architecture is built on the Ethereum blockchain, which means it operates through smart contracts that are not controlled by any single entity. This decentralization makes it resistant to censorship and shutdown efforts. The U.S. Treasury's sanctions make it illegal for any U.S.-based individual or entity to use it; still, the smart contracts continue to function because they cannot be altered or destroyed by any individual or organization, including the Tornado Cash DAO (Decentralized Autonomous Organization). The front-end interface of Tornado Cash is hosted on decentralized storage systems like IPFS (InterPlanetary File System) and can also be accessed through Tor, a network designed for anonymous communication. Tornado Cash remains legal and can be used in many other jurisdictions around the world. Consequently, users outside the U.S. can continue to utilize its services without legal repercussions. OFAC has indicated that it does not prioritize enforcement actions against individuals who have used Tornado Cash unless they are involved in other sanctioned activities. Tornado Cash also serves legitimate purposes for users seeking financial privacy. This dual-use nature has led to ongoing interest and utilization of the service among legitimate users and those with less scrupulous intentions.
Disclaimer: This article is intended solely for educational and informational purposes. It should not be considered financial, investment, or legal advice.







