Hacker attacks on smart contracts are the main danger for those who decide to invest substantial sums in cryptocurrency. In fact, although the blockchain is secure, transparent, and immutable, for this very reason, if a smart contract is altered, it becomes very difficult to fix the situation. This is exactly what happened with the PlayDapp hack!
What exactly happened to PlayDapp? PlasBit's research team worked hard to analyze the situation, and it was not easy, but we were able to reconstruct the scammers' attack process.
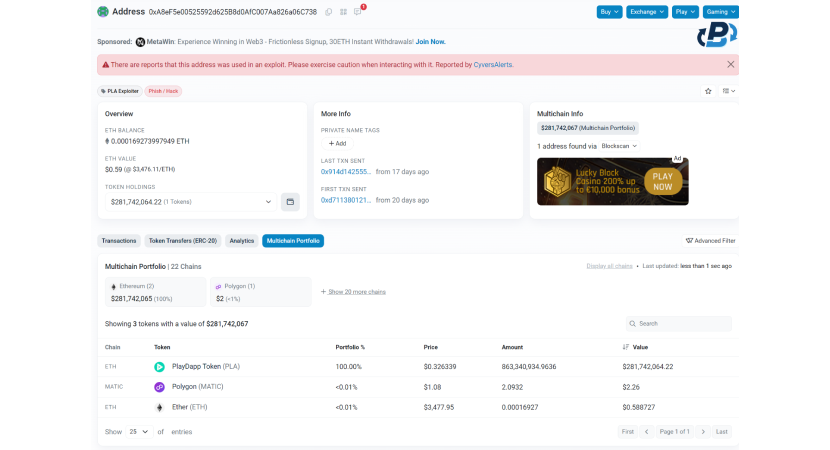
In the hacker attack on PlayDapp, scammers managed to get hold of a wallet's private keys delegated to manage the cryptocurrency's smart contract. In this way, by managing to secure full power over the smart contract, the scammers managed to undermine more than $200,000,000 worth of PLA tokens. Although the attack was successful and not just one, the situation did not turn out very positively for the hackers. In fact, they failed to convert the bulk of the loot and capitalize on the scam carried out. Let's understand the situation in detail!
PlayDapp Hack: What Happened?
It may seem like a complicated process, but we have managed to reconstruct it, and to make the explanation clearer, we will deconstruct the PlayDapp hack into several steps.
Step 1: Scammers Hack an Admin Wallet.
Hackers had to implement a well-thought-out strategy to gain access to the smart contract. In fact, in order to mint new PLA tokens, it is necessary to use one of the authorized wallets that own the smart contract, such as that of a project admin. In this case, the scammers, having probably studied their victim for months, were able to successfully derive the private key to access the wallet of one of the admins. Thus, having access to the wallet responsible for the smart contract, they were able to move on to the next step in this malicious scheme.
Step 2: The Smart Contract of PlayDapp is altered
Hackers, having managed to enter the wallet operator of the smart contracts, can carry out operations at will. On Feb. 8, PeckShield, a blockchain analytics company, announced in a post on X that 200,000,000 PLA tokens, worth about $26,000,000!!!, have just been suspiciously and improperly minted. It was at this stage that the hackers brought their plan to fruition, altering PlayDapp's smart contracts and token economy irreversibly. The improperly minted tokens could not be burned or deleted, and they are still in the scammer's wallet.
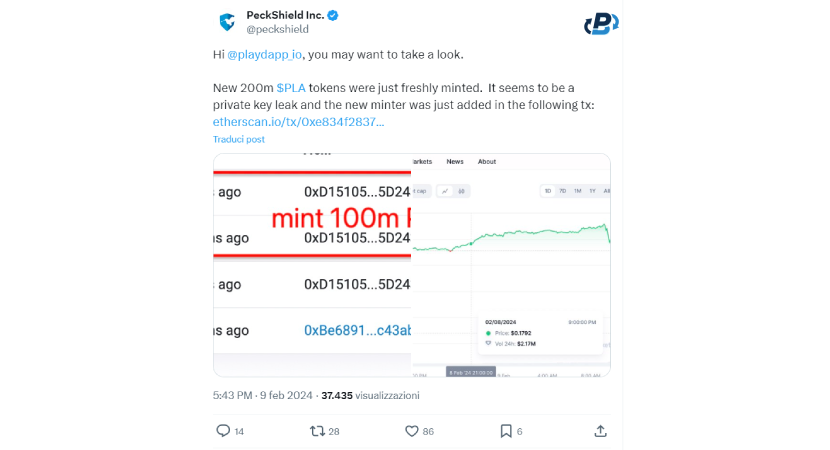
Step 3: PlayDapp Team Takes Proactive Measures
Although the situation was far from simple, the PlayDapp team reacted quite promptly. In fact, as soon as the hacker attack was noticed, the team took steps to contact all the major CEX and DEX on which the token is listed to prevent PLA exchanges and limit the scammers in their goal of converting their loot to fiat currency or other cryptocurrencies. Thus, with no way to cash out PLA tokens, the scammers found themselves in a stalemate, where they concretely owned more than $25 million worth of PLA tokens but could not trade them for any other asset.
Step 4: The PlayDapp Team's Request to the Hackers.
In order to be able to find a quick solution that could also restore the balance of the token economy and smart contract, the PlayDapp team proposed a deal to the scammer. The team, in fact, promised a $1,000,000 reward to the hackers if they returned the stolen PLA tokens. This was not enough to convince the scammers to abandon their plan, despite the fact that they could not convert the stolen loot anyway. So, despite the proposed agreement to resolve the situation peacefully, the scammers were not satisfied with this. And so they continued their diabolical plan.
Step 5: The Hackers Minted 1,590,000,000 More PLA Tokens
Ignoring the proposed deal and reward, the scammers attack again. A second, even bigger attack came on Feb. 13. The hackers minted another 1.59 billion PLA tokens, coming up with an impressive haul of about $255,000,000 in PLA tokens between the two attacks. Analyzing the situation in depth, we also understand that the hackers already knew that they could not gain anything from this attack because PLA token trading was already blocked. From here, we also understand that the nature of the attack might have a different purpose than mere financial reward, but it could probably be an act of sabotage.
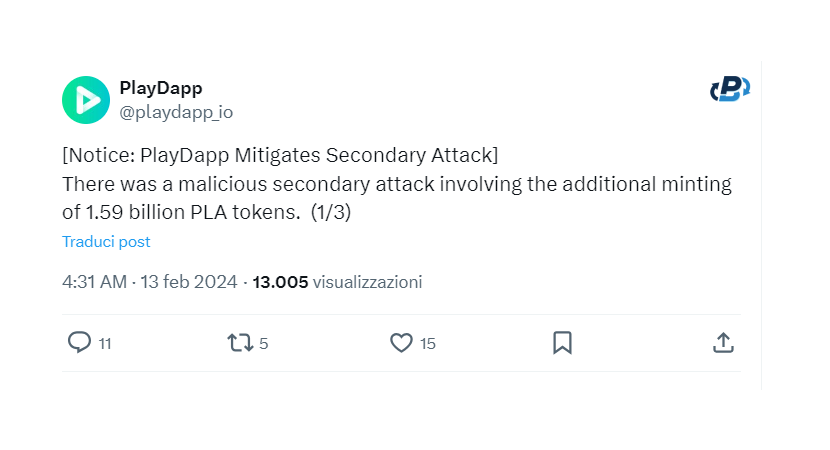
Step 6: The Solution Implemented by the PlayDapp Team
Having realized that the token economy was irreparably altered and that it would not be possible to regain possession of the PLA tokens stolen by the hackers, the PlayDapp team had to find an alternative solution. In fact, they decided to perform a token migration from PLA to PLD. In this way, although the process is complicated, legitimate holders of the PLA token can convert it at a 1:1 ratio with the new PLD token. By doing so, theoretically, only hackers would have been prevented from converting PLA tokens to PLD, automatically excluding their stolen tokens from the revamped token economy.
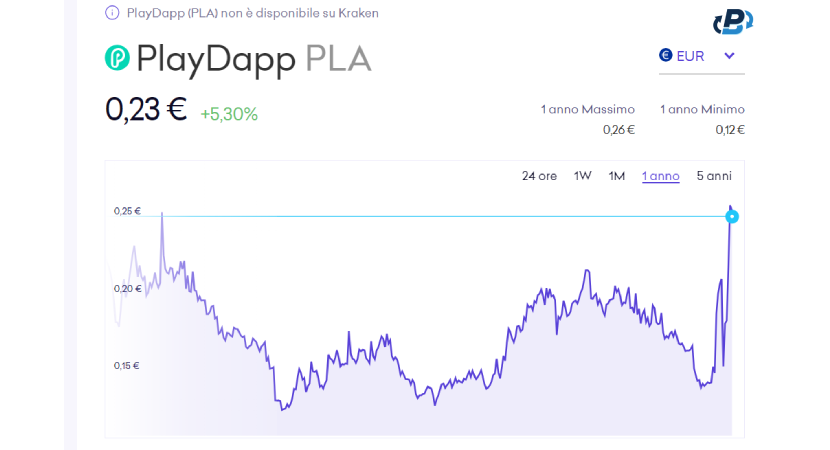
Step 7: The Price Impact of PLA Token
Although the most expected ending is a rapid collapse of the token, this was not the case. In fact, surprisingly, the price has gone from $0.14 to $0.23 today that we are writing. But how is this possible? Usually, after a hack, the price of a cryptocurrency decreases, but in the case of PLA, the price increases. Although the team is at fault for not implementing all possible security measures to prevent this unfortunate event, it still managed to respond promptly and responsively. In fact, by promptly blocking PLA trading on the major centralized and decentralized exchanges, they managed to limit the negative impact of the event on the price.
Moreover, by demonstrating transparent communication and trying to find a solution with the scammer, they showed that they were responsive as best they could and were ready to deal with even the most unpleasant misfortunes. This instilled a sense of trust and support in the community, which appreciated the team's moves and decided to support them. As they were also quite quick to propose migration from PLA to PLD, they also proved technically capable of solving a technical problem relatively quickly and efficiently. This also helped increase their media exposure and brought new investors and fans into the PlayDapp community.
Step 8: What Happened to Stolen Funds?
In the last step of this scam, you remain suspended in a stalemate. Indeed, although the hackers succeeded in their intent to improperly undermine and steal a large quantity of PLA tokens, they were unable to convert them. So, even having more than $250 million in PLA tokens on hand, they were unable to benefit from the loot because they were unable to exchange it. Although one cannot recover the stolen cryptocurrencies, one can still try to find a solution that remedies the damage done, as in the case of the PlayDapp hack.
PlayDapp: What is It and How Does It Work?
PlayDapp is an innovative platform that provides a gateway to gaming and game development by leveraging the power of blockchain technology. The platform aims to make blockchain games accessible to everyone, thereby promoting decentralization in the gaming industry. PlayDapp is committed to developing interoperable games that can be played across different blockchain platforms, thus creating a seamless gaming experience for users.
As a company that supports other blockchain innovators, PlayDapp is well-positioned to become a leader in the decentralized blockchain gaming space. The platform has demonstrated its commitment to innovation and excellence by consistently delivering quality services to its users.
Mission & Vision of PlayDapp Team
PlayDapp is a platform that is dedicated to making blockchain technology accessible to everyone, regardless of their level of familiarity with cryptocurrencies or Web3. They understand that not everyone is comfortable using cryptocurrencies yet and want to make it easier for people who only interact with Web2 to participate in Web3 games without having to deal with cryptocurrencies.
This is a significant step towards fostering inclusivity and making blockchain solutions more accessible to a wider audience. PlayDapp's focus on creating a user-friendly experience and gradually introducing users to blockchain solutions is commendable. Overall, PlayDapp's commitment to inclusivity and user-friendliness is a positive development for the blockchain industry. It shows that there are companies out there that are dedicated to making blockchain technology accessible to everyone and that the industry is continuing to evolve and become more user-friendly.
What is PlayDapp SDK?
The PlayDapp SDK service is a solution that simplifies and optimizes the integration of assets and data with Web3 infrastructure. It provides simplified integration tools, data conversion into the 3.0 format, facilitates data exchange between different Web3 services and platforms, offers data management and operational tools, supports integration with Web3 peer-to-peer marketplaces, provides a dashboard for monitoring indicators and analyzing Web3 data, and provides incentives for active participation in the Web3 ecosystem. Overall, the PlayDapp SDK enables developers and companies to fully leverage the potential of blockchain and decentralized technologies.
How Smart Contract Attacks Work?
Smart contracts are self-executing computer programs that run on a blockchain. They are designed to automatically execute a set of predefined instructions when certain conditions are met. Smart contracts are immutable and decentralized, meaning that once deployed on the blockchain, they cannot be modified or controlled by a single central authority. Attacks on smart contracts represent one of the most significant threats to the integrity and security of blockchain platforms and cryptocurrencies. To fully understand this type of attack, it is essential to have a deep understanding of how smart contracts work and the vulnerabilities that malicious actors can exploit.
Smart Contract Vulnerabilities
Despite their security and reliability, smart contracts can be vulnerable to various types of attacks. Some of the most common vulnerabilities include:
- Code Vulnerabilities: Smart contracts are written in programming languages like Solidity for Ethereum. Errors in the code can lead to security holes that can be exploited by hackers to manipulate the behavior of smart contracts.
- Unauthorized Access: If a malicious actor gains access to the login credentials of an administrator or an authorized user, they may be able to modify smart contracts or perform harmful operations.
- Hidden Backdoors: Sometimes developers may insert hidden backdoors into smart contracts that allow them or third parties to execute unauthorized operations.
- Manipulated Oracles: Smart contracts can interact with external data through oracles. If a malicious actor manages to manipulate the input of the oracle, they could influence the behavior of the smart contract in a harmful way.
Types of Smart Contract Attacks
Attacks on smart contracts can take various forms, including:
- Overflow Attacks: Overflow attacks occur when a malicious actor manages to exceed the maximum limit of a numerical variable in the smart contract attacks, causing unexpected behavior.
- Re-Entrancy Attacks: Re-entrancy attacks exploit the execution model of smart contracts to allow a malicious actor to repeatedly execute a function within the same contract, violating state control rules.
- Front-Running Attacks: Front-running attacks occur when a malicious actor exploits privileged information to execute advantageous operations before they are confirmed by other network participants.
- Market Manipulation Attacks: Market manipulation attacks involve the use of deceptive strategies to influence the price of a cryptocurrency or token.
The security of smart contracts is a critical aspect of the cryptocurrency and blockchain ecosystem. To safeguard against potential attacks, developers must adhere to strict security protocols and conduct frequent code audits to identify and address vulnerabilities. It is equally important for the cryptocurrency community to stay vigilant and work together in developing solutions that ensure the integrity of blockchain platforms. By doing so, we can mitigate the risks associated with smart contracts and protect the interests of all stakeholders.

Other Commons Scam Attacks in Web3 and Cryptocurrency
Unfortunately, because it is still unregulated and because users are still so inexperienced, Web3 is full of opportunities but also dangers. Hacker attacks, while frequent, are not the only threat that Web3 users and platforms face. In fact, more and more types of scams are emerging, like the recent PlayDapp hack, and keeping a proactive approach to avoid losing money in a scam is essential. Now, let's look at the most common types of scams so that you can be aware and recognize a potentially dangerous situation.
Pump-and-Dump Schemes
One of the most classic scams to which inexperienced investors must pay particular attention is the pump-and-dump scheme. In this fraud, a group of people create a cryptocurrency without any intrinsic value or potential, as in the case of the Squid Game pump-and-dump, and create hype for new investors to buy the project token. Once the malicious team collects a sought-after capitalization, they sell all their tokens to cash in on the new investors' money and collapse the token. This is a great risk for inexperienced investors who can suffer substantial money losses.
Slow Rug Pull NFT Scams
Slow rug pull NFT & scams are projects that originate with the idea of slowly cheating investors. In most cases, the team creates a lot of hype and expectations for the project, promising big developments and exponential growth. Despite this, in slow rug pulls, the team progressively wanes people's interests, as well as their ambitions for the project. In this way, the team has the opportunity to progressively squander the investors' funds without them being able to notice it. It is an evil type of scam because it is based on manipulating people's false expectations over a prolonged period of time, which can last even years!
Crypto Romance Scams
In crypto romance scams, the evil perversion becomes even more evident. In this type of attack, the scammer generally pretends to be a kind and empathetic girl with whom one can easily make friends. The scammer identifies his prey by looking for them to be mentally unstable and emotionally lonely in order to take advantage of their weaknesses to build a relationship of trust and love. Once the victim's trust has been won, however, the scammers convince them to make dubious investments in cryptocurrencies in order to squeeze the victims as much as possible. Once they realize that the victim has no more money available, they disappear into thin air, leaving the victim with no more funds and a broken heart.
Address Poisoning Attacks
In the address poisoning attack, also called the crypto dust attack, scammers use a well-thought-out technique to trip up the unsuspecting victim. They create a fake address that replicates the characters of a wallet the victim often interacts with and sends a small amount of cryptocurrency to the intended prey. In this way, they make sure that their fake address is at the top of the victim's transaction history, who, accustomed to sending money to a similar address, does not notice the subtle differences in the characters. So, she is mistakenly induced to send her cryptocurrencies to the scammer's fake address, which, as soon as it receives them, sends them to other wallets and causes them to lose their tracks irreparably.
ICO Token Sale Frauds
In mock or fraudulent ICOs (initial coin offerings), the team promises to create a cryptocurrency with utilities that can bring benefits to those who buy it. They may use different ways to lead users to make the purchase, including growth marketing strategies, market manipulation, and false promises. The outcome of this scam is actually quite simple: the team convinces people to buy this token with great promises and expectations when, in fact, the token has no intrinsic value, and the team disappears as soon as they collect the money from the sale. In other cases, even fake sites of other tokens are simulated so that transactions are made on the fake site instead of the real one, leading investors to lose significant amounts of money.
Fake Giveaway Scams
In this case, scammers leverage the use of artificial intelligence to make false videos promising attractive fake giveaways. For example, in one scam that our research team at PlasBit analyzed, scammers had an ad representing Brad Garlinghouse, CEO of Ripple, go viral on YouTube, altering his voice and having him talk about an incredible giveaway that should not be missed. In this giveaway, however, there are no prizes and only losses. In fact, he promised that by sending a given amount of XRP to the address shown, one would receive twice as much as a gift. Although it may seem like a trivial deception technique, many people fell for it and lost money, having trusted it by seeing a (fake) relevant person on YouTube.
Crypto Recovery Scams
We come to perhaps the worst of all Web3-related scams. The crypto recovery scam aims to scam people who have just been scammed. Sounds evil, doesn't it? Indeed it is and in no small part. In this type of attack, scammers target individuals who have had a problem with cryptocurrency and, for example, comment on Twitter asking for support. This is where the scammers come in, posing as devs who can help you recover your lost money. Predictably, however, to help you recover your lost funds, they demand payment upfront. Once they receive the payment to recover the funds, they disappear as well: in addition to the damage, there is also the prank!
In conclusion, although the cryptocurrency world is full of potential profitable investments, it is also full of numerous scam attempts like the PlayDapp hack. The dangers are many, and the only way to decrease the possibility of becoming a victim of scams is to act proactively. At PlasBit, we always recommend that you take a critical thinking attitude and focus on continually researching and improving your knowledge. Only by thoroughly studying the market, technology, and investment dynamics can you have a safe and challenging path in Web3. The world of blockchain is in the midst of a revolutionary phase, and a new interconnected and transparent world is emerging. Act proactively and secure yourself from potential threats so that you can focus on seizing the right opportunities!

 EN
EN









