In cryptocurrencies, where decentralized technologies promise financial autonomy, a sinister threat has emerged: Crypto recovery scams. This PlasBit's research delves into the disturbing world of this scam, exploring the mechanisms that scammers employ to manipulate and deceive, leaving a trail of financial ruin and shattered trust. As we navigate this threat, we will explore the legal and regulatory challenges in combating such crimes and propose strategies to fortify the cryptocurrency ecosystem against these predatory practices.
Definition of Crypto Recovery Scams
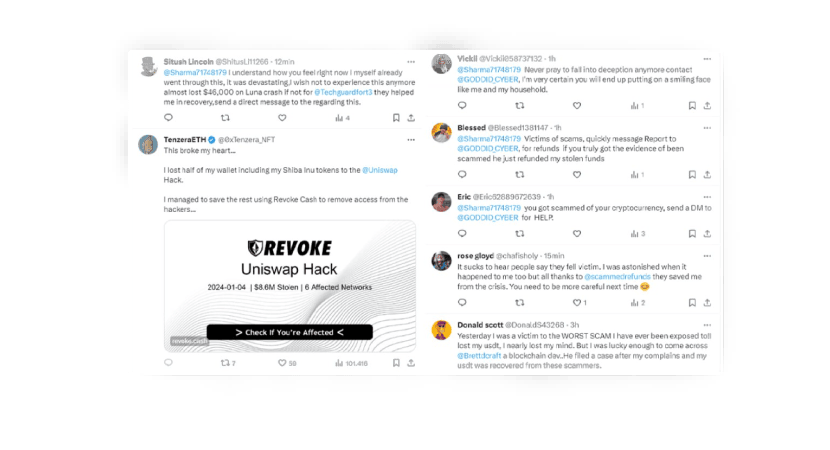
These scams target individuals who have incurred financial losses in the cryptocurrency market in a previous scam or wrong transaction. The scammers behind these schemes present themselves as companies or professionals specializing in recovering lost or stolen funds. They claim to offer recovery services that can swiftly and efficiently return investors' cryptocurrencies or funds.
How does this Scam Work?
- Step 1 - Victim Identification: Like in address poisoning attacks, the schemes start with identifying the perfect victims in recovery scams. Scammers may obtain information about individuals who have suffered losses through various sources, including online forums, social media, and previous data breaches.
- Step 2 - Persuasive Approach: Scammers employ a persuasive approach after identifying potential victims. They contact victims via comments on Twitter, email, phone calls, or direct messages on various social media. Utilizing social engineering tactics, they strive to convince victims of their legitimacy and the ability to recover lost funds.
- Step 3 - Request for Advance Payments: Once the victim's trust is gained, these scammers demand advance payments for their purported recovery services. These payments may be requested in cryptocurrency or traditional currency. Driven by the hope of recouping their losses, victims may be inclined to make these payments.
- Step 4 - Disappearance or Continuation of the Scam: After receiving payments, malicious actors have two options: they can vanish entirely, leaving victims without any recovery, or they can persist in requesting additional payments, asserting the need for further resources to complete the recovery process.
Protecting Yourself from Crypto Recovery Scams: 5 Essential Strategies
Now, our primary focus is on equipping you with comprehensive strategies to safeguard against the intricate threats posed by these scams. As we navigate these guidelines, the emphasis is on practical steps that empower individuals to fortify their defenses in the ever-evolving landscape of cryptocurrency investments.
Thoroughly Verify Company Credentials
Prioritize the validation of company credentials before engaging with any crypto service. Cross-referencing information from official sources and regulatory bodies ensures legitimacy. Review the company's history to identify any red flags or negative indicators.
Exercise Caution with Unsolicited Communication
Maintain a vigilant stance against unsolicited communication, as legitimate recovery services rarely initiate contact unexpectedly. Scrutinize the language used in communications, and always verify official contact information to ensure the authenticity of the outreach.
Independently Verify Testimonials and References
Independently validate testimonials and references to establish the authenticity of a service's track record. Directly contact individuals or companies claiming to have benefited from the service and seek additional feedback from diverse sources.
Demand Transparent Legal Processes
Prioritize services that demonstrate transparency in their legal processes. Scrutinize any provided legal documentation and, when uncertain, consult with legal professionals to validate authenticity and legitimacy.
Question Unrealistic Promises
Approach services making extravagant promises with skepticism. Recognize that legitimate processes involve uncertainties; absolute guarantees may indicate fraudulent intent.
Tactics Employed by Crypto Recovery Scammers
We will provide a complete exploration of the methods used by scammers to exploit the vulnerabilities of their targets.
Social Engineering Techniques
- Trust Building: Scammers initiate contact with victims, often posing as experts or professionals in cryptocurrency recovery. They employ persuasive language to build trust, emphasizing their expertise and success stories.
- Emotional Manipulation: Exploiting the emotional distress of victims, scammers use stories of successful recoveries to evoke hope and trust.
Falsification of Credentials
- Fabricated Companies and Professionals: Perpetrators create fake companies or personas, complete with professional-looking websites and documents, to give an illusion of legitimacy.
- Falsified Testimonials: Scammers may fabricate positive testimonials from alleged clients, further reinforcing the credibility of their fraudulent operation.
Mimicking Legitimate Recovery Processes
- Imitation of Legal Procedures: Scammers claim to follow legal processes and procedures for fund recovery, creating a semblance of legitimacy.
- Fake Legal Documents: Scammers may provide forged legal documents, such as contracts and court orders, to deceive victims to support their false claims.
Exploiting Fear and Urgency
- False Threats: Scammers instill fear in victims by suggesting potential legal consequences or permanent loss of funds if immediate action is not taken.
- Imposing Strict Timelines: Scammers set tight payment deadlines to manipulate victims into quick decisions, creating a sense of urgency.
Continued Requests for Payments
- Escalating Demands: After an initial payment, scammers continue to request additional funds, citing unforeseen complications or escalating recovery costs.
- Threats of Abandonment: Perpetrators may threaten to abandon the recovery process unless further payments are made, coercing victims into compliance.
So, Can you Recover Stolen Crypto?
The prospect of recovering stolen cryptocurrency funds is a formidable challenge, fraught with complexities and uncertainties. A profound understanding of these intricacies is essential for individuals who find themselves victims of theft or scams.
Irreversibility of Blockchain Transactions
Cryptocurrency transactions, the backbone of blockchain technology, are irrevocable once confirmed. The decentralized nature of blockchain ensures that once a transaction is added to the ledger, it becomes practically impossible to alter or reverse. While this feature enhances the security of transactions, it poses a significant obstacle to recovering stolen funds.
Pseudonymity and Anonymity of Transactions
Cryptocurrency transactions operate under the veil of pseudonymity, allowing users to engage in financial transactions without revealing their real-world identities. This anonymity extends to legitimate users and malicious actors, making it an intricate challenge for authorities to trace and recover stolen funds with any semblance of efficiency.
Global Jurisdictional Challenges
The decentralized and borderless nature of cryptocurrencies presents a dilemma of jurisdictional challenges. Stolen funds can swiftly traverse international borders, navigating through multiple legal jurisdictions, thereby impeding the ability of law enforcement agencies to coordinate and collaborate effectively.
Limited Regulation and Legal Frameworks
The regulatory landscape for cryptocurrencies remains in a state of flux. The lack of standardized regulations globally hampers authorities' ability to pursue legal actions against perpetrators. Clear legal frameworks are necessary to ensure the avenues available for adequate recovery.
Sophistication of Cyber Criminals
The adversaries in cryptocurrency theft are often highly sophisticated and technologically adept. Employing advanced techniques such as tumblers and mixers, they obfuscate the origin of stolen funds, introducing layers of complexity to the already challenging process of tracking and tracing transactions.
Lack of Centralized Authorities
Unlike traditional financial systems, where centralized authorities wield the power to freeze or reverse transactions, cryptocurrencies operate on decentralized networks. The absence of a central authority capable of intervening in fraudulent transactions significantly reduces the potential avenues for recovery.
Limited Cooperation from Exchanges
While some cryptocurrency exchanges collaborate with law enforcement, others operate with varying degrees of anonymity and may not assist in tracking or freezing stolen funds. This lack of universal cooperation serves as a significant impediment to the overall recovery efforts.
Long-Term Nature of Investigations
Investigating and recovering stolen crypto funds is a protracted and intricate process. The complexity of tracing transactions and the need for collaboration among various entities extends the investigative phase, reducing the likelihood of timely and successful recovery.
Scarcity of Specialized Expertise
The intricate nature of cryptocurrency crimes demands specialized expertise. Unfortunately, there is a need for more professionals well-versed in blockchain technology and cybersecurity, hindering the efficiency of investigations and subsequent recovery attempts.
Educational Gaps Among Victims
Many victims of crypto theft lack awareness about the irreversible nature of transactions and the formidable challenges associated with recovery. Education gaps contribute to delays in reporting incidents and can significantly reduce the effectiveness of recovery attempts.
Recovering stolen cryptocurrency funds is a difficult challenge, marked by many complex factors. The irreversible nature of blockchain transactions, coupled with the pseudonymous and borderless features of cryptocurrencies, contributes to an environment where tracing and reclaiming stolen funds becomes arduous. The sophistication of cybercriminals, limited regulatory frameworks, and the absence of centralized authorities further compound the difficulties. While education and prevention remain crucial, acknowledging the formidable nature of recovery efforts underscores the importance of robust security measures from the outset to mitigate the risks associated with crypto theft.

Navigating Common Crypto Scams: A Comprehensive Guide
We will explore other common cryptocurrency scams that individuals may encounter in the dynamic and often treacherous crypto landscape. Understanding the tactics employed by scammers is paramount to safeguarding one's assets and navigating the crypto space with vigilance.
Phishing Scams
Phishing scams involve deceptive attempts to obtain sensitive information, such as private keys or login credentials, by posing as trustworthy entities. The scammers often use fake websites or emails, tricking users into unwittingly disclosing their valuable information.
Ponzi and Pyramid Schemes
Ponzi and pyramid schemes entice investors with promises of high returns, relying on funds from new investors to pay previous participants. These unsustainable models inevitably collapse, leaving most investors with significant losses.
Pump and Dump Schemes
In pump-and-dump schemes, manipulators artificially inflate the price of a cryptocurrency through misleading information and hype, only to sell their assets at the peak. This sudden sell-off causes a market crash, leading to substantial losses for unsuspecting investors.
ICO and Token Sale Frauds
Fraudulent initial coin offerings (ICOs) and token sales exploit the enthusiasm surrounding new cryptocurrencies. Scammers entice investors with promises of groundbreaking projects, only to disappear with the funds once the initial investment phase is complete.
Pumped-Up Token Sales
Fraudulent token sales involve artificially inflating the value of a cryptocurrency to create a false sense of demand. Investors, drawn in by the apparent success, purchase overvalued tokens that rapidly lose value once the manipulative practices cease.
Crypto Dust Attacks
In crypto dust attacks, scammers create fake wallets and send small amounts of cryptocurrency to users, tricking them into sending their funds to a fake similar address. Once sent with a wrong transaction, these funds are irretrievable, and the scammers vanish, leaving users with significant financial losses.
Malicious Software and Hacking
Crypto users are vulnerable to various types of malicious software, such as ransomware and keyloggers, that can compromise private keys or login credentials. Hacking incidents targeting exchanges and wallets are also prevalent, leading to direct financial losses.
Advanced Fee Frauds
Advanced fee scams involve convincing victims to pay upfront fees in exchange for promised returns or services. The scammers disappear once the fee is paid, leaving victims with empty promises and financial losses.
Token Swapping Scams
Token swapping scams involve tricking users into swapping their legitimate tokens for worthless or non-existent ones. These scams exploit users' trust and lack of thorough research into the assets they are exchanging.
Social Media Impersonation
Scammers often impersonate well-known crypto influencers like Brad Garlinghouse, companies, or crypto projects on social media platforms. They use these fake accounts to promote fake crypto giveaways or fraudulent investment opportunities, exploiting the trust of unsuspecting users.
Cloud Mining Scams
Cloud mining promises individuals the ability to mine cryptocurrencies without expensive hardware. However, many cloud mining operations are scams, with users paying for services that never deliver the promised returns.
Tech Support Scams
Tech support scams involve fraudulent individuals posing as customer support representatives of crypto exchanges or wallet providers. Victims are coerced into providing sensitive information, leading to unauthorized access and potential theft.
Understanding these common crypto scams is crucial for individuals navigating the cryptocurrency space.
The Imperative of Security in Cryptocurrencies
PlasBit believes cryptocurrency security is a key consideration in the ever-changing digital landscape. We will explore why security is essential in the cryptocurrency ecosystem and provide practical strategies for implementing effective protection measures against scams.
The Inherent Irreversibility of Blockchain Transactions
The crux of cryptocurrency security lies in understanding the irreversible nature of blockchain transactions. Once a transaction is recorded on the distributed ledger, it becomes immutable. While enhancing security, this feature underscores the importance of adopting preventive measures to avoid unwanted or fraudulent transactions.
The Centrality of Private Keys
Private keys, the gateway to cryptocurrency funds, are paramount for security. Safeguarding private keys with the utmost care, keeping them confidential, and storing them in secure environments is crucial to prevent unauthorized access to funds.
The Criticality of Strong and Unique Passwords
Adopting solid and unique passwords for cryptocurrency-related accounts is essential to prevent unauthorized access. Avoiding using the same passwords for different services and regularly updating them are fundamental practices.
The Use of Hardware Wallets and Cold Storage
Utilizing hardware wallets and cold storage (offline storage) are effective measures to protect cryptocurrencies from online risks. These solutions significantly reduce exposure to cyber-attacks and potential vulnerabilities of online platforms.
The Activation of Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security, requiring a second element beyond the password to access accounts. Activating 2FA helps defend against unauthorized access.
The Need to Update Software and Firmware
Keeping software and firmware up-to-date for both hardware wallets and exchange platforms is crucial to benefit from the latest security patches and improvements developers implement.
Vigilance Against Phishing and Social Engineering
Awareness of phishing and social engineering techniques is essential to recognize targeted attacks. Carefully verifying web addresses and communications and avoiding clicking on suspicious links significantly reduces the risk of falling into fraudulent traps.
The Adoption of Strict Privacy Policies
Maintaining stringent privacy policies is crucial to protect personal and financial information. Limiting the sharing of sensitive data and monitoring privacy settings on online platforms helps reduce opportunities for attackers.
Continuous Education and Skepticism Toward Too-Good-to-Be-True
Staying constantly informed about emerging threats and new scam tactics allows for continuous adaptation and reinforcement of security measures. Additionally, awareness of common scam types like crypto romance and zero transfer scams and maintaining a healthy skepticism toward overly enticing promises are essential to avoid financial losses.
Consulting Cybersecurity Professionals
Consulting cybersecurity experts or specialized consultants can be crucial for assessing and resolving security issues in complex situations or cases of suspected security compromise.
Defense Against Social Media Impersonation Attempts
Remaining vigilant against social media impersonation helps avoid falling for fraudulent giveaways or false investment proposals. Verifying the authenticity of accounts is a fundamental preventive practice.
Willingness to Report Suspicious Activity
Promptly reporting suspicious activity to relevant authorities and the cryptocurrency community contributes to a safer environment and can help halt the spread of fraud.
Investing time and effort in cryptocurrency security is a fundamental form of protection.
Don't Fall Victim of Crypto Scams!
At PlasBit, we believe that by implementing these strategies, individuals can significantly reduce the likelihood of falling victim to scams and maintain a more secure grasp on their digital assets. In conclusion, the prevalence of crypto recovery scams and crypto dusting attacks highlights the persistent and evolving challenges within the cryptocurrency ecosystem. The intricate nature of these scams, coupled with the often irreversible nature of blockchain transactions, underscores the importance of proactive measures and heightened vigilance among cryptocurrency users. As the crypto ecosystem matures, staying informed about emerging threats, implementing robust security practices, and fostering a collective awareness against fraudulent activities become paramount. The journey toward a secure and trustworthy digital financial ecosystem necessitates continuous education, adaptability, and a shared commitment to thwarting illicit activities.

 EN
EN









